

Brand impersonation
What it is & how to defend against it
This article explains what brand impersonation is and gives real-world examples of phishing attacks on major brands such as Microsoft and PayPal. You’ll also learn important prevention strategies to help protect your business from this type of attack.
What is brand impersonation?
Brand impersonation is a type of email phishing attack where cybercriminals pose as a trusted brand to dupe victims and steal their data.
Also known as brand spoofing, this cyberattack uses an email that looks like it’s from a recognizable brand to trick recipients into clicking a link or downloading an attachment containing malware.
Some of the most impersonated brands include Facebook, Microsoft, Google, and PayPal.
- Visit our Blog for more information on the role of brand impersonation in email threats.
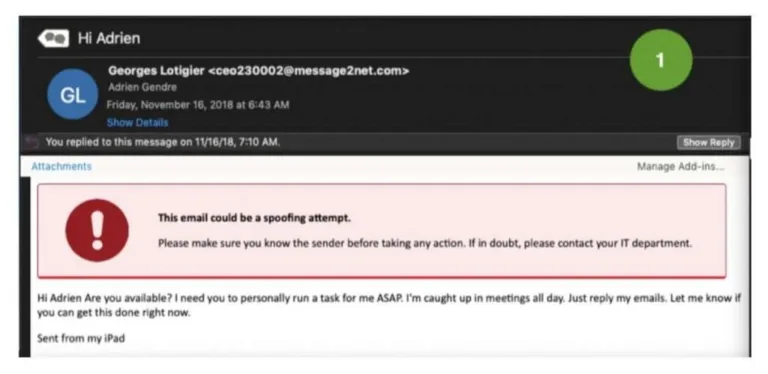
Examples of brand impersonation
With 11,041 unique phishing URLs, Microsoft is the top target for brand impersonation. The popularity of Microsoft 365 among SMBs and enterprises has made Microsoft a lucrative target for phishers hoping to steal valuable data from Microsoft 365 applications.
In 2022, financial services brands saw the most impersonation of any industry represented in the report. The financial services industry had a total of eight brands in the top 25. Cloud followed with six brands on the list. The E-commerce/logistics and telco industries each had four brands in the top 25, followed by social media with three.
How to prevent Brand Impersonation
For small to midsize businesses (SMBs), and particularly small businesses, the damage of brand impersonation could be unrecoverable.
Employee awareness and training are essential to ensure the best security at the office.
In addition, we recommend implementing an effective anti-spear phishing software that can automatically detect and block suspicious emails, so your employees are never put in a dangerous situation.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to brand impersonation? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.


