

Mastering and Leveraging the MITRE ATT&CK Framework on Cyber Threat Detection
History of MITRE ATTACK Framework
The requirement to track and catalog typical TTPs (Tactics, Techniques, and Procedures) that APT (Advanced Persistent Threat) organizations used against business Windows networks was first addressed by MITRE in 2013. FMX (Fort Meade Experiment), an internal experiment, was where it all began.
In this project, a group of security experts was assigned to simulate adversarial TTPs against a network, and information was gathered from the attacks on this network. The information obtained was used to build the first components of the ATT&CK framework, as it is known today.
What Is in the MITRE ATT&CK Matrix?
MITRE ATT&CK matrix provides a systematic and structured flow of the threat actors’ tactics and techniques carried out in cyber attacks. This framework’s main purpose is to provide cybersecurity professionals insight into the different stages of an attack, how adversaries operate, and their next steps.
The ATT&CK framework has grown and expanded throughout the years. One notable expansion was that the framework focused solely on the Windows platform but expanded to other platforms, such as macOS and Linux, SaaS, Iaas Containers, and many more.
Each technique in the MITRE ATT&CK Matrix is documented with details on how it is executed, potential mitigations, and associated threat groups known to use it. The matrix is continuously updated to reflect the latest threat landscape and tactics employed by adversaries.
If you haven’t done so, navigate to the ATT&CK website.

MITRE ATT&CK Top Horizontal Matrix column describes Tactics, which start with Reconnaissance, Resource Development, Initial Access, and others. Each Tactic has a lot of techniques drawn from each of its vertical columns.
Based on MITRE’s presentation at a conference, the Technique in the table above is the result of hard work from various Adversary Groups over the past 10 years based on findings from cyber security researchers or threat intelligence reports.
Defining Retention Policies
MITRE ATT&CK currently has 14 tactics/categories that contain the techniques an adversary could use to perform the tactic. The categories cover the seven-stage Cyber Attack Lifecycle (credit Lockheed Martin for the Cyber Kill Chain, see below).
- Reconnaissance: Method used to gather intelligence for a target network, system or individual to identify potential vulnerabilities.
- Resource Development: Tactics used by adversaries to craft or acquire the resources necessary for their operations, such as tools, malware, or credentials.
- Initial Access: Tactic used to gain an initial foothold in a target environment.
- Execution: Tactic to run malicious code on a victim system.
- Persistence: Methods to maintain a presence on a compromised system.
- Privilege Escalation: Tactic to gain higher-level access and permissions.
- Defense Evasion: Methods to avoid detection and analysis by security tools.
- Credential Access: Tactic to steal or acquire user credentials.
- Discovery: Methods for gathering information about the target network.
- Lateral Movement: Tactics to move laterally within a network.
- Collection: Tactics for gathering data or valuable information.
- Command and Control: Tactics used by attackers to take over infiltrated computers, keep control over them, and communicate with their malicious software.
- Exfiltration: Tactics used to steal and transfer data outside the target environment.
- Impact: Tactics that cause damage or disruptions to systems or data.
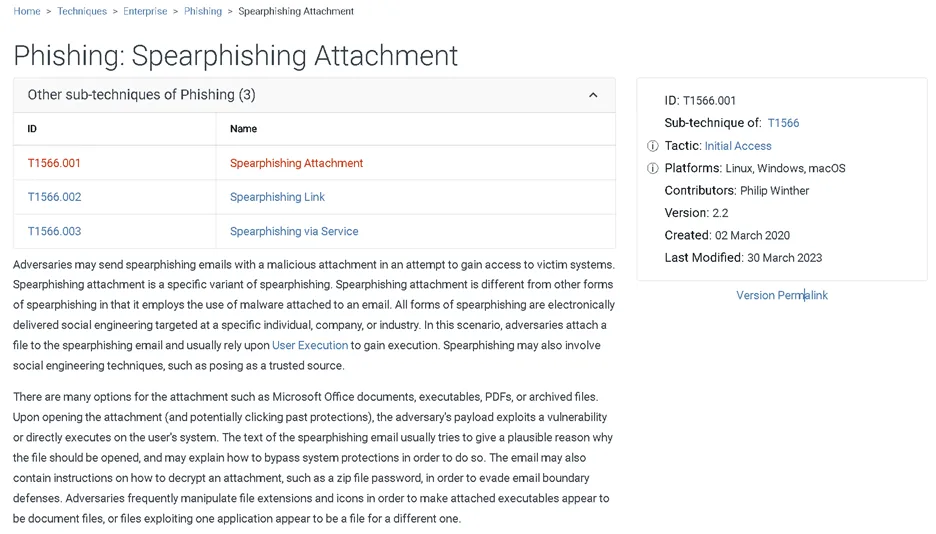
Under Initial Access, there are 9 techniques, and some of the techniques have sub-techniques, in this case 3:
- Spearphishing Attachment
- Spearphishing Link
- Spearphishing Via Service

On the other hand, “sub-techniques” such as Spearphishing Attachment are more precisely defined and subsets of the parent technique. They demonstrate several approaches or variations that adversaries may use to employ to achieve their goal. Read on about spear phishing examples.
Sub-techniques deliver greater clarity and insight into numerous strategies, enabling cybersecurity experts to comprehend the several paths adversaries could use to achieve the objective.
Adjusting RTOs, RPOs, and Retention Policies to Match Practical Restraints
Although the Cyber Kill Chain and MITRE ATT&CK are both popular frameworks in the cybersecurity field, they have different functions and take different methods of assessing and reducing cyber risks.
In contrast to MITRE ATT&CK, which focuses on understanding the “how” of an attack, describing the specific tactics, techniques, and procedures used by adversaries at various stages of the attack lifecycle, the Cyber Kill Chain framework originates from a military concept known as “kill chain,” which specifies the planning of an attack.
Identification of the target, deployment of troops, attack on the target, and eventual destruction of the target comprise it. However, “breaking” an adversary’s kill chain is a defensive or aggressive tactic.
The following steps make up the Cyber Kill Chain:
Reconnaissance
- Attackers assess potential vulnerabilities and weaknesses in the target system or organization.
Weaponization
- Attackers can turn the payload into a weapon by combining a harmful payload (such as malware) with a delivery method (such as a phishing email).
Delivery
- The weaponized payload is sent to the intended system or user, frequently through social engineering or other dubious methods.
Exploitation
- After the malicious payload is run, it exploits holes in the target’s defenses to gain a foothold in your organization
Installation
- Once inside the system, the attacker sets up backdoors or additional access points to create a persistent presence.
Installation
- The attacker establishes communication channels to keep hold of the compromised system and accept orders.
Actions on Objectives
- With full control established, the attacker carries out their primary objective, which could be data theft, system disruption, or other malicious activities.
Use Cases of the MITRE ATT&CK Matrix
As we dive deeper into technology and make our lives easier and more automated, the only downside is that risks are increasing proportionally. It is an ongoing battle that seems to never end, playing catch up with threat actors who use ransomware techniques to hijack critical data.
MITRE ATT&CK Matrix is continuously improving and staying up to date thanks to the security researchers, and several uses cases can be employed, depending on your company mission:
Incident Response
Supports comprehension of and reaction to online threats during investigations.
Threat intelligence
Examines the strategies and methods used by adversaries in reports.
Red Team testing
This technique simulates actual attacks to evaluate defenses.
Security awareness training
Security awareness training informs staff members about typical attack vectors.
Threat hunting
Threat hunting involves aggressively looking for signs of compromise.
Analysis of security
Analysis of security tool efficacy and coverage holes.
Threat sharing
Promotes the exchange of intelligence among peers.
Risk assessment
Finds gaps in defenses and strengthens them.
Security standards
Supports the observance of security standards.
Enhance employee awareness and safeguard critical data by leveraging Hornetsecurity’s Security Awareness Service for comprehensive cyber threat education and protection.
We work hard perpetually to give our customers confidence in their Spam & Malware Protection, Advanced Threat Protection, Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Conclusion
Despite cybersecurity frameworks like MITRE ATT&CK and the Cyber Kill Chain offering helpful perspectives into adversarial strategies and attack phases, they can be challenging for those without Security Awareness to understand because of their complexity and technical nature.
You can read more about Cybersecurity training here, after all, the humans are the ones navigating the ship.
FAQ
MITRE ATT&CK framework is a smart toolkit for digital investigators that reads like a spy manual, outlining the malicious schemes (tactics), nifty devices (techniques), and top-secret operations (procedures) employed by online criminals.
MITRE ATT&CK Matrix are the attack’s nuts and bolts, basically groups of approaches. Attackers use tactics to accomplish their stages or aims, whereas they use specific techniques (bolts) to carry them out.
For the past 40 years, MIT’s spin-off MITRE Attack has sought to strengthen cyber defenses with government funding. It is connected to several top-secret and commercial programs for numerous agencies.
One of the big benefits, and a large reason for it’s popularity, of the framework is that it provides a common language for defenders to communicate about different types of intrusions and attack types.
It promotes a threat-based defensive strategy with a balanced security posture and timely adoption of a cyber-attack response strategy by utilizing cyber threat intelligence. Nevertheless, given the quantity and variety of MITRE attack strategies, it is difficult for an organization to assess every MITRE attempt.
Because of this, MITRE Attack created the ATT&CK framework, an abbreviation for Adversarial Tactics, Techniques, and Common Knowledge, as a knowledge base.
