“Zoom-bombing” Attacks during COVID-19: How can I protect myself?
The video conferencing software Zoom is enjoying enormous popularity because of the recent mass move to working from home. Unfortunately, concerns about the security of the tool have arisen. It was possible for uninvolved parties to join other people’s meetings and contribute unwanted or offensive content – the phenomenon was given the name of “Zoom-bombing.” In this blog post, the experts at Hornetsecurity have some tips on how to use Zoom safely.
In March 2020, Zoom reached 200 million users in one day
During the lockdown caused by the Coronavirus COVID-19 crisis, more and more businesses and people have begun using video conferencing tools, whether to assist them while working from home, teach online classes, see their family or friends, or even organize online parties. Thanks to this videoconference technology, these difficult days are being made a little easier. Can you imagine not being able to do videoconferences during this crisis—especially as a business?
For many patients who have been isolated away from their families, being connected via videoconference gives them the ability to see their relatives and not feel alone while recovering. Even if it is through the screen of a smartphone or tablet, feeling connected is what really matters to them during these trying times.
As a result of the current situation, Zoom reached 200 million users per day in March according to data provided by the company. This is a massive increase from December 2019, when the maximum number of participants per day in Zoom video calls was only 10 million.
New type of hijacking: “Zoom-bombing”
Unfortunately, cybercriminals have taken advantage of the coronavirus situation, and on March 30th the FBI alerted the public to the rise of hijacking cases via videoconference, also called “Zoom-bombing.” The FBI has received multiple reports of educational lectures interrupted by pornographic images and/or hate speech and threatening language.
The U.S. House of Representatives was the most recent victim of a “Zoom-bombing” cyberattack. The meeting was interrupted by uninvited attendees on at least three separate occasions—according to an internal letter to Carolyn Maloney (Republican Chairwoman of New York), chair of the Oversight and Reform Committee, which is the main investigative committee of the U.S. House of Representatives.
Also the INCIBE (National Cybersecurity Institute in Spain) reported a vulnerability affecting the Windows operating system that could allow a cybercriminal to steal the victim’s username and hash of the access password via Zoom. In addition, using the same vulnerability, the cybercriminal could run files and programs from the attacked computer. This applied to Windows users with versions earlier than 4.6.9.
Furthermore, it has been observed that phishing emails are being sent to users in the name of Zoom. These emails contain a fake Zoom notification inviting the recipient to an upcoming videoconference with their manager—in the hope that Zoom users will be misled to hurriedly enter their log-in data on a fake Zoom registration landing page. With the stolen credentials, hackers get access to the accounts and as well as the meeting IDs. They sell this information on the dark web or even give it away for free, so it can be used for “Zoom-bombing” attacks.
What can we do to prevent “Zoom-bombing”?
Users can already prevent the problem of “Zoom-bombing” by making the following adjustments in their Zoom settings:
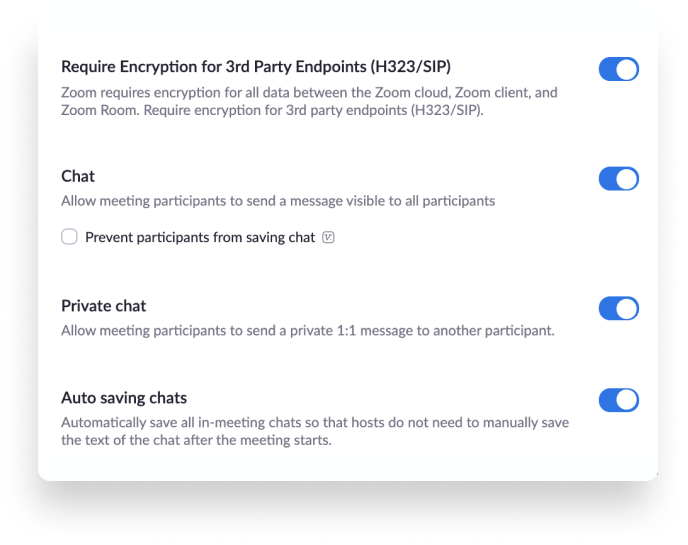
• Make sure the meeting is conducted using encryption*
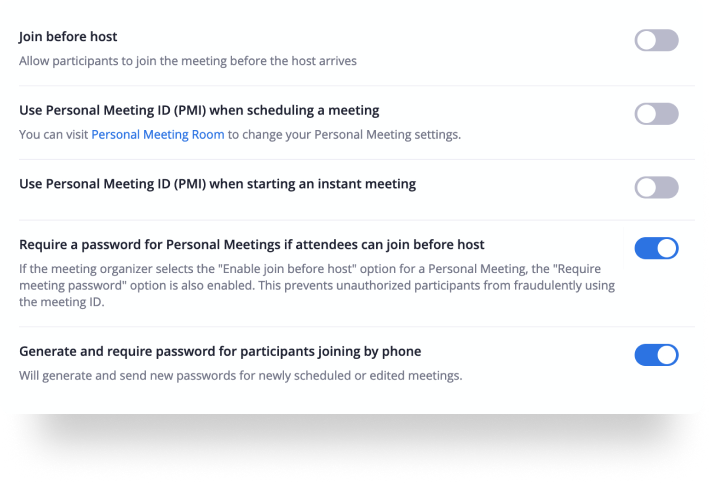
• Create waiting rooms for attendees
• Require the host to be present before the meeting begins
• Audio signatures
• Enable/Disable a participant or all participants to record
• Temporary pause to share the screen when a new window opens
• Protect the meeting with a password
* Chat Encryption Zoom uses both asymmetric and symmetric algorithms to encrypt the chat session. Session keys are generated with a device-unique hardware ID to avoid data being read from other devices.
Conclusion:
All these measures will help you prevent potential Zoom-bombing cyberattacks. However, special attention must be paid to email communication, as it is the most-attacked vector by cybercriminals—which has been demonstrated once again by the phishing emails for obtaining Zoom credentials.
One solution is Hornetsecurity’s Advanced Threat Protection service, which protects your email account from this kind of phishing cyberattack. It also uses innovative detection mechanisms: the latest technology of freezing, URL scanning, rewriting and sandboxing to keep hackers away from your Zoom credentials and all other sensitive data.
We can’t allow cybercriminals to take advantage of the current Coronavirus COVID19 crisis —whether via Zoom or any other teleconference video service—since it has now become a vital need to communicate with our colleagues, family and friends.
Sources
- FBI: https://www.fbi.gov/contact-us/field-offices/boston/news/press-releases/fbi-warns-of-teleconferencing-and-online-classroom-hijacking-during-covid-19-pandemic (published 30th March 2020)
- INCIBE: (National Spanish Institite of Cybersecurity): https://www.incibe.es/protege-tu-empresa/avisos-seguridad/vulnerabilidad-descubierta-el-sistema-videoconferencia-zoom (published 6th April 2020)
- FORTUNE: https://fortune.com/2020/04/02/zoom-bombing-what-is-meeting-hacked-how-to-prevent-vulnerability-is-zoom-safe-video-chats/ (published 4th April 2020)
- ZOOM: https://zoom.us/security
- BLOOMBERG: https://www.bloomberg.com/news/articles/2020-04-02/zoom-grapples-with-security-flaws-that-sour-some-users-on-app (published 2nd April 2020)
- BLOOMBERG: https://www.bloomberg.com/news/articles/2020-04-01/hackers-without-conscience-demand-ransom-from-health-providers (published 1st April 2020)
- TECHCRUNCH: https://techcrunch.com/2020/04/01/zoom-doom/ (published 1st April 2020)
- THREATPOST: https://threatpost.com/zoom-bombing-attack-hits-u-s-government-meeting/154903/ (published 17th April 2020)
- LETTER OF USA COMMITTEEi: https://www.documentcloud.org/documents/6839151-Letter-to-Chairwoman-Maloney-Re-Committee-Use-of.html (published 10th April 2020)
- BLEEPING COMPUTER: https://www.bleepingcomputer.com/news/security/phishing-uses-lay-off-zoom-meeting-alerts-to-steal-credentials/ (published 24th April 2020)
- FORBES: https://www.forbes.com/sites/leemathews/2020/04/28/new-phishing-attacks-prey-on-job-loss-fears-with-fake-zoom-meeting-invites/#6f1a33c94602 (published 28th April 2020)