

How Automated Security Notifications Are a Game Changer for Efficient Security Operations
Introduction – Why Speed is Everything in Cybersecurity
The pace and volume of threats targeting organizations of all sizes everywhere is increasing at a rate many security teams are struggling to keep up with. IT teams are overwhelmed by the alerts and notifications coming in left, right and center. They’re doing their best with the tools they have but often resorting to manual monitoring, causing delays.
There’s no silver bullet, no single solution that’s going to solve this. Threat response time is critical and can mean the difference between containment and catastrophe. As we saw in an earlier blog, Security Teams are often overwhelmed and their response capabilities significantly delayed having to use manual monitoring.
The Pitfalls of Relying on Manual Monitoring
I was thinking of an analogy I can use to highlight this issue, and I settled on fishing, specifically bottom trawling.
This involves fishing boats dragging a massive net across the ocean floor sweeping up everything in their path, dumping the catch up on the boat. People on the boat spend time trawling through it all, filtering out the fish they need, discarding the rest.
Like those fish, critical threats are often caught up and often hidden in the tsunami of alerts washing over Security Teams. These threats often go undetected for hours or days, sometimes even months as we saw in the case of the spectacular Solar Winds Cyber Attack attack in 2020.
In fact, it came as quite a surprise to see IBM’s statistics covering the minimal improvement for the average time to detect a breach over the course of seven years.
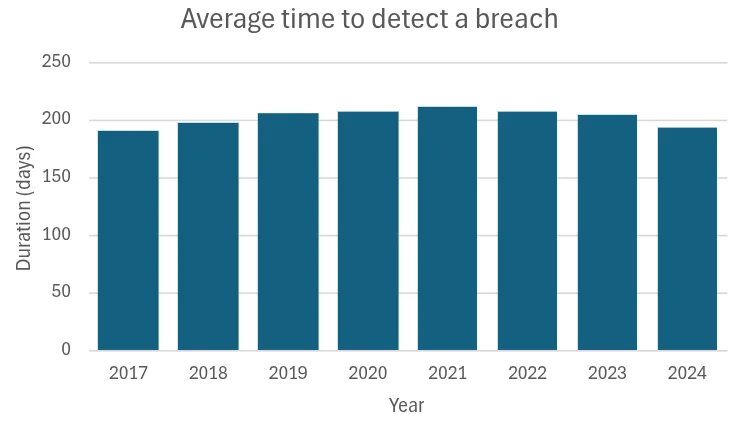
Relying on manual monitoring often results in missed or delayed alerts and could lead to catastrophic consequences as we saw in the Target 2013 breach. Investigations found that the Security Team failed to act on the multiple alerts, perceiving them as false positives likely exacerbated by the alert fatigue facing the team.
Threat actors often create a lot of “noise” with false positives generation, distracting security teams with fake alerts ahead of or during an attack, often resulting in missing the real threats. The Censys 2024 State of Threat Hunting report showed the number of false positives was a whopping 20% for some respondents.
What Are Automated Security Messages?
Automated security messages are real-time notifications triggered by specific events in response to detections like threats, vulnerabilities, or other suspicious activities in the digital environment.
The trigger could be in the form of a threat actor attempting to brute-force a password, through policy violations to phishing attempts. Automated Security Messages typically provide actionable information related to the event and details of the recommended actions.
Notifications received in real-time reduce the load on the team and the need for constant monitoring, improving operational efficiency and enabling you to act faster, prioritizing responses to legitimate threats.
The impact of threat response time
I mentioned at the start how impactful the threat response time is when it comes to incidents. Central to preventing such incidents and responding effectively are automated security messages. Think of them as a “canary in the coal mine” providing an early warning with a predefined set of corrective actions to quickly contain a threat, crucially important for business-critical systems and services.
Any discussion around security automation would be incomplete without also including the impact of AI. It’s a complete game-changer because of how it is transforming the speed and accuracy of the notifications, at a pace and scale us humble humans cannot possibly compete with, and neither should we even try!
An interesting finding in IBM’s 2024 Cost of a Data Breach Report showed that organizations heavily invested in using security AI and automation were able to identify and contain a data breach a staggering 100 days faster than those who don’t.
The 20% figure of false positives from that Censys report mentioned earlier can be cut right down with AI, ensuring that organizations can prevent incidents and contain threats fast and more efficiently.
Many security teams are already integrating AI into their security operations, with the term “AI-SecOps” becoming part of the vernacular. The benefits, use-cases, how and why it’s revolutionizing the industry are summed up well in this article by Wiz, demonstrating the positive impacts from workflows through to threat detection.
The Benefits of Real-Time Security Alerts
Faster Threat Response
Real-time notifications delivered almost immediately lead to faster isolation and remediation of threats such as ransomware as it tries to infect its way across your network. Despite what you may think or hope, ransomware remains rampant.
Better Situational Awareness
Security teams with their finger on the pulse and aware of what’s happening in their environment are better equipped to quickly ensure vital communications get the attention of the right people. This is critical when dealing with a high-priority incident and allows for faster and smarter decision-making in a time of crisis.
Reduced Alert Fatigue
Smart filtering features ensure alerts are relevant and actionable – not just noise. Alerts configured with specific or dynamic thresholds provide meaningful and actionable alerts, used by teams to prioritize and focus on immediate and high-priority threats.
Improved Collaboration Across Teams
Better collaboration leads to everyone seeing the same alerts in real-time, reducing communication gaps, providing a coordinated and unified response, and reducing the risk of duplicated efforts. Security Incidents often make for a very high-pressure environment; thus, a coordinated approach shared across teams enabled by real-time alerts helps to provide clear and unimpeded lines of communication.
How 365 Total Protection Automates Security Messaging for Microsoft 365
Built-In Notifications for Email Threats, Compromised Accounts, and More
Unsurprisingly Microsoft 365 has proved to be a common attack vector, evidenced by statistics like the 43% of breaches involving Microsoft 365 and the increase of password-based attacks rising in the first quarter of 2024 from 3 billion per month to 30 billion!
As you’ll see, the 365 Total Protection platform is tightly integrated with Microsoft 365, identifying and alerting for threats in real-time using powerful and advanced spam, malware, and phishing filters.
The 365 Total Protection monitoring engine sniffs out unusual behavior such as repeated unauthorized login attempts or irregular login patterns, generating immediate notifications delivered by email and visible in the management portal, allowing security teams to take immediate action to investigate and remediate if needed.
Customizable Alerting Options
Alert fatigue from your Microsoft 365 environment becomes a thing of the past with the level of control available to your Administrators with 365 Total Protection. Alerts can be tailored in a way that works for your organization, allowing teams to control who, how, when, and where they receive alerts.
Every business is unique and has different risk priorities and thresholds. Customizable thresholds provide flexible options for configuring alerts, ensuring the right alerts are delivered to the person or team at the right time. Centralized storage of past alerts makes it easy to retrieve these at audit time, saving you the hassle and stress of last-minute document hunts.
Integration With Existing Workflows
Native Microsoft 365 API integration and Microsoft graph synchronization API provide seamless integration with Microsoft’s Sentinel SIEM platform, and the Microsoft 365 applications such as Exchange Online, SharePoint, OneDrive and Teams.
It doesn’t stop there though; this is just the start of the powerful workflow integrations built into 365 Total Protection. It can also easily connect with popular ticketing systems using API or email-based workflows, giving you quite a few options for centralized incident tracking and response.
Proactive Security Without the Overhead
The continuous AI-driven threat detection monitoring by 365 Total Protection takes care of the heavy lifting, responding and dealing with threats across your Microsoft 365 environment.
Once configured for your needs, the notifications you do get are the ones that need your attention, reducing alert fatigue by freeing security teams from laborious tasks like manual log reviews. Talking of freedom, this also means less time spent in front of dashboards, and more time to focus on actual threats.
Is your SOC team drowning in alerts, struggling with manual processes, and still missing threats? It’s time for a smarter approach. Hornetsecurity’s 365 Total Protection helps you:
- Automate threat detection and response
- Eliminate alert fatigue with AI-powered precision
- Manage Microsoft 365 security from a single console
- Improve your organization’s overall security posture
At the heart of 365 Total Protection, well perhaps more accurately the brain, is AI Cyber Assistant from Hornetsecurity.
Don’t let critical threats slip through the cracks. Discover how 365 Total Protection can transform your security operations today!

From Reaction to Prevention – Why This Matters for Security Teams
Responding reactively to alerts, manual investigations and repetitive tasks are frankly well past their use-by date. Automated security messaging helps organizations shift to preventing threats from escalating by responding before damage is done.
Instant, relevant and actionable alerts reduce human error and alert fatigue, enabling security teams to embed proactive threat detection and prevention into their practices. It strengthens the entire organization’s security posture, without adding headcount and helps pivot the approach to proactive strategic defense improvements.
Conclusion – Get Ahead of Threats with Automated Security Messaging
Embracing and incorporating automated alerts to reduce alert fatigue, increase response times and take a proactive defense approach makes security teams more efficient and effective.
The threat landscape is constantly changing with new threat actors entering the scene, bringing with them new tactics, techniques and procedures security teams must be able to detect.
A continuously monitored environment using AI-powered alerting from 365 Total Protection, ensures your security team receives timely and actionable notifications, prioritizing the risks across your Microsoft 365 environment.
We’ve seen from many examples explored in this blog the devastating impact of delayed alerts, and how speed and visibility are everything in the world of cybersecurity. Make sure you have the tools you need to provide real-time insights to stay ahead of attackers and the destruction they bring.
Even small teams will be empowered to act like big ones with automation on their side.
FAQ
Automated security messages are real-time alerts triggered by specific events that notify teams about potential threats or suspicious activities, enabling quicker responses.
They reduce manual monitoring needs, deliver actionable insights instantly, and help prioritize alerts, allowing security teams to focus on genuine threats.
Speed is critical because prompt responses can prevent threats from escalating, minimize potential damage, and maintain the organization’s security posture.



