

Email Spoofing
Definition & how to protect against it
In this article, you will learn about the different types of email spoofing, as well as real-world examples of how these attacks work. We will also explore effective strategies for preventing email spoofing to protect individuals and organisations from these threats.
Table of Contents

What is Email Spoofing?
Email spoofing is a technique used in phishing and spear phishing attempts in which a person attempts to pass off a fraudulent email as a legitimate one that closely resembles a message an individual would typically receive. It can be extremely difficult for users and even sophisticated email filters to detect.
Examples for Email spoofing
Email spoofing attempts to rely on targeted individuals overlooking subtle differences in an email address or display name in order to successfully compromise information, access funds, or infect the device with malware. Email spoofing exists on a continuum of sophistication. While some forms of spoofing are quite simple, others require a high degree of skill.
The three common types of email spoofing include:
Display Name Spoofing
This is a simple but effective approach to email spoofing, in which a hacker sends a malicious email that impersonates a display name recognizable to the recipient. Display name spoofing is most effective when targeting mobile devices or email clients that show the sender’s name and hide their email address. While a trained user might notice the discrepancy between the display name and the email address, hackers are counting on untrained users who will focus on the display name and not the email address. DMARC doesn’t protect against display name spoofing.
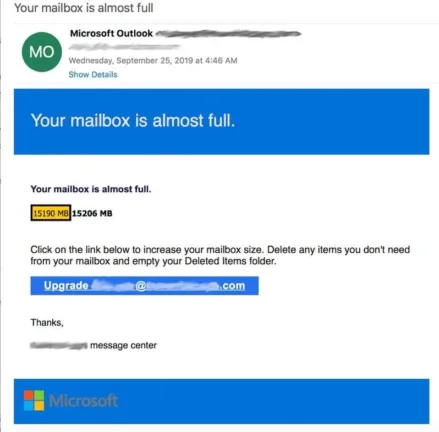
Here’s how display name spoofing works in the example above: You get an email from the display name “Microsoft Outlook,” but the email address is [email protected]. The attacker is working under the assumption that many busy people won’t check the sender email address carefully—they often don’t.
Another tactic in display name email spoofing is to use an email address as the display name. This distracts the user from looking at the sender’s real email address and adds an extra layer of legitimacy to the email. In the below example, the hacker uses a Microsoft email address as the display name.
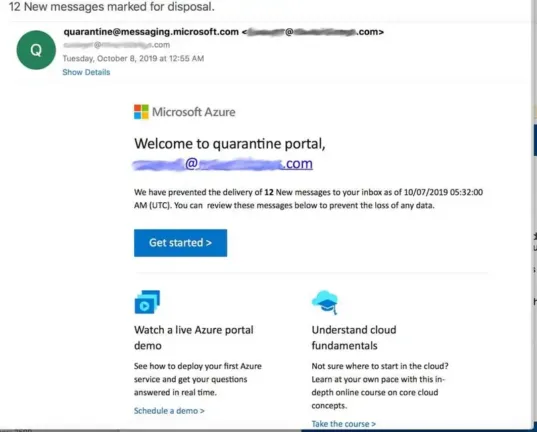
When combined with social engineering, display name spoofing can trick people into taking actions they otherwise wouldn’t. For example, the attacker will research the target and use known facts to establish trust before making a request. This social engineering tactic is often used in spear phishing, also known as business email compromise and CEO fraud, in which a hacker impersonates a high-level executive and requests that an employee send a wire transfer.
Close cousin spoofing
A hacker sends a malicious email that appears to be a replica of a legitimate email address, but uses slight alterations to bypass DMARC technology. Close cousin spoofing may include Cyrillic characters that are undetectable to the human eye, or extensions that don’t match the legitimate URL. For example, this spoofing attack technique might involve using the .co domain extension instead of .com or by adding or subtracting a letter or word from the URL.
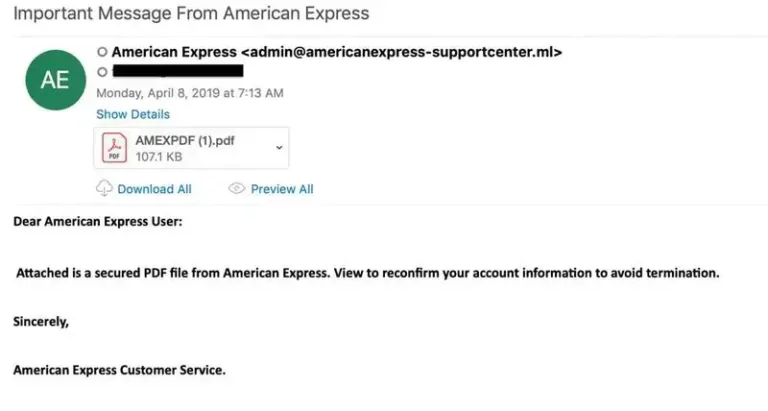
Let’s say your company is called Maine Express and has the domain maineexpress.com. A spoofer could register the domain mainexpress.com or maineexpresss.com and fool at least a portion of email recipients. Or they could add an an additional but plausible word to URL, such as “global,” making it maineexpressglobal.com and so forth.
Domain name spoofing
A hacker sends a malicious email from an address that impersonates the recipient’s domain name. For example, an attacker could send an email that appears to come from [email protected], a legitimate Bank of America email address. Except, it doesn’t actually come from that address. It’s a phishing email designed to get you to click on a URL that sends you to a spoofed webpage that looks like www.bofa.com.
Fortunately, exact domain email spoofing is less common than it used to be, thanks to the Sender Policy Framework (SPF) and Domain Keys Identified Mail (DKIM). Once incorporated into DNS settings, SPF or DKIM prevent unauthorized use of domain names for spoofing attacks.
How to stop email spoofing
Though some spoofing attacks are extremely hard to detect, many are easy to spot, and user awareness training can empower your employees to make a difference. Establishing clear policies about processes like sending wire transfers also helps mitigate the risk of business email compromise, CEO fraud, and other spear phishing attacks. To counter cousin domains, some businesses deliberately buy all similar domains. This has the added benefit of reducing the risk of trademark infringement.
Finally, advanced email security solutions can quickly analyze inbound emails for signs of email spoofing and other anomalies. 365 Total Protection analyzes email headers to determine if the display name and email address are consistent with the company’s entity model. It also adds an SPF-like layer into the email filtering process that spots unauthorized use of legitimate domain names and cousin domains.
The solution also looks for revealing inconsistencies in email structure and content, including words and phrases commonly used in business email compromise. If spear phishing is suspected, a customizable warning banner is placed inside the email alerting the user to a suspected spoofing attack.
Learn about HORNETSECURITY’S SERVICES
Interested in Related Topics?
Did you like our contribution to email spoofing? Then other articles in our knowledge base might interest you as well! We help you learn more about cybersecurity related topics such as Emotet, Trojans, IT Security, Cryptolocker Ransomware, Phishing, GoBD, Cyber Kill Chain and Computer Worms.


