The cybercriminals behind the banking Trojan Emotet are working hard to circumvent anti-virus filters with various tricks and spread the malware on many more systems. From email conversation thread hijacking, through changes of the web shells, to updating the Emotet-loader, which led to a huge increase in malware downloads. Now Emotet is again sending encrypted attachments via its malspam to further expand its botnet network.
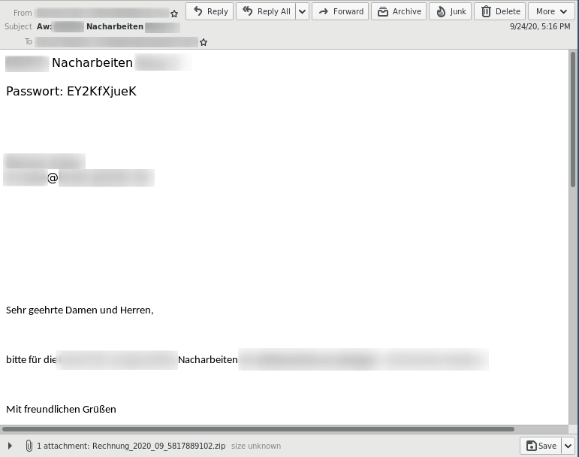
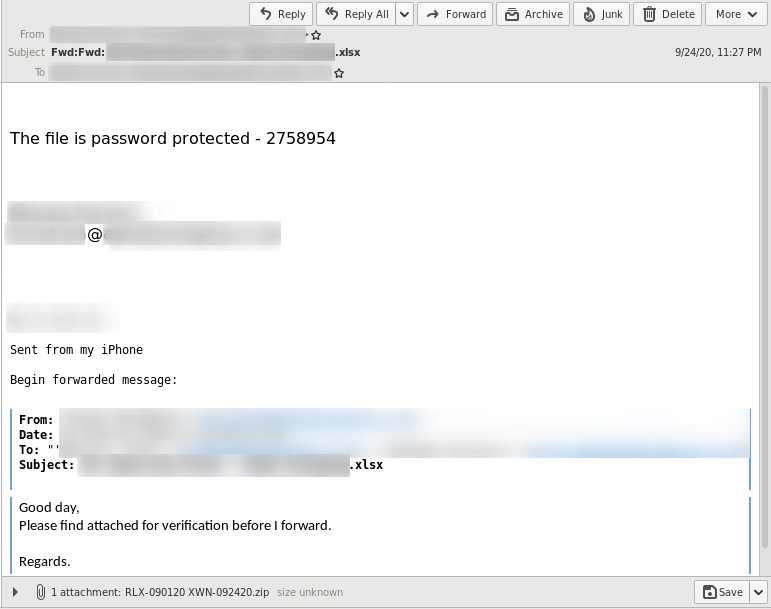
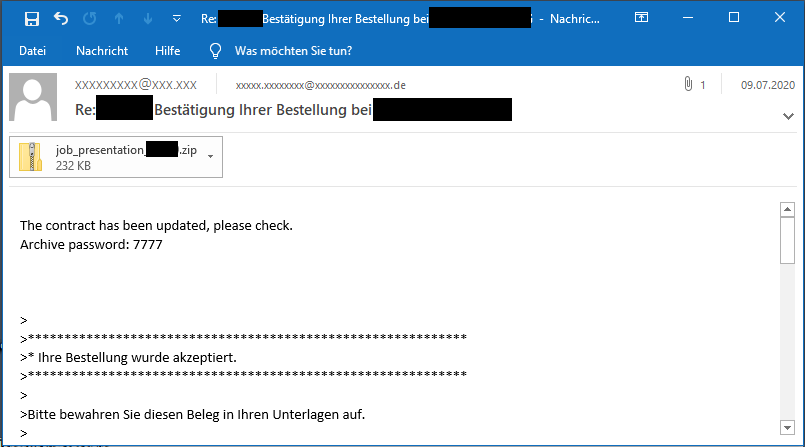
Since September, the Hornetsecurity Security Lab has observed a significant increase in Emotet malspam, which again sends encrypted archive files. The password for decrypting the file is included as plain text in the email message. By encrypting the attachment, conventional anti-virus programs are unable to detect and block the hidden malware. However, the victim can decrypt, open and execute the file, which eventually reloads the malware.
But this technique is not new: As early as April 2019, security analysts discovered the first waves of emotet malspam using encrypted zip files. Since then, such waves of spam have been appearing from time to time throughout the year and each wave lasts for a few days. The white-hat group “Cryptolaemus” calls this approach of the cybercriminals behind Emotet “Operation Zip Lock.” This team of over 20 security researchers and system administrators has set itself the mission of curbing the spread of “the most dangerous malware in the world.” Every day, the group publishes all updates of Emotet on their website and Twitter account. This enables system and network administrators to enter the so-called Indicators of compromise (IOCs)—including IP addresses for Emotet command servers, subject lines and file hashes of Emotet-infected files—into their security filters and thus protect themselves from possible Emotet infections.
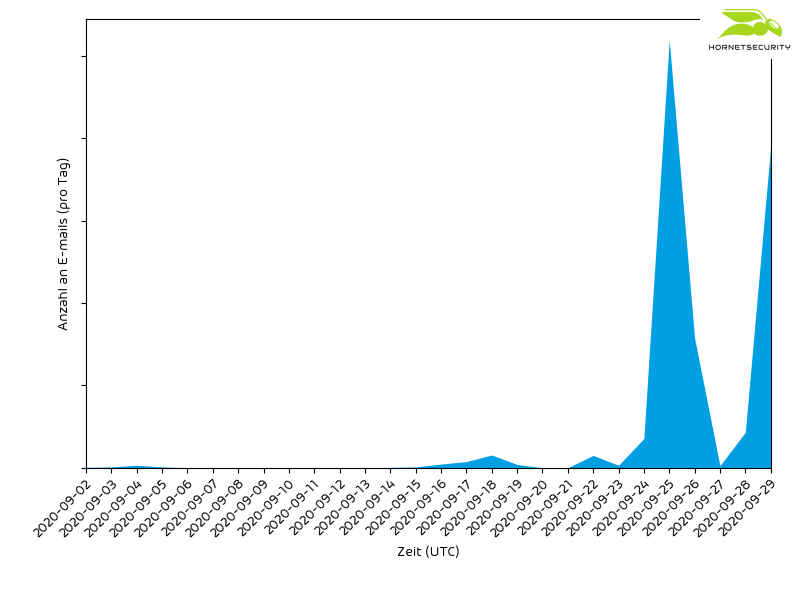
The current malspam wave with encrypted archives has been active since at least September 1st and was first aimed at Japanese-speaking regions.
The Hornetsecurity Security Lab reported waves of spam in Spanish, English and German starting around September 14th.
To increase the chance that a victim will actually open the malicious mail and activate the malware attachment when it arrives in the mailbox, cybercriminals make additional use of the “Email Conversation Thread Hijacking” technique. In doing so, the victim’s existing email conversation threads are used to make it appear more authentic. The attackers then reply to existing conversations that are stored in the target’s mailbox.
A popular cybercrime trend
In general, the email attack method of using encrypted attachments is quite popular among cybercriminal groups. For example, security analysts at Hornetsecurity discovered encrypted Office documents in GandCrab malware campaigns, and the malware Ursnif also spreads through encrypted zip attachments.
How can I protect myself against this?
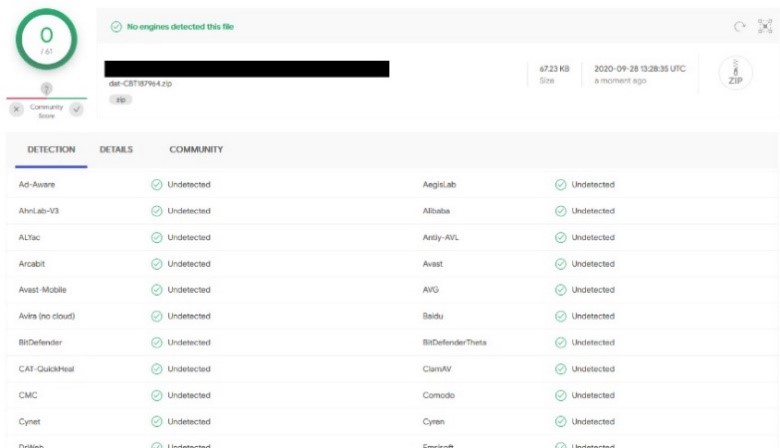
The encrypted Emotet files are still not detected by conventional antivirus programs, as shown by the malware scanner service VirusTotal.
The technique of Email Conversation Thread Hijacking also contributes to the success of cyber criminals, as it is almost impossible for recipients to detect such an attack, since the malicious emails are sent from a legitimate but compromised account.
However, in-depth filters and intelligent security mechanisms are able to detect both of these attack techniques and keep them out of the recipient’s mailbox.
The tactics of the cyber criminals behind Emotet make it clear that it is time for companies to take the next step in cybersecurity. After all, successful attacks serve to drive the ambitions of hackers and bring more cyber criminals onto the scene.
Further Information:
- Hornetsecuritys Advanced Threat Protection can analyze and identify these encrypted attachments thanks to the Malicious Document Decryption feature.