

Social Engineering
Definition, Examples & how to Protect Your employees
“There’s no technology today that can’t be overcome through social engineering.” (Kevin Mitnick, former hacker and social engineering expert)
Even with the best technical security precautions, every company has a risk factor that is difficult to control: the human one.
To get hold of important data or gain access, a hacker needs to understand not only computers but also people.
What exactly is social engineering, and how can you protect yourself? We will answer key questions about this in the article below.
What’s behind social engineering?
Social engineering is all about manipulating individuals on an interpersonal level. It involves the hacker trying to gain their victim’s trust and persuade them to reveal confidential information, for example, or to share credit card details and passwords.
The method is not something that only occurs on the Internet, but a scam tactic that has been used for many decades. One of the best-known ploys is the “grandparent” scam, where a fraudster telephones an elderly person and passes themselves off as a relative in desperate need of money (German police program for crime prevention, 2017).
Criminals also regularly use social engineering for financial gain through online dating services. A seemingly young, attractive woman will contact a man who is obviously looking for a new partner. The imposter plays their single-woman-in-love role well enough to win the victim’s trust in a relatively short time. Then the criminal asks the victim to help them with money for something like visiting their “new partner” – after which they often cut off contact.
Social engineering attacks on companies
If social hacking works in the private sphere, then businesses are the next target up for criminals – chiefly because there are often higher sums of money up for grabs here. Hackers follow much the same approach as with private individuals, although obtaining the information needed for a professional attack takes significantly more time. This makes the following information especially relevant for cybercriminals:
- Who is the head of the company (CEO) and which individuals are in leadership positions?
- Who is authorized to make bank transfers?
- When is the CEO on vacation or out of town for a work trip?
- What business activities are currently happening?
Hackers will usually target an employee who is authorized to carry out financial transactions, sending them an urgent message from a fake email address that looks like it has come from the boss.
Examples of Social Engineering:
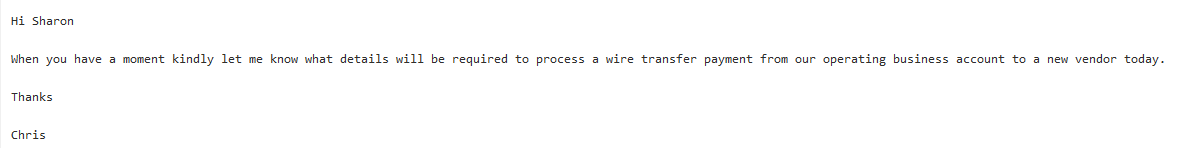
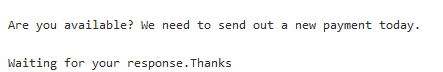
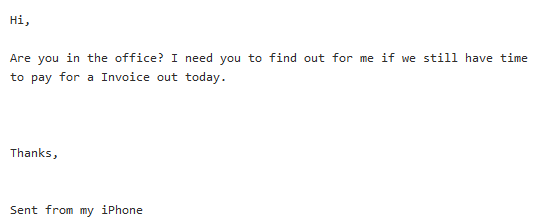
Due to the apparent urgency of the request, the email recipient then finds themselves rushing to follow their superior’s instructions without asking any significant questions. Once the data has been sent, the cybercriminal goes straight to work or money is transferred directly to the social hacker’s account. In 2016, large enterprises like Austrian aeronautics supplier FACC and Nuremberg-based cable manufacturer Leoni learned hard financial lessons about this modus operandi when they suffered losses of several million euros.
Phishing: the impersonal form of social engineering
A less laborious type of social engineering is the classic phishing email. This usually involves fake PayPal emails containing a link to a simulated website so much like the original that it is difficult to notice any deception. The email will ask people to update or verify their login details on this website, but doing so delivers the data directly into the hands of the scammers.
Unlike a personalized email, these messages are highly generic. The classic phishing email is based on a simple and less costly method, which means huge volumes of emails are sent. Even if only a fraction of the recipients fall for the ruse, hackers will have found the social engineering attack worthwhile..
Learn everything about phishing at our phishing page.
Social engineering needs no programming expertise
Technical obstacles are overcome simply by employing psychological tricks, with hackers exploiting people as the weakest link in the IT security chain. Even the most secure vault in the world can be opened if the access details are handed over to unauthorized individuals. This saves the criminal a great deal of technical effort and lessens the chance of them being detected by IT security measures.
If you had replied to the email from Felix above, the hacker would have infiltrated the company network within a few minutes. No effort, no programming skill, no great risk. Criminals leverage employees’ fundamental trust and curiosity in order to steal data or money.
How can I protect myself and my company against social engineering?
Organize preventive training sessions on a regular basis to educate yourself and your colleagues about the dangers of fake emails. Regular information emails can also help to raise awareness of the issue.
As long as criminals have not gained access to an employee’s or the CEO’s email account, there are several different ways to recognize fake emails:
- Verify the sender address: Check the sender address carefully. Is the email address really correct? Have any letters been swapped, maybe? Or an upper-case I replaced with a lower-case L? There will often be an automatically generated and untraceable second email address behind the first one. If you think an email is suspicious, you can take a closer look at the header. Information like the actual sender and the server that the message was sent from can all be found in an email’s header. In most cases, the sender is the clearest criterion for identifying a fraud attack.
- Check first hand: Contact colleagues directly if you’re unsure. Call the person in question or speak with them face to face.
- Rhetoric: With CEO fraud attacks especially, it is important not to let yourself be intimidated. Ask yourself whether the boss really wants to transfer €20,000 into an unknown account without anyone’s knowledge. Or consider whether your IT colleague Felix could in fact have noticed “unusual activity” and why that would make him require your login anyway. And even as a private individual – if you receive a surprising email from a company where you are a customer, it can help to make a brief call to their support team.
- Pay attention to spelling mistakes: Phishing emails, in particular, are full of misspelled words; from an incorrectly written name to sloppy language that suggests the text was not written by a native speaker but perhaps translated by automated language software.
- Don’t click on links directly: If the content of an email leaves you in any doubt, the best thing is not to click on any links inside it and instead to access the website concerned directly through your browser. For example, if Amazon asks you to update your details, then you should go directly to Amazon.com and look for a corresponding message there. If there is nothing to be found, you have likely received a phishing email.
- Hover over links: Before you open a link, mouse over it. With most browsers, a small window will open in the bottom left. This is the URL which will be accessed when the link is clicked. Checking the URL provides information about the true destination of the displayed web address.
Google phishing quiz: Your free awareness check
A few weeks ago, Google created a security quiz in response to the sharp growth in phishing attacks. This quiz challenges you to try and spot a phishing email. Can you see through any social engineering attack? Find out now!
Additional Protection with Hornetsecurity’s ATP
Classic phishing emails will generally be identified and weeded out immediately by a good spam filter. A personalized social engineering attack, however, is not much different from a perfectly ordinary email. These unwanted emails will therefore end up in your inbox in spite of spam filtering.
Advanced Threat Protection goes a step further: various deep filters and heuristic detection mechanisms will uncover almost any fake email. With the help of AI, the filter learns from every attack and thus improves its detection rate on a daily basis. Advanced Threat Protection covers many of the above points completely automatically.
Ultimately, though, you should always question every email and be cautious about sharing data.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to Social Engineering? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.


