

Ransomware
What is ransomware?
How can you protect against it?
In this article, you’ll learn what ransomware is, how it differs from other malware, and how attackers use it to extort victims. We’ll also explore the most common ransomware variants, examine why the threat is growing, and share proven strategies for protection.
Table of Contents

What is ransomware?
Ransomware is a malicious program that is installed unnoticed on the PC of a stranger., which ensures that the computer is locked for the user, and can only be unlocked again by paying a ransom.
The difference of ransomware to normal malware, is that ransomware comes into direct contact with the user of the affected system. The malware encrypts either the files or the entire computer. The hacker has control over the computer, and demands a ransom. As long as the victim does not pay the ransom, the device stays encrypted.
If the infected device is in a network, such as in a company, the malware can spread to the entire network and encrypt all devices on that network. This can shut down entire companies, hospitals and universities.
A ransomware attack can cost businesses anywhere from a few hundred to several thousand dollars, and is one of the more common types of malware attacks. This range doesn’t account for the costliest aspects of being a ransomware victim, which may include downtime, data loss, compliance issues, customer churn, bad publicity, and legal consequences.

What is the difference between ransomware and malware?
Malware is the umbrella term for all programs that cause damage to a device. Both viruses and ransomware are therefore malware. Ransomware, is malware that spreads during activation and encrypts files in the infected computer network. The device is only decrypted by the hacker when a ransom is paid.
Is ransomware a virus?
No, ransomware is not a virus. Although viruses and ransomware are both malware, they are different. Viruses infect data and replicate themselves. Ransomware on the other hand encrypts files. For this reason, the name “cryptovirus” does not correlate exactly with the malware.
What is a Cryptolocker / Cryptotrojan?
A cryptolocker is part of the ransomware family. The goal is to get a ransom from the hacked victim. The cryptolocker infects the user’s documents and forces him to pay a ransom.
Ransomware attacks by cryptotrojans can have serious (financial) consequences for companies. Cryptotrojans have even threatened the existence of some companies, and driven them into bankruptcy in some cases. It is the horror scenario par excellence: An employee of a company catches a cryptotrojan on his work computer. It does not take long for the malware to spread across the entire company network.
How does ransomware work?
It usually starts with a classic phishing email that serves as bait to download an infected file. In most cases, the infection with the ransomware happens by an attempted PDF, DOC or XLS file. By opening the malicious file, the criminal has crossed the most significant hurdle. The installation on the respective system takes place. It should be mentioned that the installation can run independently of the activation of the ransomware. The ransomware attack can thus be prepared in advance, but for example can be started at a later time.
As soon as the ransomware is activated, the actual damage starts : the encryption process begins. Individual files on one system or even several systems within a company network can be encrypted. From now on, the user no longer has access to certain files or his entire computer. He has completely lost his admin rights. The control is in the hands of the hacker.
Once everything is encrypted, a notification appears on the victim’s screen. Here the hacker demands a ransom to remove the ransomware. Once this process is complete, the attackers only have to wait for the victim to pay the ransom. Linking the ransom demand to a deadline is an effective way for cybercriminals to increase the pressure on the victims. If the owners of the systems have not made a payment by the deadline, either the ransom demand will increase or the process of deleting data will begin.
Ransomware attacks can cause great damage, especially to companies. Experts and authorities usually advise against paying a ransom. Often the victims have no choice but to hope for the good-naturedness of the hackers after the payment. Often, the decryption after the payment of the ransom is not carried out.
What types of ransomware exist?
There are basically two different types of ransomware. Crypto ransomware encrypts files so that the user has no access to them. Locker ransomware excludes the user from his computer so that he cannot access it. There are also subtypes of these two variants. Scareware is fake software that finds errors and problems on the PC that do not exist. The software charges money to fix this problem. Scareware can also lock the computer (locker ransomware). Doxwareor also called Leakware extorts users with allegedly stolen data. Who does not pay, their data will be published, threatens the Leakware.
- Maze: A variant of ChaCha, Maze is often delivered through spam emails that contain malicious links or attachments, remote desktop protocol (RDP) attacks, or exploit kits.
- REvil (Sodinokibi): A strain of ransomware delivered through phishing emails, exploit kits, and server vulnerabilities. REvil is available as RaaS.
- Mailto (NetWalker): First detected in August 2019, this ransomware variant spreads via phishing and password-spraying campaigns.
- DarkSide: A variant responsible for the Colonial Pipeline attacks in May 2021, DarkSide is delivered through RDP brute force attacks and is available as RaaS.
- Ryuk: Ransomware that spreads initially through a phishing email and installs an exploit kit, often Trickbot or Emotet.
Get to know Emotet – A dangerous example of a ransomware attack
Emotet is one of the best known variations and even made it into the daily media coverage. Our Security Lab has taken a closer look at Emotet and examined it. In a detailed knowledge base page you will learn exactly how Emotet works:
How big is the danger of ransomware?
The danger is greater than one might think. Companies in particular should be on guard against infected emails. By 2018, cybercriminals had already stolen 8 billion euros. A considerable sum, but in 2019 even more was hijacked: The damage generated in 2019 has more than tripled compared to the previous year, of approximately 24 billion euros.
What is the reason for this rapid increase in successful ransomware attacks? Hackers have found the right niche. Sophisticated techniques and a little information about a company’s employees (social engineering) enable hackers to infect the IT infrastructure with a simple malicious email. Hospitals have been the most frequent victims of encryption attacks.
Risk of ransomware for companies
The danger for companies through ransomware is enormous. If a private computer is encrypted by ransomware this is annoying, but usually no reason for private insolvency. If a company computer is infected, this can lead to the companies bankruptcy. Often ransomware spreads throughout the entire network and infects all devices that are in this network. The result: entire companies can no longer operate. Files are lost, working time is lost, work cannot continue. In a 15-minute article, our IT expert Dr. Yvonne Bernard explains in detail how ransomware like Emotet can take a company apart and destroy it (The video is in german).
How Ransomware-as-a-service increased the relevance of ransomware attacks
Through a subscription model, hackers receive a kit with everything they need to launch an attack, including ransomware code and a decryption key. RaaS means low-skilled hackers can present significant threats to an organization’s cybersecurity.
How to protect against ransomware?
To protect against ransomware, companies should be proactive and develop a cybersecurity plan against malware. Since ransomware is very difficult to detect and fight, different protection mechanisms should be used. The most important protection is the training and sensitization of employees. Only those who know that ransomware exists and how it proceeds can detect such attacks.
Since the email inbox is one of the classic entry points for malware, a good spam filter should block or at least quarantine all executable attachments, zip files and MS Office document macros. Hornetsecurity offers a solution and filters out these dangers with the spam and virus filter before the mail can be delivered. The constant further development of the filters ensures that the increasingly professional means and methods of attack are counteracted.
With one of the highest detection rates on the market (99.99%), 18 different virus scanners check email traffic. A contaminated attachment, which has been packed several times and made unrecognizable, is recognized by the virus scanner of Hornetsecurity and categorized as spam.
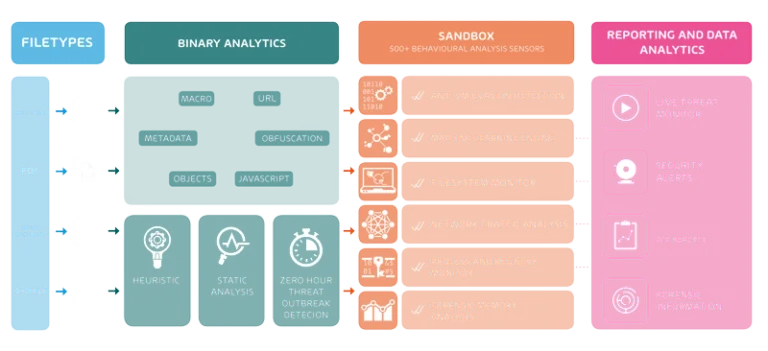
Advanced Threat Protection goes one step further and reliably detects ransomware attacks as well as various types of malware that are still unknown. Hornetsecurity Advanced Threat Protection (ATP) offers solutions on a broad basis. These include URL rewriting and URL scanning.
If an attack is successful, it is important to have up-to-date backups available. In this way an older version without infection can be uploaded. This keeps data loss as low as possible. The backup can be done manually or automatically. A cloud solution for companies would be a great possibility for data backup.
For ransomware attacks the email is primarily used. Well camouflaged, emails get to the computer of the employee in the target company as PDF, EXE or JPEG files. The display of file extensions is deactivated by default in most email clients, which is why the user usually cannot recognize the format of the file at first glance.
Unintentionally, the infected files are opened and the ransomware is executed. Therefore, it is important that you enable the viewing of file extensions in your email client settings.
Closing vulnerabilities is also very important. Microsoft’s Remote Desktop protocol is often used as a vulnerability. This feature allows ransomware to spread within the local network in individual cases. This way the malware distributes itself in the network within a very short time. Updating the systems is also absolutely necessary. The older the software, the more entry points are known and available. If you are still using Windows 7 or even Windows XP today, you should not be surprised if your computer is infected and encrypted. So WannaCry used a gap in outdated Windows systems (EternalBlue). It was simply ignored by many companies. Updates or patches were not applied. This resulted in a large number of successful ransomware attacks on companies.
Are ransomware scanners available?
If the ransomware is already on the computer, it is usually already too late. If the ransomware has not yet been activated, an up-to-date anti-virus program will help. However, the most sensible solutions are those that detect ransomware before it reaches the computer. This is also where classic virus scanners, such as GDATA, which take action against all types of malware, help. However, if it is a question of protection against infected emails, an extended spam filter should be used. Here, for example, an anti-ransomware scanner such as the cloud solution Advanced Threat Protection from Hornetsecurity can help.
Hornetsecurity’s ATP protects against attacks with ransomware such as Locky, Tesla or Petya, filters out phishing mails and fends off so-called blended threats. To achieve this, ATP uses various detection mechanisms: In addition to a sandbox, URL rewriting and URL scanning are also used. Freezing, i.e. the “freezing” of suspicious e-mails, is also part of Hornetsecurity’s ATP.
How to remove Ransomware?
Once the ransomware is on the computer and has infected it, there is usually no good way out. Either you pay the ransom (the police advise against it) or you set up the computer new (with the hope of an up-to-date backup). For some attacks, however, there are decryption tools. Just visit the site https://www.nomoreransom.org/crypto-sheriff.php?lang=en for this. No More Ransom provides decryption for over 50 different ransomware types.
Should I pay the ransom for a ransomware attack?
No, experts and investigating authorities advise against paying the ransom. Often the data is not decrypted despite payment and the computer is still not usable. Therefore, anti-ransomware solutions should rather be used and preventive measures should be taken so that paying ransom does not become an option in the first place.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to ransomware? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.


