

How Attackers Are Targeting Microsoft Teams and What You Can Do to Defend Against Them
Criminals are always looking for new ways to attack your users, and finding a new avenue to put their phishing messages or malware in front of your staff is crucial for them. Microsoft Teams (with over 320 million monthly active users) provides just such a platform, and until recently it didn’t have anywhere near the same protections as email.
We’ve been dealing with malicious emails (spam, phishing, malware) for decades at this point, and while not 100% perfect, modern email hygiene solutions such as Hornetsecurity’s Advanced Threat Protection keeps 99%+ of the bad stuff out of your user’s inboxes.
But Microsoft Teams doesn’t have the same history which means there are fewer technical options for protection, plus your users are less likely to be suspicious of messages in Teams.
In this article we’ll look at why Teams is becoming such a popular vector for criminals, and how using Teams as part of their overall attacks can increase their effectiveness, plus what you can do to protect your organization.
How Cybercriminals Are Targeting Microsoft Teams Users
Teams has several attractive features for criminals to subvert:
- Chat, also known as instant messaging, allows one-on-one communication, as well as one-to-several. This is a great tool for business productivity, but also a good way for bad actors to build rapport with your end users to further their social engineering goals.
- File sharing built in. One of the powers of Teams is how easy it makes filesharing, with links to files or websites pasted into messages a normal activity. This is a golden opportunity to bypass those extremely effective email filters and put your file or link to a malicious website right in front of your unsuspecting victims.
- There are hundreds of apps available to extend the functionality of Teams – often these can be installed by a Teams owner themselves (not a suspicious IT admin), so this is another great way to get their malicious wares in front of users.
- In many organizations, Teams is also integrated with the phone system, with users using Teams to call normal phones, and also be called from Teams or phones. This presents a good option for attackers who engage in vishing (voice-based phishing).
Variants here are using Chat to build a connection with a user, then serving them a link or a file under some pretense, that infects their computer with malware or tricks the user into entering their credentials on a fake login page.
Often attackers will pose as colleagues or IT staff to build trust with their victims. This can take the form of requesting MFA codes for “verification” or guidance to assist with “password resets”.
Alternatively, it can be used for security warnings, to add urgency / emotional manipulation to the request.
Another option is where an attacker has compromised one legitimate user and now looks through Teams for data that this user has access to, meeting recordings, files and chats.
This is a “trusted space” where staff share a lot of information, providing a gold mine for the attackers to access data outright, and / or use the compromised account to communicate with others in the business to compromise their accounts as well.
Recipients in the business are likely to trust internal communications from a colleague much more.
Real world attack patterns that we have seen includes starting with “email bombing” where a user’s inbox is flooded with thousands of newsletters, making it impossible for the user to do their work.
This is then followed up by a helpful message in Teams from the “IT department”, along the lines of “we’ve seen the problem with your inbox, and knew that trying to email you to help you out would be lost in all the emails, so we’re contacting you in Teams instead, please run this tool to fix the problem” leading to full compromise of the users device.
But how do the bad guys get their messages to your users in the first place?
Teams federation, trial tenants and trust between companies
One popular approach for criminals up until recently was registering Microsoft 365 trial tenants, which provided a certain measure of trust when messages from this tenant were sent to your users. However, since July 2024 the default setting is to block this exploitation route.
Be aware however that criminals still use trial tenants as these are normally trusted by the wider internet more than a random sender. They also use cloud infrastructure in AWS, Azure and GCP, along with Cloudflare for the same reason.
Security settings in Microsoft Teams that you should be aware of
You have a great deal of control over who your users can communicate with in Teams, and more importantly, who can communicate with them. If you have administrative permissions, head to Teams admin center and click on Settings & policies.
Settings for limiting external collaboration
The two areas to look at are Guest access and B2B member access, be aware that these are tenant wide and can’t be customized for different groups or users.
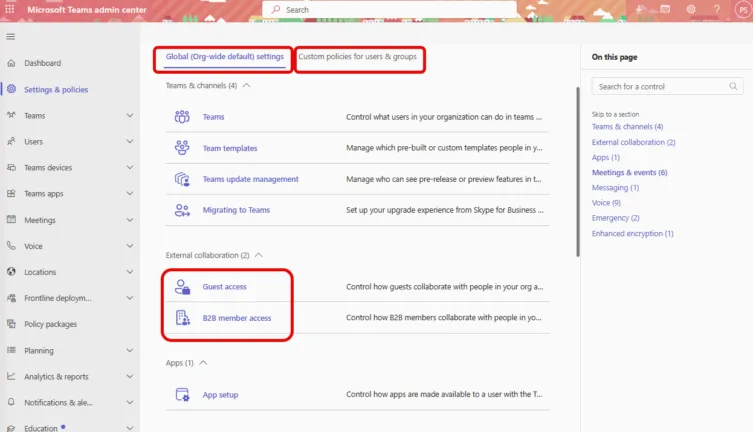
If you turn Guest access off, external users can’t collaborate with your internal users in Teams at all. If you turn it on, you can customize calling, meeting and messaging settings for guests.
Obviously turning the setting off provides more security against Teams phishing communication but might hinder business processes so make sure everyone is on board before turning it off.
The only setting under B2B member access is whether an external user that has a Microsoft 365 Copilot license in their home tenant is allowed to use Copilot functionality in your tenant.
There used to be a setting in this area for blocking or allowing communication from (consumer) Skype, but since it was discontinued in May 2025, whatever that setting was is irrelevant.
Cross-tenant access settings
Another area that you should check is what the federation settings are for your tenant, in the Entra portal. Go to Entra ID – External Identities – Cross-tenant access settings.
Here you can configure settings for specific Entra ID tenants that your business works with, Default settings which will apply to any other tenant and Microsoft cloud settings which covers Azure Government and Azure China tenants.
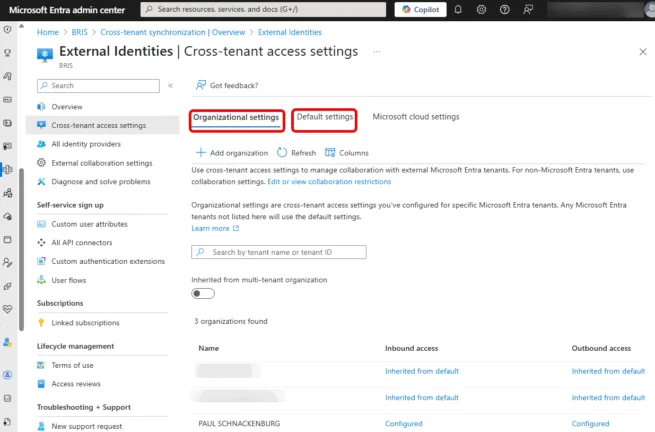
A full deep dive is beyond the scope of this article, but do have a look at the Default settings tab. Here you can set how you want inbound access and outbound access to be configured for every tenant not listed under Organizational settings.
For inbound you can allow or block B2B collaboration which means external users can be invited as guests into your tenant and be given access (in Teams or SharePoint for example).
Again, an outright block might not work for your business. There are also settings for B2B direct connect (see below) and if you trust the MFA process of their tenant, in other words, if you require MFA for access a resource, and the guest user has already performed an MFA in their home tenant, they’re not prompted again.
For both inbound and outbound defaults, you can specify groups or everyone in the tenant. One of the core principles of Zero Trust is assigning Least Privilege access, so if only certain departments in your business need to be invited into other tenants, only add those groups.
And for inbound access you can block every business but allow specific tenants that you know you’re collaborating with, thus blocking the attacks through Teams (and other Microsoft 365 workloads) right at the gate.
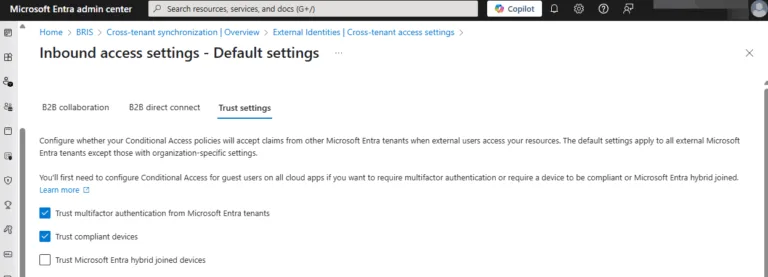
B2B direct connect is a special case that only affects Teams shared channels, a concept introduced a few years ago.
Here you can set up collaboration with other Entra ID tenants (administrators in both tenants need to set this up) and then you can create Shared channels in Teams where users (in specified groups) from the other tenant can be invited without having to create Guest accounts at all, they’re “just there”, improving collaboration.
The risk here is minimal, as you have to work with the other administrators to set this up in the first place and will hopefully verify that they aren’t criminals.
However, all of these settings in Teams and Entra only work for unknown users, coming from unknown tenants, which is a good start, but doesn’t cover compromised user accounts.
Best Practices: How to Strengthen Microsoft Teams Security
If a user in a tenant you collaborate with is compromised and under attacker control, they’ll use it to explore everything that account has access to in their home tenant, but also what they have access to in yours.
Even worse, if a user account in your business is compromised, not only can the attacker access everything that it has access to in your tenant, but also other tenants where it’s a guest.
A great tool for understanding the access a user has, as well as see and tighten up both internal and external permissions to both Teams and SharePoint sites is Hornetsecurity’s 365 Permission Manager.
Apart from configuring Teams guest access and Entra ID cross-tenant settings, what other steps should you take to minimize the risk to your users?
- Enable Multi-Factor Authentication for all user access to Microsoft 365, including Teams. This adds a much stronger verification that the account signing in is indeed the correct user than just a username and password. Also, not all MFA is created equal, start migrating to phishing resistant MFA flavors, such as Windows Hello for Business, hardware 2FA keys such as YubiKeys, or Passkeys, where a smartphone acts as the 2FA hardware.
- Regularly review granted access to different Teams, for internal users, but especially for Guest users.
- Train users not to just be aware of phishing and suspicious messages in email, but also in Teams, via voice calls and in other communication apps such as WhatsApp, LinkedIn chat etc. Use our excellent and low admin overhead solution, Security Awareness Service to turn your users into strong “human firewalls”.
- Use the new features in Hornetsecurity’s Advanced Threat Protection (ATP) to block malicious links and attachments in Teams. This is a brand-new addition to ATP and adds similar protections that we provide for emails to Teams messages and attachments.
How 365 Total Protection Secures Microsoft Teams
Using 365 Total Protection gives you a complete suite of protection for your Microsoft 365 tenant, including detecting and blocking phishing attack messages and attachments in Teams as just mentioned.
It also deals with malware and ransomware attempting to come in via emails, and adds AI-Powered email security which prevents account takeovers by securing login credentials. Furthermore, there’s compliance and archiving functionality for ensuring regulatory compliance for your Teams conversations.
Secure Microsoft Teams with 365 Total Protection
Microsoft Teams security is more critical than ever. Cybercriminals are exploiting chat messages, file sharing, and account credentials to launch attacks.
With 365 Total Protection, you can:
- Block phishing messages and malicious links before they reach your employees
- Prevent malware and ransomware infections from compromised Teams accounts
- Monitor and secure Teams communications for compliance and data protection
Protect your Teams environment today – schedule a demo now!
Microsoft Teams Security Shouldn’t Be an Afterthought
Cybercriminals are targeting Microsoft Teams, making sure you don’t just watch the front door of your house (email) but also the windows (Teams) for attacks is very important.
As we’ve covered, this includes a multilayered strategy to only allow guests and external users to reach your users in the first place if there’s a clear business need for them to do so.
On top of this we add phishing resistant MFA for strong identity authentication, plus ATP link and attachment scanning for peace of mind. Finally, if all of those layers fail, we make sure our users are trained to be aware of the potential of phishing attack messages in Teams.
So, is Microsoft Teams secure enough for communicating confidential information? The answer is yes, if you’re aware of the risks outlined in this article, and you have implemented these best practices controls.
FAQ
Attackers use Teams’ features like chat and file sharing to impersonate colleagues, send phishing links, and distribute malware, taking advantage of users’ trust.
Enable Multi-Factor Authentication, limit guest access, regularly review permissions, and train users to recognize phishing attempts within Teams and other communication tools.
With increasing cyber threats targeting Teams, securing communications is vital to protect sensitive information and maintain organizational integrity from phishing and malware attacks.


