

Monthly Threat Report April 2024: Impersonation Attacks, and the US CSRB’s Report on Storm-0558
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of March 2024.
Executive Summary
- The amount of easily identifiable (and ultimately rejected) email threats has increased, while there has been a slight decrease in the amount of more targeted and sophisticated email-based threats
- The top file-types used for the spread of malicious payloads via email were Archive files, PDFs, and HTML files.
- Top targeted industries were Mining, Entertainment, Media, and Manufacturing
- Most impersonated brands for the month included DHL, Facebook, Docusign, as well as targeted campaigns involving some German entities such Strato and Targobank.
- The US Cyber Safety Review Board completed their report regarding the Microsoft Storm-0558 attack last year. the findings are not kind to Microsoft and calls on the industry to work together to help secure public cloud services.
- The US Federal Trade Commission has stated that impersonation attacks have cost victims 1.1 BILLION USD in 2023
- A potentially catastrophic supply chain attack in a widely used linux library looks that have been narrowly avoided
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for February 2024 compared to March 2024.
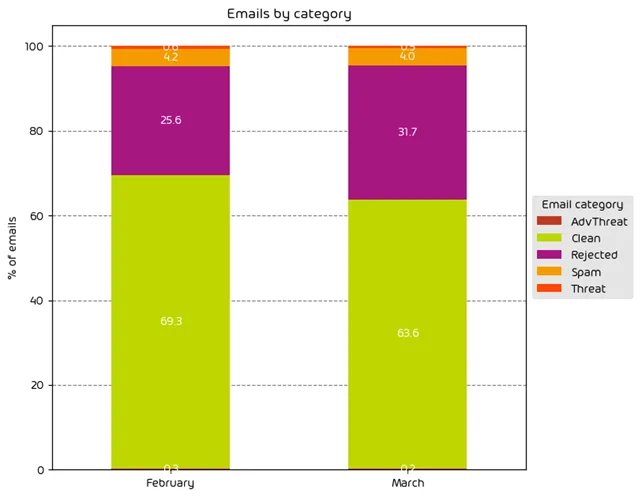
Our data for the past month shows that the amount of low effort, easily identifiable spam messages increased, while we noticed a decrease in more targeted attacks. This is indicated by the 6.1 percentage point increase in the amount of “rejected” messages, which is explained in the note below.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
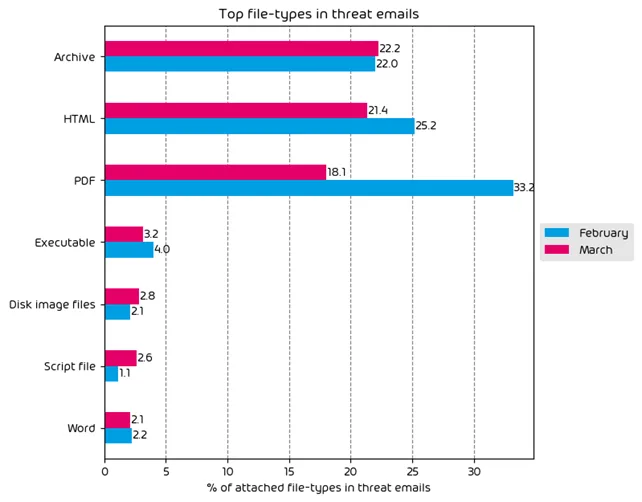
This month the top three most used file-types used in email attacks are Archive files, HTML, and PDFs. These three are commonly in the top spots largely due to the fact that they are platform agnostic and practically every OS on the planet can utilize these file types in some way. This has lead to their popularity among threat-actors. Also noted was an observed decrease in just about every file-type category. This was with the exception of small increases in three categories:
- Archive files (0.2 percentage point increase).
- Disk image files (0.7 percentage point increase).
- Script files (1.5 percentage point increase).
This data correlates with the data shown above where the amount of more advanced email attacks is currently down, and as a result, threat actors are currently less likely to attempt to attach malicious files to emails. That said, security teams should remain wary.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
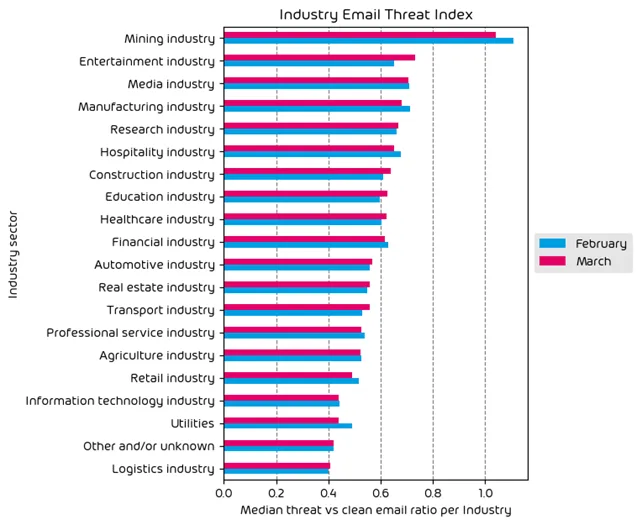
In terms of top targeted industries, we saw a mixture of increases/decreases across all tracked sectors with the Mining, Entertainment, and Media verticals being the top three offenders. You’ll see that even though the mining industry has had a noted decrease in targeting, it still remains in the top place by a large margin currently. Organizations falling in categories near the top of the list should be aware that they are more at risk of being targeted.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
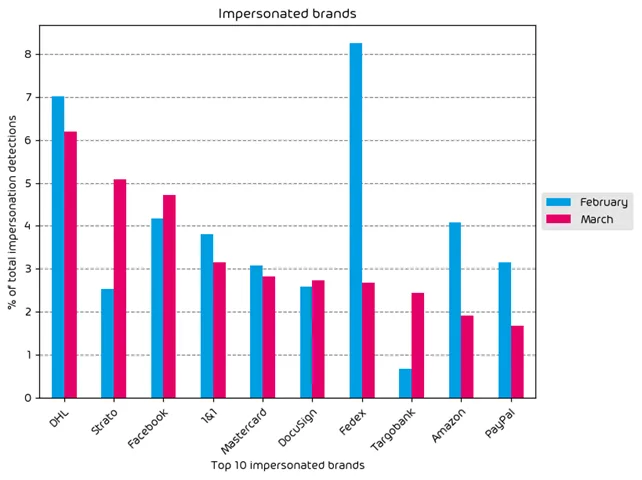
The top most impersonated brands during the data period are DHL, Strato (German Hosting Provider), and Facebook. We also observed clear campaigns involving impersonation of both Strato, and Targobank. Also of note, Facebook brand impersonation attempts have been on the rise in recent months. This is likely an attempt by certain threat actors to gain access to Facebook account credentials for use in password stuffing attacks or in an attempt to help spread disinformation, which is a common tactic we see during election years. The increase in Docusign brand impersonations is easily explainable due to the fact that it’s “tax season” in many countries, and as a result more people are expected to see Docusign emails on the regular. Threat actors know this, and are looking to capitalize on the expected increase in brand visibility.
Major Incidents and Industry Events
The US Cyber Safety Review Board Completes It’s Report on the Storm-0558 Breach
As we’ve covered extensively in these monthly reports and on The Security Swarm Podcast, the Storm-0558 breach was an attack on Microsoft Cloud services by Chinese Nation-State actors who were able to (somehow) get their hands on a consumer signing key, and then forge authentication tokens for access to cloud services. This attack has been heavily discussed in the industry, and Microsoft has been (seemingly) transparent about the attack chain and aftermath. This case was bad enough and led to direct impact on the US state department, which ultimately led to an investigation by the US Cyber Safety Review Board (CSRB).
The CSRB released their report on March 20th, and the news has been making the rounds in recent days. The report is extensive (34 pages). The report details the failings of Microsoft in this case, provides key findings, and provided a staggering 25 recommendations for how CSPs (Cloud Service Providers) should be prioritizing security over new features. The report clearly states:
Microsoft leadership should consider directing internal Microsoft teams to deprioritize feature developments across the company’s cloud infrastructure and product suite until substantial security improvements have been made. In all instances, security risks should be fully and appropriately assessed and addressed before new features are deployed.
This is a statement that echoes something we were discussing in a recent episode of The Security Swarm Podcast where Andy Syrewicze and Paul Schnackenburg questioned whether the industry’s current push towards innovation at all cost, is costing the larger IT community in safety. The CSRB also commented on another facet of this issue that was discussed on other episodes of the podcast – the importance of transparency from major CSPs. The report states:
The Board is troubled that Microsoft neglected to publicly correct this known error for many months. Customers (private sector and government) relied on these public representations in Microsoft’s blogs. The loss of a signing key is a serious problem, but the loss of a signing key through unknown means is far more significant because it means that the victim company does not know how its systems were infiltrated and whether the relevant vulnerabilities have been closed off. Left with the mistaken impression that Microsoft has conclusively identified the root cause of this incident, Microsoft’s customers did not have essential facts needed to make their own risk assessments about the security of Microsoft cloud environments in the wake of this intrusion.
This once again calls into question the current lack of transparency from major cloud providers where security is involved. This includes behaviors such as those outlined in the CSRB’s report as well as bad corporate practices such as late Friday night disclosures. It also highlights the critical need of independent third-party security vendors in the ecosystem to ensure that transparency is maintained at all levels of the ecosystem as well as the growing problem of single-vendor overdependence in the space.
We’ll be publishing a future podcast episode with more details on this topic.
Impersonation Scams top 1.1 Billion USD in Damage in 2023
As an industry we spend so much time discussing ransomware and supply-chain attacks that we often don’t spend as much time discussing other attack types, such as impersonation scams. In fact, According to the US Federal Trade Commission (FTC), “reported” impersonation scams topped 1.1 billion USD. This is a shocking statistic in and of itself, but pair that with this quote directly from the FTC:
In 2023, data from the FTC alone show more than 330,000 reports of business impersonation scams and nearly 160,000 reports of government impersonation scams. That amounts to nearly half the frauds reported directly to the agency.
Nearly HALF of the fraud reported to the agency in 2023 could be classified as impersonation scams. This trend is likely to continue in the coming years as new “Phishing Resistant” technologies like passkeys hit the mainstream causing passwords to be less of a target. Threat-actors can use impersonation scams for far more than just password and token theft. The can be used for social engineering, payment redirection scams, business email compromise, and more. This is certainly a problem that the industry will need to keep an eye on in the coming months and years.
Backdoor found in Open Source XZ Utils
The industry is always on the lookout for the next bad supply chain attack. A chance investigation by a Microsoft software engineer may have already thwarted it. CVE-2024-3094 is a malicious software injection in xz versions 5.6.0 and 5.6.1 that could potentially allow an attacker to break SSH authentication and gain unauthorized access to a target system. It has a CVSS Score of 10, and the issue impacts certain versions of Fedora Linux as well as some Debian (SID) distributions.
What’s so fascinating about this case is that it appears on the surface that someone maintained xz for a long period of time with the intent to eventually introduce a backdoor. The malicious code that is injected in this case appears to be difficult to reverse-engineer, but more information will undoubtedly come to light in the coming days.
Predictions for the Coming Months
- Financial and document verification (like docusign) services will continue to see an increase in brand impersonation attempts in the coming days. Once tax season is complete (particularly in the US), it’s likely that threat actors will pivot to other methods and brands.
- The industry will react to the CSRB’s report on the Storm-0558 breach, while the information could potentially drive policy change in the US government where cloud services are concerned.
- Given the recent findings with the XZ Utils supply chain attack, open source software will get more scrutiny than it has to date as we all become increasingly aware of how dependent we are FOSS.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on the CSRB’s report regarding Storm-0558:
As public cloud services (like Azure and M365) become more critical to the everyday lives of people around the world, we get closer to inevitable new regulations from governing bodies. In the CSRB’s report, one interesting thing that stands out is the board’s seeming admission that public cloud is deemed as “critical infrastructure”. With this designation comes increased scrutiny from governments and the eventual implementation of some much-needed regulation. In my opinion, some additional guardrails need to be put in place for public cloud where security is concerned, and the critical infrastructure designation indicates that the spectre of regulation on the technology sector is looming larger every day.
From Michael Posey, Lead Channel Sales Engineer, on Impersonation Attacks:
With the “CONSERVATIVE” estimate from the FTC of $1.1 Billion dollars lost to impersonation attacks in 2023, it continues to show that as IT professionals we need to be more diligent in protecting our users. While many will say that the end user is the weakest link, with proper security awareness training, testing, and education, they can also become your biggest asset in protecting your business. Along with proper education, helping to establish internal processes for leveraged BEC targets such as payment processes can also help to reinforce good behaviors that could be subject to many types of BEC/impersonation attacks.
Monthly Recommendations from the Hornetsecurity Security Lab
- March 31st was World Backup Day! If you haven’t checked in on your data protection plan lately, this is a good time to do so.
- If you use any of the affected linux distributions in your infrastructure, make sure they are not affected by the XZ utils vulnerability listed above.
- Take the time to educate your end-users on the dangers of impersonation attacks. A trusted security awareness training vendor can help with this!
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


