

The Future of Governance, Risk, and Compliance in the Cloud
Cloud adoption has made the overall field of Governance, Risk Management and Compliance (GRC) more complex. Couple this with more regulations in most geographies around the world, plus larger fines and more frequent changes to compliance regulations, and it’s clear that adapting to this requires a new approach for organizations – you need cloud security governance.
This article will look at GRC in the cloud and the challenges, emerging trends and opportunities that it brings for managing security, business risk and compliance.
The Challenges of GRC in the Cloud
Adapting to cloud environments
Regulation frameworks are struggling to adapt to cloud environments overall, including the rapid change in technology.
A simple example could be requirements around physical security for a datacenter, which made a lot of sense in the on-premises era, but many businesses today don’t even know where their data is hosted, and definitely not in which physical building it is – and they’ve outsourced the physical security to their Cloud Service Provider (CSP).
Understanding the shared responsibility model
That one example leads to another challenge, understanding the “shared responsibility model” which all cloud providers have.
In essence, it means that there are some controls (mitigation measures in regulatory language) that’s under the CSPs control and responsibility, some that are yours to manage (endpoint security for example) and some that are shared.
An example of the latter could be identity security – the CSP is responsible for providing a secure directory plus authentication / authorization options, but if you give every user administrative access to your cloud tenant, the inevitable breach is on you, not the CSP.
The number of settings & permissions
There are a few truths in cybersecurity that are always true, no matter which technological era we’re looking at. “Complexity is the enemy of security” was true for 1970’s mainframes, 1990’s client server and the 2010’s cloud environments.
It’s been estimated that across Azure, AWA and GCP there are about 40,000 different permissions that can be granted. Add to that the thousands of settings that can be configured for a Microsoft 365 tenant, and you begin to see the scope of the challenge.
And these cloud configurations and permissions can interact in “interesting” ways, making it very hard to map out how a change in one part can cause unintended consequences in another resource.
The rate of change
The other challenge is the rate of change – in the on-premises world we had a new server OS version every few years, enabling IT Pros and security teams to adapt new technology in a methodical fashion, developing and refining best practices to ensure stable and secure systems.
Risk of misconfigurations
Today, with the cloud changing every day, there’s never a day where optimal settings are configured across the board, instead it’s a never-ending catch-up to take advantage of new features whilst maintaining a good overall posture.
This landscape brings increased risk of misconfigurations, which can lead to data breaches and compliance failures.
Keeping track of all resources
Another truth is that “you can’t protect what you don’t know about” so maintaining a solid asset inventory, so that you know what resources you have (user accounts, mailboxes, virtual machines, containers, databases, etc.) and where they’re located, along with their access permissions is vital.
Again, back on-premises this was “easier” as most resources stayed more or less the same over time, whereas the cloud is full of impermanence, with resources and networks being spun up rapidly and torn down just as quickly.
Increased attack surface
Finally, the fact that most enterprises connect their on-premises infrastructure and their cloud resources, further increases their attack surface, enabling attackers to pivot from one to the other.
Cloud Security Governance Best Practices
Use a cloud-based service for GRC
It’s important that businesses that must comply with regulations (and that’s most nowadays) take a holistic approach. Start by using cloud-based services for GRC to manage the cloud – a cloud security governance framework. You need a centralized solution for governing (and monitoring) resources, permissions and access.
Have a cloud governance strategy
You also need a cloud governance strategy to understand the different regulatory frameworks (GDPR, HIPAA, NIS2, ISO 27001, etc.) that you must comply with, for all the different countries that your business operates in.
Often, you’ll need to consider data sovereignty and cross-border compliance to manage or restrict the movement of data from one country to another.
An interesting statistic is that 26% of businesses audit their cloud infrastructure daily, something that’s only possible when the process is automated. The old days of tracking manually with a spreadsheet every six months are well and truly behind us.
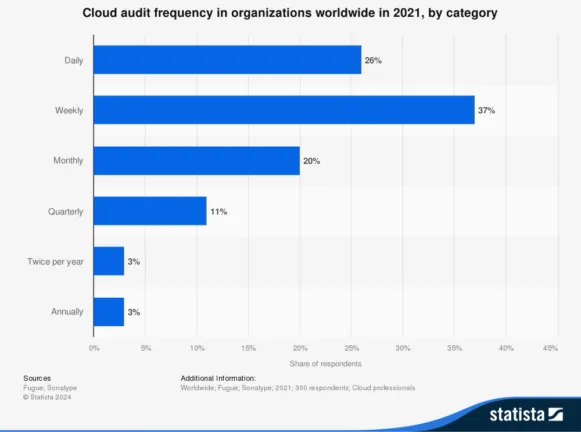
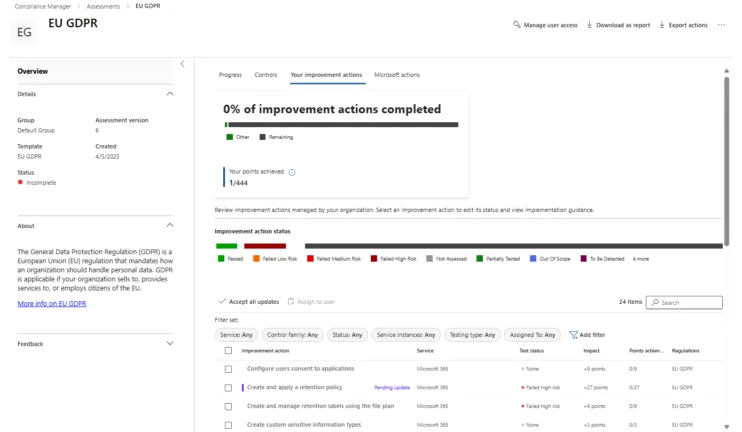
Use a Dashboard
Then inventory what controls your CSPs have already fulfilled, in many cases you’re already halfway there as they have to fulfil many controls because the infrastructure and network is under their control.
Here’s an example dashboard from Purview Compliance Manager, a feature of Microsoft 365.
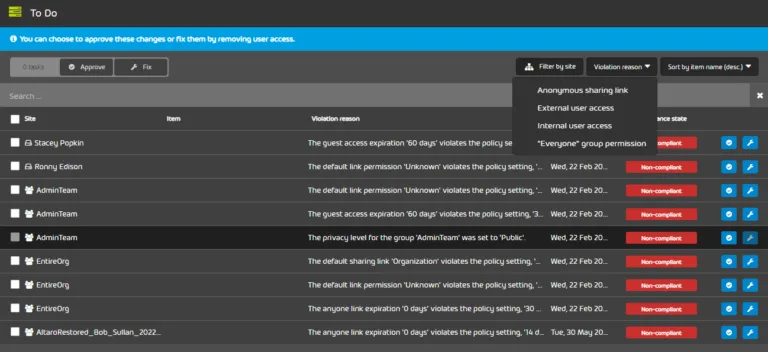
Keep track of all permissions with Hornetsecurity’s Permission Manager
One core component of both maintaining security of your Microsoft 365 cloud tenant, as well as governing, risk management and compliance reporting is data sharing and permissions.
Here, Hornetsecurity’s industry-leading 365 Permission Manager solution provides full visibility of all permissions across SharePoint Online and OneDrive for Business, and not only identifies but also lets you easily close permission gaps.
There’s also comprehensive compliance reporting built in, making it easy to demonstrate compliance adherence for auditors. Being cloud-based, 365 Permission Manager simply scales from the smallest to the largest environments.
It not only finds the risks, and helps you mitigate them, it also provides templates based on cloud security governance best practices to ensure that existing and future document sharing is managed securely.
Here’s the built-in To Do list which helps you apply the principle of least privilege across your entire estate.
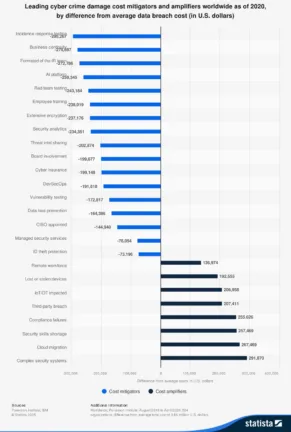
To understand which steps, out of all the mitigation steps a business can take to minimize the cost of cyber crime to their business, have the most impact, consider this graph from the Ponemon Institute from a few years ago.
You’ll see that Compliance failures is a large cost amplifier (and complex security systems is the largest amplifier – see above), whereas employee training is one of the biggest cost mitigators.
AI for GRC, GRC for AI: Why it’s essential
The widespread adoption of generative AI tools in business in all different verticals brings interesting risks and opportunities. In environments where GRC is lax or non-existent, it’s likely that staff are using consumer AI tools and thus sharing potentially sensitive business data or PII without thinking about the consequences.
Consumer GenAI tools ingest all user prompts to further train their models, leading to data leakage. It’s thus important that organizations apply strong governance to the use of LLM AI tools.
Equally, you need your GRC tools (such as 365 Permission Manager) to use AI and Machine Learning technology to manage the huge amounts of data and signals to govern permissions and access.
Related: AI in Cybersecurity: Insights and Perspectives from CISOs
Take Control of Your Cloud-Based GRC with 365 Permission Manager
Managing governance, risk, and compliance in the cloud is more challenging than ever. 365 Permission Manager gives you the visibility and control you need to manage permissions, reduce risk, and ensure compliance.

Key benefits:
- Automate permission management and compliance reporting;
- Gain real-time insights into security and access issues;
- Meet GDPR, HIPAA, and other regulatory standards.
Schedule a demo today and strengthen your cloud-based GRC strategy!
Why Cloud-Based Governance, Risk, and Compliance Is the Future
The pressure of compliance regulations on businesses worldwide isn’t going to abate, and forward-looking businesses take this as an opportunity to adopt a modern, cloud-based GRC strategy. Using 365 Permission Manager helps you maintain strong governance, minimize risks and stay compliant.
Adopting cloud-based GRC tools is the way to manage the increasingly complex regulatory landscape going forward.
FAQ
GRC in the cloud is more complex due to multiple regulations, shared responsibility models, and the dynamic nature of cloud environments, which increases the risk of misconfigurations.
The shared responsibility model outlines that the Cloud Service Provider manages some security controls, while others, like endpoint security, are the organization’s responsibility.
Businesses can enhance their cloud GRC using centralized cloud-based tools like 365 Permission Manager to govern resources, manage permissions, and ensure compliance.


