

The SharePoint Hack – Lessons Learned From 400+ Servers Being Pwned
You might have seen in the news that over the last few weeks many organizations have had their SharePoint servers compromised.
In this article we’re going to cover what happened with this SharePoint vulnerability, who the attackers were and why, the geopolitical ramifications, a reveal of another vulnerability in SharePoint’s sibling, Exchange Server, and what you can do to protect your business against similar vulnerabilities in the future.
The Beginning of a SharePoint vulnerability
The difference between a SharePoint Server & using SharePoint Online
A quick explanation – Microsoft provides SharePoint Online as part of Office / Microsoft 365 and that’s a fully managed service, which is not affected by this vulnerability.
They also offer SharePoint Server 2016 and 2019, along with the newer SharePoint Server subscription edition – all of which organizations run on their own servers, in their own datacenters, where protection and updating / patching them is up to the business themselves.
This story starts at the Pwn2Own (hack an item and you get to keep it – people walk away with laptops and even cars) ethical hacking competition in May 2025. A researcher at Viettel earned $ 100,000 for revealing the ToolShell flaw (see below) in SharePoint server.
Microsoft issued patches for the affected server versions, but they weren’t comprehensive, and thus exploitation starts in June, initially on a small scale. It seems at this stage that compromises are used to gain a foothold and then move laterally inside an organization to further compromise other systems.
An issue here is that once compromised, attackers can use a SharePoint server ASP.NET machine key to achieve persistence, even if the patch is subsequently applied (details here).
Specifically, CVE-2025-53770 addresses the previously disclosed vulnerability CVE-2025-49704 and CVE-2025-53771 addresses the previously disclosed CVE-2025-49706 vulnerability.
The Acceleration of the threat
You may remember the 2021 Microsoft Exchange server mass compromise event, attributed to various Chinese threat actors. It followed a similar trajectory, initial stealthy compromises of servers for the purpose of stealing Intellectual Property or espionage, but then when the vulnerability became widely known, and patches / mitigations were available, a “feeding frenzy” ensued to compromise as many vulnerable systems as possible, with over 250,000 servers breached.
Déjà Vu: SharePoint Exploited by Chinese Threat Actors
The west’s strong diplomatic response in 2021 clearly wasn’t sufficient, as this new SharePoint vulnerability has now been exploited by at least three different Chinese threat actors (Linen Typhoon (stealing IP) and Violet Typhoon (Espionage) and Storm-2603), along with doubtlessly many other groups getting in on the action.
Storm-2603 in particular has been deploying the Warlock ransomware using Group Policy software distribution in Active Directory.
MAPP and Early Exploitation
A wrinkle in both the 2021 story, and the SharePoint vulnerability is that there’s some evidence that Microsoft Active Protections Program (MAPP) might have provided early access to Chinese attackers.
MAPP is a program that Microsoft provides for cyber security vendors worldwide where they get advance notice (a few days depending on your level in the program) of upcoming vulnerability disclosures / patches, which is intended for them to be able to assist their customers in protecting themselves.
However, if the information was leaked prior to the patches being released publicly, and used to generate exploit code, the inclusion of Chinese cyber security firms in the program might be questionable. Microsoft is investigating if the current SharePoint vulnerability was leaked and an attack developed ahead of time.
Risk factor: Code Maintained in China
ProPublica has also reported that the SharePoint server code is maintained by engineers in China, again not something that’s necessarily evidence of malicious intent, but does merit including this in your risk calculation in continuing to use it.
High-profile victims
Notable victims of the SharePoint vulnerability are:
- the Department of Homeland Security,
- National Institutes of Health,
- and the National Nuclear Security Administration in the US, along with many other federal agencies,
- plus many other businesses worldwide.
Are you ready for round 2?
Just as the dust is settling on the SharePoint Server vulnerability and subsequent carnage of compromises, Exchange Server in a hybrid configuration was revealed to contain a serious vulnerability.
Black Hat 2025: Critical Exploit Revealed
At the Black Hat conference (6-7th of August 2025), researcher Dirk-Jan Mollema detailed the steps required to use administrative access on an on-premises Exchange server to compromise an organization’s Microsoft 365 tenant.
CVE-2025-53786: A Patch Ignored by Many
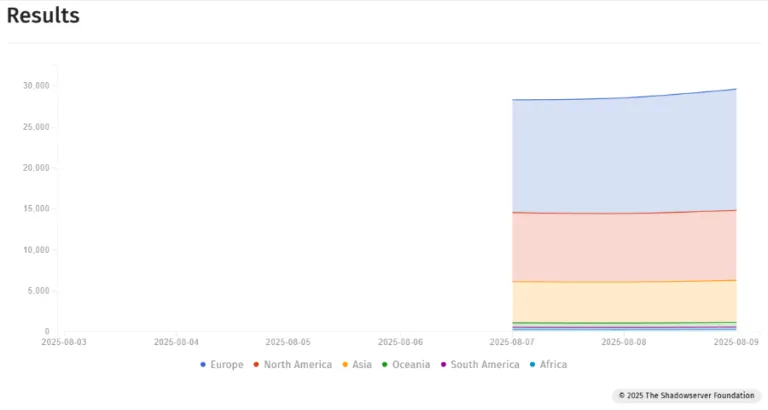
This vulnerability was initially described and patched in April 2025 (CVE-2025-53786), but it’s likely that many organizations didn’t implement the patch in a timely manner. At the time of writing, approximately 28,000 servers worldwide were vulnerable.
Many, many organizations have migrated to Microsoft 365 completely, but many others, either due to inertia, security concerns (more on this below) or mergers and acquisitions are still hybrid – meaning they have some user mailboxes hosted on Exchange Server on-premises, and others hosted in Exchange Online.
CISA in the US issued a rare emergency directive, mandating that federal agencies had to have this vulnerability patched by Monday the 11th of August. They also released a malware analysis report.
Technical steps provided by Microsoft
More detailed technical steps are provided by Microsoft, in a nutshell the risk involves service principals with overly broad permissions, and the recommendation being to replace these with a dedicated Exchange hybrid app. These service principals will stop working in October 2025, breaking functionality such as sharing free / busy between calendars etc.
Having another serious vulnerability, in another (still popular) on-premises server product, this close to the first one, is not a good look for Microsoft.
[Related]: Hackers Are Using Copilot to Grab Your Passwords. Here’s How
What’s a business to do?
- If you have a hybrid SharePoint deployment, follow all the instructions from Microsoft to patch your servers if you haven’t already, and assume that you’ve been compromised (if those servers are in any way reachable from the outside of your network) and start investigating for signs of compromise.
- If you haven’t got the skills in-house, hire experts to help you out. Do the same for any Exchange servers in a hybrid deployment that you have, again assume that if you haven’t patched already, there’s a high risk that you’ve been compromised, and act accordingly.
- Beyond those immediate actions, if you still have SharePoint or Exchange Server on-premises, it’s time to have a strategy meeting with the business leadership. Strategic decisions around on-premises versus cloud deployments for IT systems isn’t just a matter of comparing features and license costs, you need a holistic understanding of the risks you take on by continuing to use (some) on-premises software.
- Notably, neither SharePoint Online, nor Exchange Online in Microsoft 365 were vulnerable to either of these flaws and you might need to face the fact that Microsoft’s focus (for 10+ years) are SaaS services in the cloud.
- And they have armies of cyber security experts protecting them, because an exploitable vulnerability in Microsoft 365 could potentially lead to hundreds of millions of business accounts being compromised, compared to tens of thousands of on-premises servers.
- Furthermore, if you must continue to run these products (it’s not just Microsoft of course, although that’s the flavor of the month, any enterprise software is potentially vulnerable) you must assess whether they need to be internet accessible at all.
- Traditional VPN solutions have also proved extraordinarily vulnerable over the last few years, so considering a modern, cloud-based SASE solution for network-based isolation and access from anywhere is a good way of controlling access to any on-premises system.
- Another option is cloud based reverse proxy solutions, where you must log on to your SSO platform first, before accessing any service on-premises.
- Fundamentally the question is – if we continue to run on-premises software because we think it’s more secure (because we have more control) – is that hypothesis born out by the data? The answer will be different for every enterprise based on the software they rely on, their risk mitigations etc. but “it’s more secure because I can touch the servers” is no longer a valid answer.
- Finally, look at your patch cycles and prioritization parameters. Many times, the main rule is not to impact business operations, and schedule patch restarts in short, infrequent maintenance windows. That’s no longer sufficient, the time between a vulnerability being revealed and exploit code being available used to be measured in weeks, now it’s days or hours. Thus, any business-critical system that’s accessible from outside of your network, must be patched promptly.
Partnering with a strong cyber security partner such as Hornetsecurity is a good way of mitigating risks overall, we have a long history and strong track record of providing exceptional defenses for Microsoft 365 workloads.
Protect Your Hybrid Environment with 365 Permission Manager
In the wake of unprecedented attacks on SharePoint and other vital systems, ensuring robust permission management has never been more critical. Hornetsecurity’s 365 Permission Manager offers a comprehensive solution for safeguarding your organization’s data. Here’s how it can help:
- Automated Compliance Monitoring: Enforce strict compliance policies across SharePoint, Teams, and OneDrive.
- Data Access Control: Ensure employees only access the data they are meant to see, preventing unauthorized exposure.
- Continuous Auditing: Benefit from regular permission audits to identify compliance violations proactively.
- Real-time Alerts: Receive alerts for critical sharing permissions to act swiftly against potential risks.
- Simplified Management: Streamline the complexity of managing permissions at scale with an intuitive dashboard.

Don’t wait for the next incident to occur! Request your free trial today to see how 365 Permission Manager can fortify your organization against evolving threats.
Conclusion
With cybersecurity risks no longer being the domain of “geeks in the basement”, it’s vital that businesses elevate the conversation to the leadership. Company boards and the C-suite may not understand the details of cybersecurity risks, but they do understand risk mitigation overall.
Furthermore, the confluence of cyber security risks and geopolitical actions by nation states is also not something that ordinary businesses can just ignore and pretend is only a risk for military contracting companies. Shifts in how nation states like North Korea, Iran, Russia and China hack organizations in the west with very few consequences means we’re all a target.
As our businesses are now almost completely dependent on IT systems for their operations, plus the IT systems and their functioning in all the organizations in your supply chain, it’s incumbent on us in the security field to communicate these very real risks to decision makers in a comprehensive manner.
FAQ
The crisis began at the Pwn2Own ethical hacking competition in May 2025 when a researcher discovered the ToolShell flaw and earned a significant reward for it.
Victims included the Department of Homeland Security, National Institutes of Health, and National Nuclear Security Administration in the US, as well as various other global businesses.
Businesses must patch their SharePoint servers immediately, assume they’ve been compromised, and begin investigations alongside hiring experts if needed. Feel free to get in touch with our team here at Hornetsecurity for further assistance.



