

Monthly Threat Report November 2023: Holiday Email Threat Increases and More Zero-Days
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from October.
Executive Summary
- Spam messages are slightly up over the data period, while those emails classified as “Threats” and “AdvThreats” are slightly down. That said, the state of email security risks in the industry remains high.
- The use of PDF files to deliver malicious payloads via email has risen over the last month. This is likely driven by post-QakBot botnets such as DarkGate.
- The research industry has seen the most significant increase in attack targeting over the data period and is number one on our list of most targeted industries. The mining and entertainment verticals were second and third place, respectively.
- Shipping and Finance brands have seen increases in brand impersonation attempts over the last month. This trend will continue due to the upcoming holiday shopping months.
- Microsoft has started to roll out the promised logging changes in response to the cloud services attack by Storm-0558.
- A significant vulnerability in Citrix NetScalers dubbed CitrixBleed has the industry scrambling to apply patches. The vulnerability has been exploited in the wild since at least August, according to Mandiant.
- The Security and Exchange Commission has brought charges against SolarWinds and their CISO for fraud and security lapses regarding the late 2020 SunBurst incident.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for October 2023 compared to September 2023.
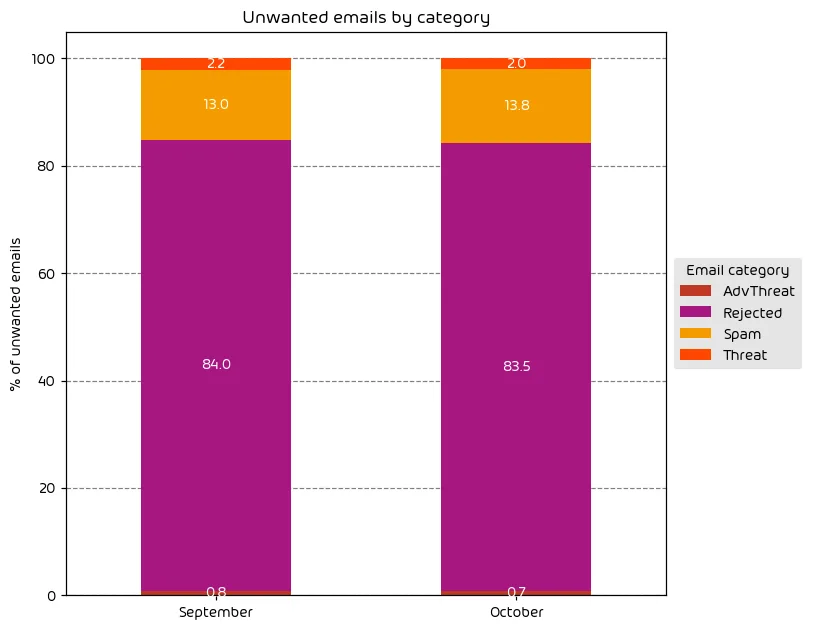
October saw a slight increase in the number of emails classified as “spam,” while “threats” and “AdvThreats” were down slightly. As we stated in last month’s report, the overall email threat landscape remains dangerous, with a high volume of current threats that will likely persist for some time, especially as we move into the holiday months.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
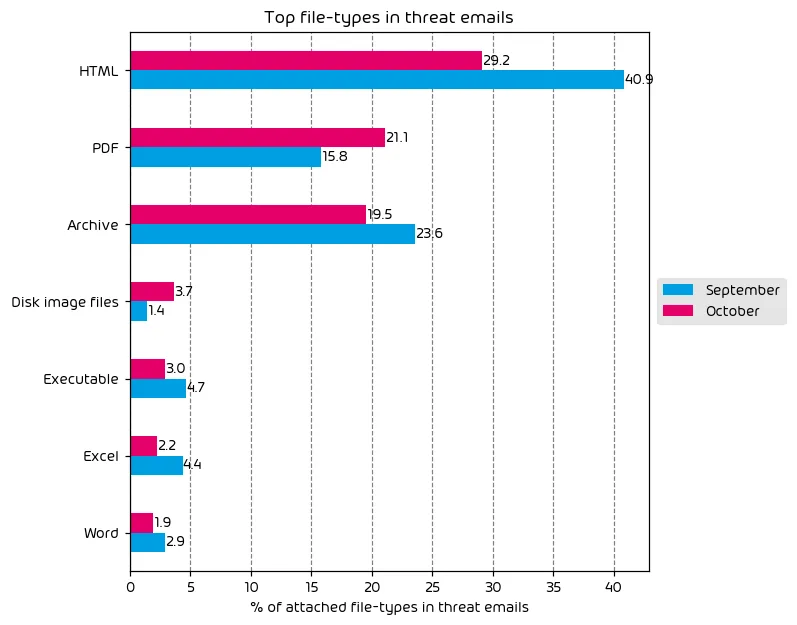
The usage of HTML and Archive files is down over the data period, while the use of PDF and disk images is up. One reason for the suspected increase in PDF files is the fact that they are the preferred delivery mechanism for some of the newer (post-Qakbot) botnets such as DarkGate. While the vector of attack for DarkGate has pivoted somewhat towards instant messaging, the attacks can also be seen via email.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
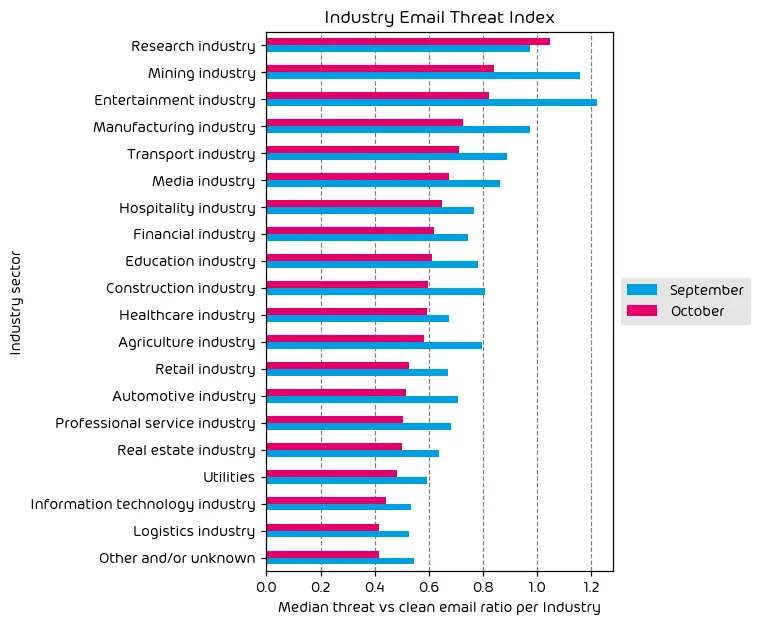
During this data period, we have observed a net decrease in threat indices across all industries except for the research vertical. The research industry remains at (or near) the top of the list for this month’s report. According to our data, this industry has seen a consistent threat landscape for some time and is frequently in the top 3 targeted industry sectors. This is mainly due to the fact that research organizations are often working with sensitive intellectual property and supporting data, making them ripe targets for threat actors who can not only attempt to ransomware the organization but also threaten to release said data to the public via double extortion attacks.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
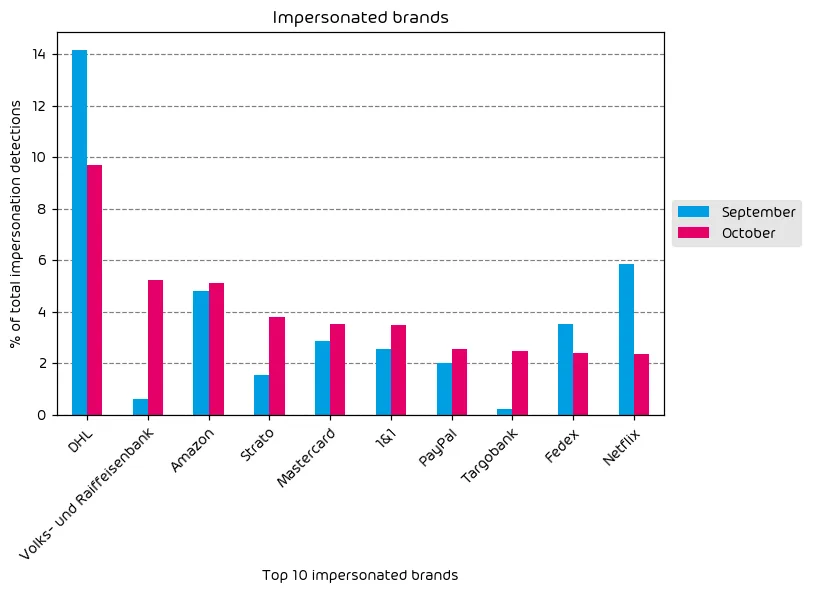
Shipping and finance brands continue to top our list of most impersonated brands for this month’s report. Even though the number of DHL brand impersonations is down, the global shipping vendor remains at the top of the list. Amazon, Mastercard, and PayPal also saw noted increases. Another trend we have observed this month is a significant increase in brand impersonation attempts for several German banks. Increases for shipping and finance organizations are not uncommon this time of year as many threat actors will try to capitalize on the holiday shopping season and attempt to sneak into end-users inboxes, posing as one of these organizations.
Major Incidents and Industry Events
Update on Storm-0558
Thankfully, there has been no further negative news surrounding the Storm-0558 breach that occurred earlier this year. For those who are unaware, Storm-0558 is the designation that Microsoft gave to a group of nation-state threat actors that managed to procure a Microsoft consumer signing key. The group then used that signing key to forge authentication tokens to gain access to Microsoft cloud services. We have covered this breach extensively through these monthly reports since the news broke.
That all said, Microsoft has made a new announcement regarding this case in that they confirmed they’ve begun to roll out some of the promised logging changes they had mentioned while they are postmortem analysis of the breach. Microsoft did not even detect the Storm-0558 breach. The US State Department is the entity that brought the breach to Microsoft’s attention, and this is ONLY because the State Dept. had the premium logging capabilities licensed and enabled for the applicable cloud services.
This was a HUGE point of criticism against Microsoft, as many security experts in the industry pointed out that adequate logging should not be placed behind a paywall of any kind. Thankfully, Microsoft has taken this criticism seriously and has started rolling out these logging capabilities as promised. Said changes included extended default retention policies, additional capabilities, and more. While this change is welcome and does help, the question of over-reliance on Microsoft for security continues to be asked in the security community. We’ll continue to provide updates on this case as new developments occur.
CitrixBleed
October 10th saw the industry add another major zero-day flaw to the list for 2023, this time from Citrix. CVE-2023-4966 (known as CitrixBleed) is a flaw in Citrix NetScaler devices and has seen exploitation in the wild since August, as reported by Mandiant. This vulnerability allows attackers to force the system to return system memory via a specially crafted HTTP GET message. The memory dump contains post-authentication session tokens that the attacker can use to log in to the device while bypassing MFA. Once an attacker gains access to the system, the goal is often lateral movement, privilege escalation, persistence, and data exfiltration. Thankfully, Citrix has released a patch, urges customers to install it ASAP, and also recommends taking the extra step to kill all existing sessions as outlined in their official notice.
This vulnerability is a stark reminder to the industry that comprehensive security involves more than just endpoints, servers, and cloud services. Network devices, IoT devices, and those often after-thoughts components can be easy stepping stones for threat actors to use to access critical data. If you still need to make a plan for patching these types of devices in your environment, make sure you get them on your schedule ASAP.
SEC Repercussions for SolarWinds
Even though not directly technical, the next item on this month’s list has some serious implications for the security industry. It’s been clear for some time now that various governments and business regulatory bodies have begun losing patience with the increase in security lapses in recent years. This can be seen, for example, in Australia, where steep fines are now levied against organizations that do not take relevant steps to provide proper cybersecurity. Or, another example is the Department of Homeland Security’s Cyber Safety Review Board investigation of the recent Microsoft Cloud issues.
The latest example of this comes from the US Securities and Exchange Commission (SEC), and it targets SolarWinds, and it’s Sunburst vulnerabilities from late 2020 specifically. While SunBurst is old news in the security space, the SEC has taken the unprecedented step of charging SolarWinds and their CISO with “Fraud and Cybersecurity Failures”. This can be seen as a clear escalation by governing bodies and agencies and would mark one of the first times that actual charges are being filed regarding alleged security negligence against an organization AND (more shockingly) a specific officer within said organization. Despite the charges being valid or not, many see this as a step too far, and some fear that this will keep talented and competent security professionals from stepping into the CISO role for fear of legal risk. It’s still early days regarding this case. Still, the security community is watching, and we’ll continue to monitor this in future reports as the impact on the security community could be significant.
Vulnerability in Curl
Thankfully, it has been found that making use of the exploit for a recently discovered curl vulnerability is quite difficult. That said, we felt it was worth mentioning the disclosed curl vulnerabilities here due to the vastness of those impacted. For those who are unaware, curl is a commonly used system utility for transferring data using a variety of protocols. It’s present in most operating systems, including Windows, MacOS, and Linux. Due to that fact, this vulnerability has a large potential blast radius.
The vulnerability is being tracked under two CVEs – CVE-2023-38545 and CVE-2023-38546. Those impacted organizations should apply the needed patches applicable to your operating system.
Predictions for the Coming Months
The Holidays Will Drive an Increase in Malicious Emails
The holidays bring an increase in shipping, family communication, and financial transactions during November and December every year. Threat actors know this and will seek to hide malicious emails amongst that holiday communication. This will take the form of brand impersonation emails (particularly that of shipping companies), financial scams, charity fraud, and others.
We’ll Start to See the Industry Fallout from the CitrixBleed Vulnerability
Like other large-scale attacks impacting a large number of enterprise customers, we won’t know the extent of the damage for some time. The fact that this vulnerability was actively being exploited for a month or more before disclosure means that many organizations may have been impacted and not yet know it. With the vulnerability publicly known now, the race is on for IT teams to get mitigations into place before threat actors can target them. The extent of the damage is likely to start making some small ripples in the news in the coming days.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Umut Alemdar, Head of Security Lab, on the SEC’s actions against cybersecurity failures and the holiday season:
The SEC’s actions against cybersecurity failures mark a significant shift in regulatory oversight. This development should prompt organizations to reassess their compliance and cybersecurity frameworks, ensuring they align with evolving legal and ethical standards. I am excited to see how company boards will adapt and enhance their governance structures in response to these regulatory changes. As we approach the holiday season, a predicted spike in malicious emails necessitates a heightened state of alertness. This is an excellent time for CISOs and security teams to reinforce security training, update phishing response protocols, and ensure that all systems are adequately protected against the latest threat vectors. Stay safe!
From Andy Syrewicze, Security Evangelist, on the security of network appliances:
The recent Citrix NetScaler vulnerabilities are a good reminder for all organizations to re-evaluate their security posture and patching strategies. I’ve sadly seen it happen too many times where an organization will make great efforts to secure their servers, endpoints, and cloud services while switches, routers, and network appliances go years without firmware updates or patching. This goes for IoT devices as well. Any connected system is a potential foothold for an adversary, and businesses will only have a holistic security posture once ALL connected devices are taken into consideration.
Monthly Recommendations
- Be aware of holiday spam and email scams and communicate the likely increase in malicious traffic to your end users. Also, consider investing in a trusted security awareness service to help educate your end users on these dangers.
- Take advantage of new logging offered by Microsoft. As we discussed earlier in the report, Microsoft is offering some additional logging capabilities for cloud services. The extra visibility can help organizations keep an eye on their environments and is crucial to spotting anything out of the ordinary.
- Apply Citrix NetScaler Patches and apply the proper mitigations if applicable to your organization.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


