

Monthly Threat Report October 2023
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of September 2023.
Executive Summary
- Email threats remained nearly the same as the previous month throughout the data period at an alarming level.
- HTML file usage for delivery of malicious payloads is down, while PDF and archive usage is up. All common operating systems support these file types. Hence, attackers continue to arm them with malicious intent.
- The Entertainment and Mining industries remain the two most targeted industries over the last 30 days.
- There has been a notable increase in brand impersonation phishing emails over the data period, with marked increases for the Netflix, FedEx, DocuSign, and T-Mobile brands.
- Microsoft continues to experience security incidents, which questions its security culture.
- A critical vulnerability in the libwebp library that encodes and decodes WebP images has prompted many affected applications to rush out patches. We predict that threat actors will rush to capitalize on this.
- We predict we will continue to see a trickle of information regarding the Storm-0558 breach due to US Government investigations. Recent reports highlight that threat actors managed to exfiltrate around 60,000 emails from 10 State Department accounts.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for September 2023 compared to August 2023.
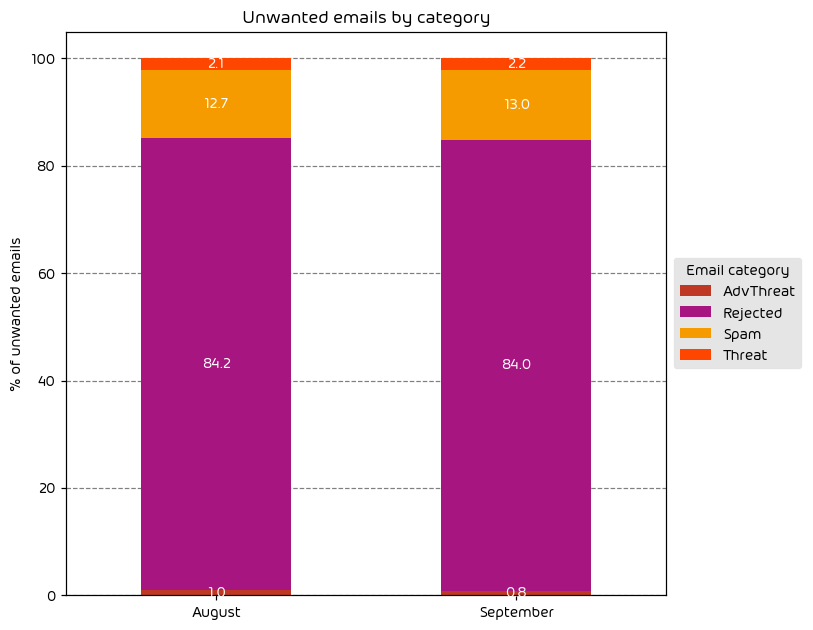
The change in the amount of unwanted emails by category was nearly negligible for the data period. We saw a SLIGHT increase in the amount of threats and advanced threats but nothing noteworthy.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
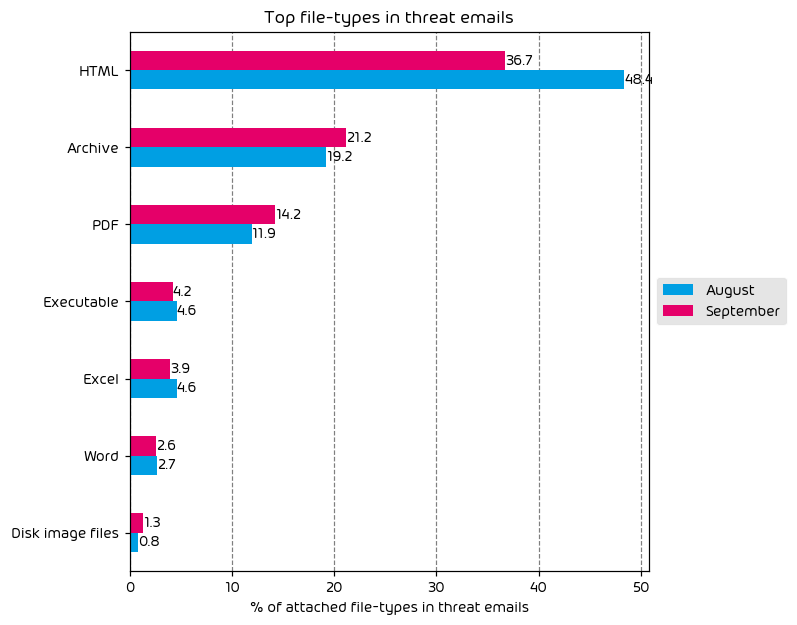
Top File Types in Email Attacks
- Archive and PDF usage is up
- HTML file usage is down
This month saw an increase in the usage of PDF files to deliver malicious payloads. One common malicious payload we have seen via this method during the data period is the DarkGate Malware. We suspect several threat actors that were previously shipping Qakbot via malicious PDFs have shifted to the DarkGate Malware instead, and we now see more malicious PDF files.
If you would like to read more of our commentary on the results of last month’s disruption of the Qakbot botnet, please see the report from the previous month.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
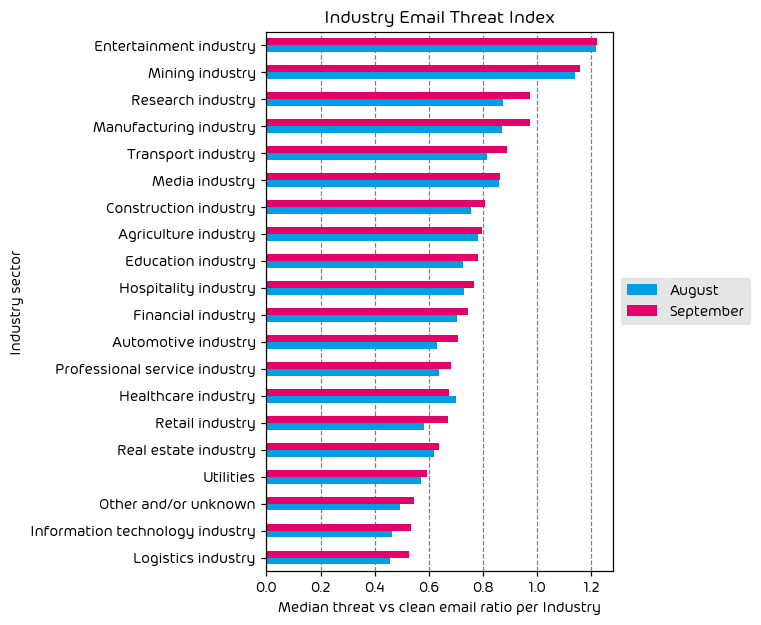
Overall, we observed a slight net increase in threats across most industries during the defined data period for this report. This correlates with the slight increase in threats, as discussed earlier in the report.
The top targeted industries continue to be the entertainment and mining sectors – the same as last month. That said, there was a noticeable increase in email threats levied at the research and manufacturing verticals. This is a trend we will continue to watch in the coming days.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
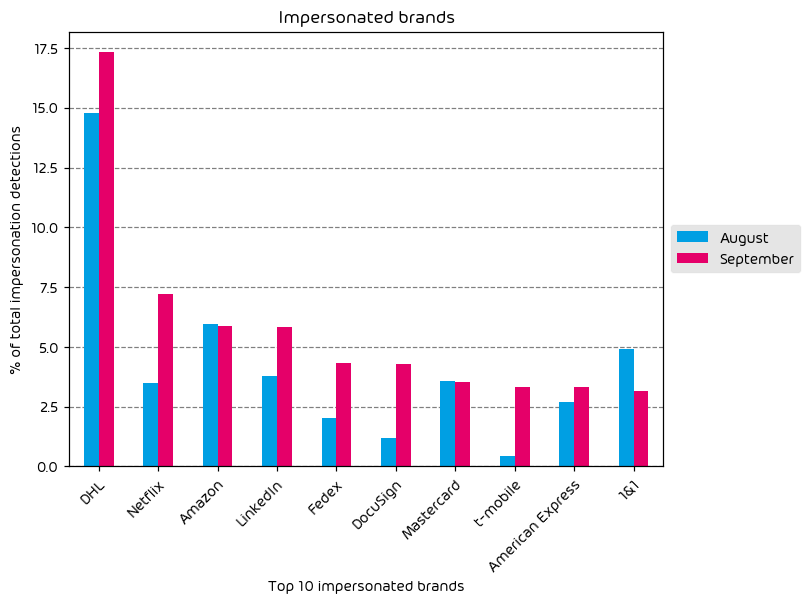
We observed major increases in brand impersonation attempts throughout the data period of this report. While DHL remains the most impersonated brand by a large margin, Netflix, DocuSign, LinkedIn, FedEx, and T-Mobile all saw significant increases over the previous month.
Continued Impersonation of Shipping Organizations
As we have reported during the previous two months, it is common to see shipping organizations near the top of the impersonated list simply because package shipment is quite common in our post-COVID world. If attackers can land a phishing message about your “pending package delivery” in your inbox at the right moment, you have a greater chance of interacting with it.
Significant Increase in T-Mobile Brand Impersonation Attempts
One possible reason for the T-Mobile increase could be attributed to yet another potential data leak from the US Telecom organization in that an application “glitch” allowed users to see the account details of multiple accounts, not just their own. It is common to see threat actors use information from such situations.
Variations of DocuSign Impersonation Phishing Emails
Also worth noting when it comes to recent DocuSign phishing messages is that some threat actors have fallen back to simply embedding a link behind images in their brand impersonation emails, as shown below:
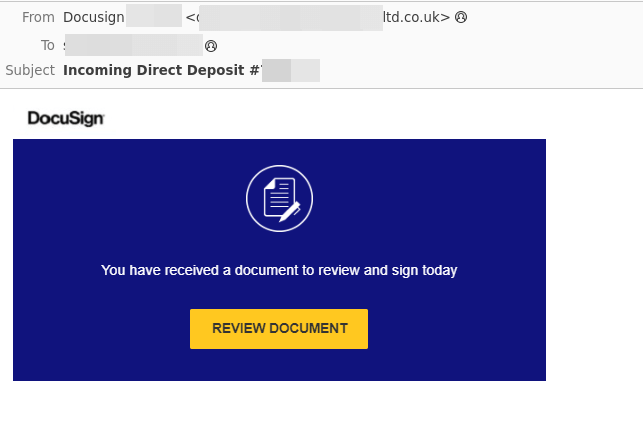
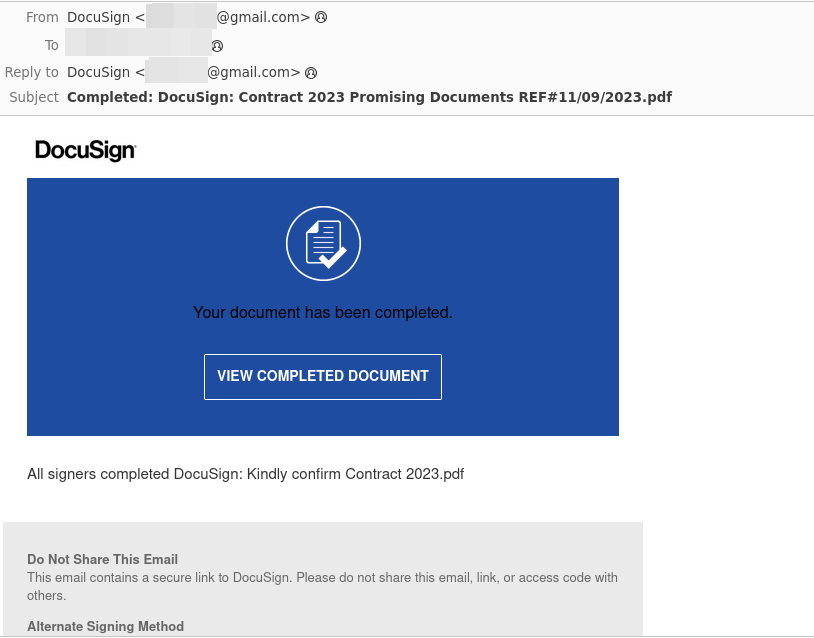
That said, we continue to see the traditional method of brand impersonation attempts as DocuSign, where the attacker uses HTML to piece together the phishing email more accurately:
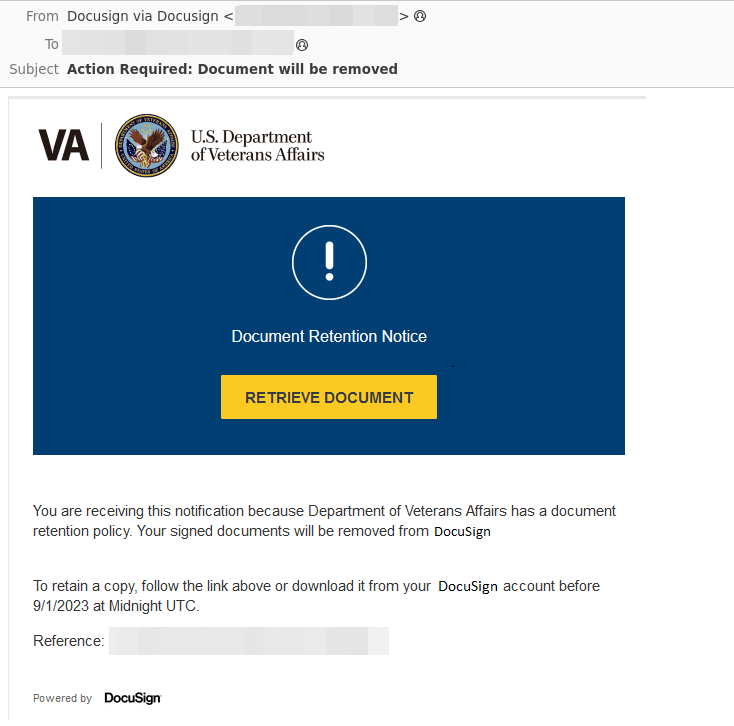
Also of note is a current DocuSign impersonation campaign specifically targeting the US Department of Veterans Affairs (VA). We have included a screenshot of this particular vulnerability in the image below:
Major Incidents and Industry Events
Microsoft Storm-0558 Breach Update
As discussed in our two previous iterations of this monthly report, we have some additional commentary on the Storm-0558 Breach. If you are unaware of the background of this particular attack, please see the section in last month’s threat review where we provided several key details behind the breach. The short version is that Chinese Nation-State threat actors procured a Microsoft consumer signing key and used it to forge authentication tokens to gain access to Microsoft cloud services.
What is new this month is that we now have some confirmed reports as to the extent of the damage. Previously, we only had communications from Microsoft that “approximately 25 organizations” had been impacted. We now have confirmation that 60 thousand emails from the US State Department had been exposed as a result of this breach. In addition, the attackers took a complete list of the department’s email addresses. This makes the targeting of future attacks much more effective for threat actors.
We likely have not seen the end of news about this breach, so we will continue to watch for updates in the coming weeks.
Another Microsoft Data Breach Involving 38 TBs of Data
It has been a bad couple of years for Microsoft on the security front, and it is not improving. Even after the Storm-0558 fiasco mentioned above, there is already a net new cybersecurity incident with Microsoft. This time involving 38 TBs of private data. To quote Microsoft:
Microsoft investigated and remediated an incident involving a Microsoft employee who shared a URL for a blob store in a public GitHub repository while contributing to open-source AI learning models. This URL included an overly permissive Shared Access Signature (SAS) token for an internal storage account.
The notice from Microsoft would have you believe said breach was quickly remediated and no damage done. While they claim this breach impacted no customers, it is worth noting that information regarding what was contained in the 38TB data trove is absent from Microsoft’s notice. Researchers from Wiz, who disclosed the breach to Microsoft, stated that the trove included the personal backups of two Microsoft employees and that said backup included:
The backup includes secrets, private keys, passwords, and over 30,000 internal Microsoft Teams messages.
While, yes, customer data was likely not impacted, this is not a breach to be simply swept under the rug. All of the items contained within this breach will undoubtedly be used in other attacks, and it also provides some insight into the internal workings of Microsoft and its technology stack.
At the very least, it is another line item on a growing list of Microsoft security lapses in the past three years that continues to bring Microsoft’s commitment to ecosystem security into question.
Critical libwebp Vulnerability
One critical CVE that came to light during the data period that system admins and security professionals should be aware of is a vulnerability in the libwebp image encoding/decoding library. This vulnerability uses a specially crafted HTML page to cause a heap buffer overflow, allowing for arbitrary code execution or denial of service.
This CVE was originally tracked by Google as a Chrome-specific vulnerability, but it became quickly apparent that it was NOT a Chrome-only issue. The vulnerability is now being tracked as CVE-2023-4863 with a CVSS score of 8.8 and the reach of impacted applications is quite large. The below list are just some of the affected applications that have been listed as vulnerable:
- Chrome
- Firefox
- Microsoft Edge
- Skype
- Electron-Based Apps (Like Microsoft Teams)
- Signal
- 1Password
- Brave
- Opera
It is also worth noting that there are some in the security space that see a potential link between this vulnerability and one for IOS and reported to Apple by security researchers Citizen Labs and tracked as CVE-2023-41064. It is believed that the NSO Group used this vulnerability and its pegasus spyware in an exploit chain called “BLASTPASS”.
The recommendation is to patch all affected software quickly.
Predictions for the Coming Months
- It remains to be seen what malicious application will ultimately fill the void left by last month’s disruption of the Qakbot botnet. We expect to see several different malware variants in the coming days. Still, as of now, DarkGate is looking like a potential option for threat-actors. We will continue to monitor this in future reports.
- We predict that the fallout from the Storm-0558 breach will continue for some time. While we heard numbers from the US State Department this month, more details will likely come to light in the coming days. This will be primarily driven by the ongoing DHS Cyber Safety Review Board investigation into the incident and US government consumption of cloud services in general. The result may be more information and new government policies on the usage of cloud services.
- Finally, we also predict that threat actors will seek to capitalize on the libwebp vulnerability that was disclosed over the last month. With as far reach as this vulnerability is, it will take the industry time to roll out patches. There will likely be successful exploitation of this vulnerability in the wild before we see the end of it.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on further Microsoft Security Incidents:
There was a time where I couldn’t see Microsoft being the source of so many data incidents but the last 3 years are proof that it was an unrealistic expectation. It’s no secret, that when you’re a major cloud vendor, you become a target. However, the whole business model of the Microsoft Cloud is built around trust, and that trust is failing at this moment for many in the industry. With as crucial as Microsoft Cloud Services are to the general public, I don’t think there has ever been a time where the expertise of independent, third-party security vendors has been needed more. In light of all the recent breaches, Microsoft needs to win trust back, and they’re going to have to be open, transparent, and work with the vendor community in order to do so.
From Umut Alemdar, Head of Security Lab, on zero-day vulnerabilities in 2023:
The cybersecurity state in September 2023 is alarming, with the number of reported zero-day vulnerabilities increasing significantly from around 52 in 2022 to approx. 77 so far in 2023. One of the most critical zero-day vulnerabilities discovered in 2023 is CVE-2023-5129, a heap buffer overflow in the libwebp image library. This vulnerability is being actively exploited in the wild and allows attackers to execute arbitrary code on victim systems. Businesses should invest in cybersecurity measures to protect themselves from the increasing threat of zero-day vulnerabilities. By implementing a comprehensive cybersecurity strategy and regularly training employees on cybersecurity best practices, businesses can help mitigate the risk of being attacked. But remember, even with preventive measures, some zero-day vulnerabilities can still be exploited. Event logging and business recovery measures, such as backups for critical systems, are critical for detecting, investigating, and recovering from zero-day attacks.
Monthly Recommendations
- Urgently get patches installed for applications in your environment that are affected by the libwebp vulnerability. The best place to start is to ensure web browser updates are handled first.
- With the increase in brand impersonation attempts and cleverly disguised phishing messages, it is an excellent time to review your email security posture as well as your internal practices for security awareness training. These services will go a long way towards preventing end-users from falling prey to this noted increase.
- Specifically, if you use DocuSign internally, ensure you communicate the best methods for spotting DocuSign phishing emails to those in your organization who are most likely to encounter them.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


