

Ransomware: Prices, Pressure and Protection
Summary
Ransomware is the simplest way to monetize computer intrusions. Ransomware is thus the single greatest cyber-risk for corporations today. This blog post discusses ransomware prices, the pressure ransomware threat actors put on victims, and how companies can protect their assets.
Ransom amount
To estimate the currently demanded ransom amount, we analyzed ransomware samples available from OSINT sources. These are samples uploaded to various online services, such as online anti-virus scanning or malware analysis sandbox services, and thus shared with the security research community.
We have observed ransom demands spanning from US $100 up to US $10,000,000.
The highest ransom demand we observed was US $10,000,000. The Clop ransomware demanded it.
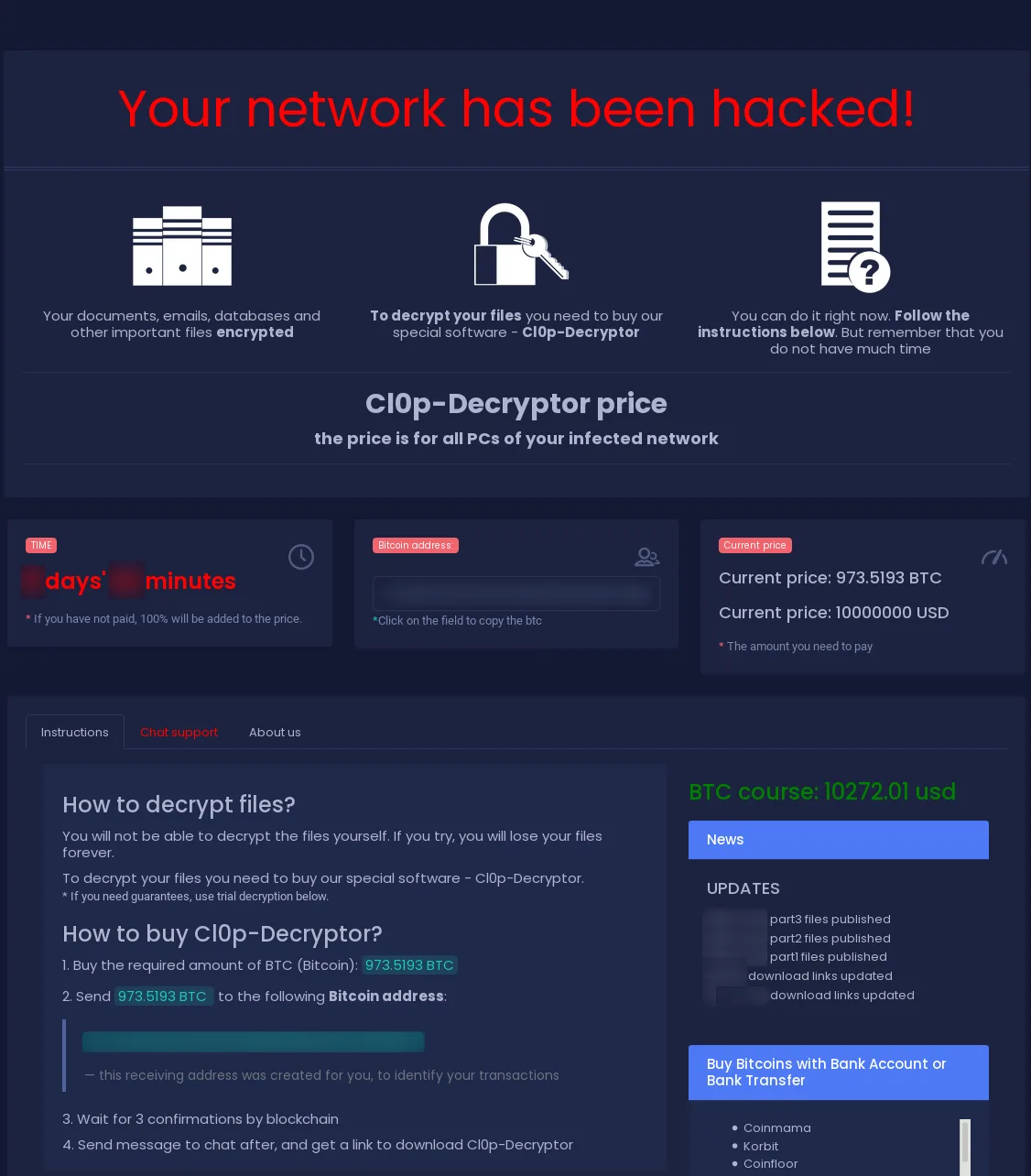
While preparing this blog post, public reporting of a US $50,000,000 ransom demand has surpassed our observed maximum demand. It is essential to understand why such an enormous range in demanded ransom exists. Therefore, we will discuss ransom amount volatility in the next section.
Ransom amount volatility
Ransom demand is adjusted based on several factors. One factor is victimology, i.e., threat actors demand a higher ransom from large corporations than a private, individual computer user.
As a case study, we can take a look at the first campaign of the Avaddon ransomware. It was spread via malspam sent by the Phorpiex botnet. Hornetsecurity reported on this campaign.1 The Phorpiex botnet usually sends Sextortion spam and other low-quality threats. The demanded ransom by Avaddon at the time was only US $500. The ransomware deployment was fully automatic, i.e., once a victim executed the ransomware from the email attachment, it started to encrypt the victim’s computer. Higher-quality threat actors will specifically target large companies and use the initial infection for reconnaissance first. After they have mapped the company’s network and identified all assets, they start the ransomware on many of the company’s computer systems simultaneously. This way they can demand more ransom because restoring the entire company computer infrastructure from backups is much harder than to restore a single encrypted computer.
During our research we found a recent Avaddon ransomware sample with a ransom demand of US $3,000,000. This is much higher than Avaddon’s previous demand of only US $500.
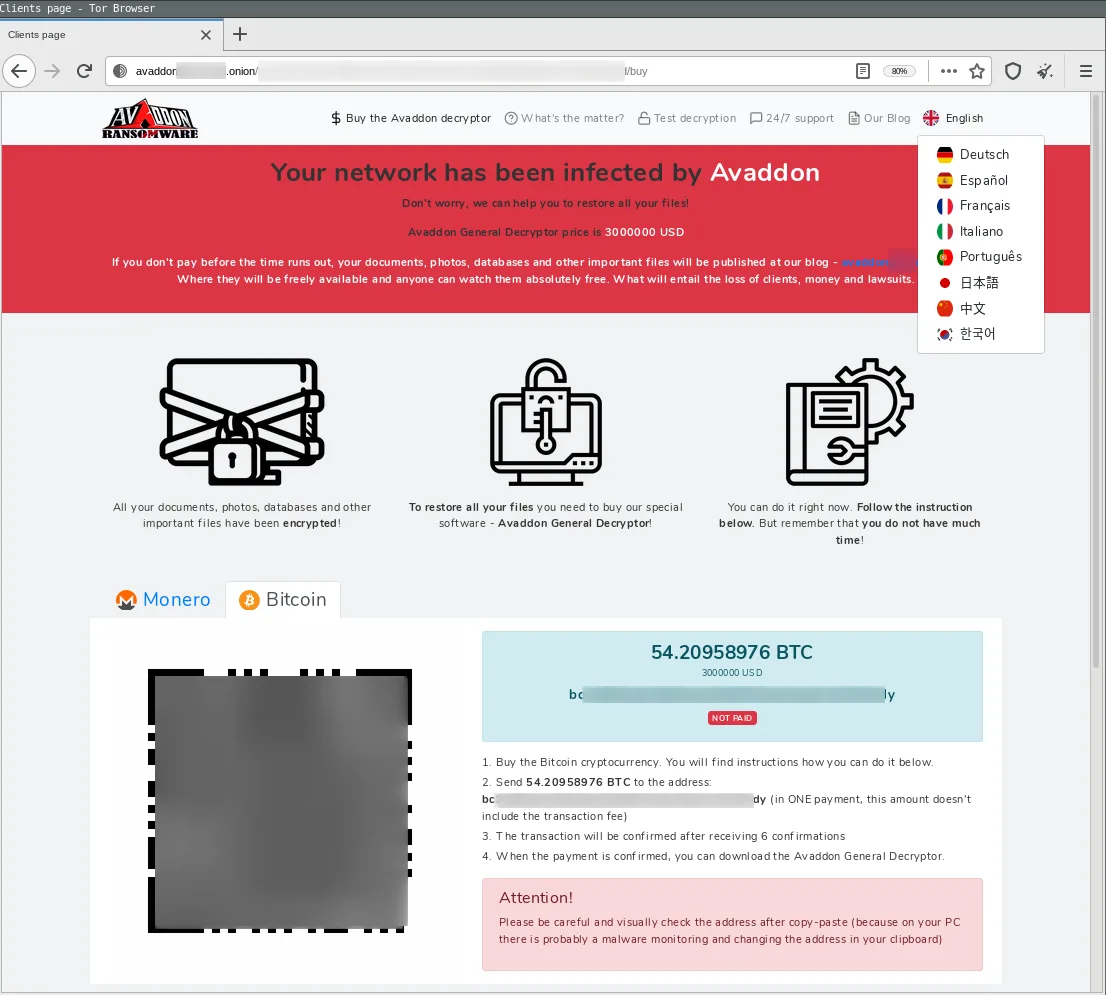
The demand above is addressed to a large company—and this is what is driving the difference in ransom demand. The threat actors will adjust the ransom to how much they think they can get. Thus, there are no clear figures when it comes to ransom demands. Sometimes ransomware threat actors will even analyze the financial documents found on a company’s internal network to discover how much ransom they can demand or how much the company’s cyber-insurance coverage for ransomware will pay.
Negotiation
For higher tier, human-operated ransomware, demanded amounts are often simply asking prices and are the basis for negotiation. The ransomware operators know that getting only a fraction of what they asked for is better than getting nothing. Hence, they are willing to negotiate.
Smaller automated ransomware pricing is mostly fixed, and if the ransomware operation offers ” support” at all, it is only provided to assist victims in obtaining the cryptocurrency needed to pay the ransom. The following are chat logs with the “support” of the Adhubllka (named after the .adhubllka extension it adds to encrypted files) ransomware. The ransomware executable was attached to the email within a ZIP file and distributed via the Phorpiex botnet in an unsophisticated but fully automated ransomware attack—in an identical fashion as the first Avaddon ransomware campaign we reported on.1
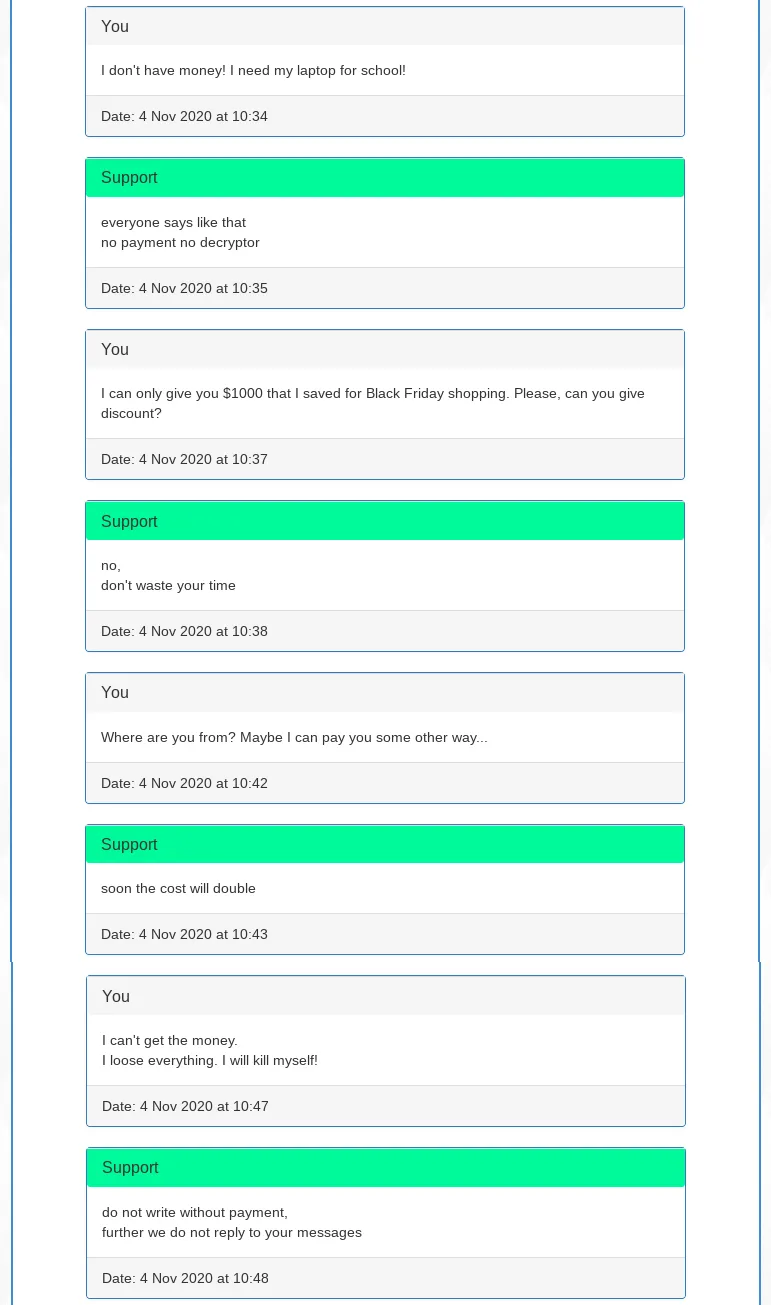
So while there is human-operated “support” even in low-tier mass delivered automated ransomware operations, this “support” is not entitled to negotiate. We traced the total earnings of their campaign, which were 0 BTC, so giving in to our fake demands for a discount would have potentially made them US $1,000. But as said, low-tier automated ransomware operations usually do not offer negotiations.
Putting pressure on ransomware victims
Some ransomware operators provide additional “services.” These are actions designed to pressure victims into paying the demanded ransom.
Leaksites
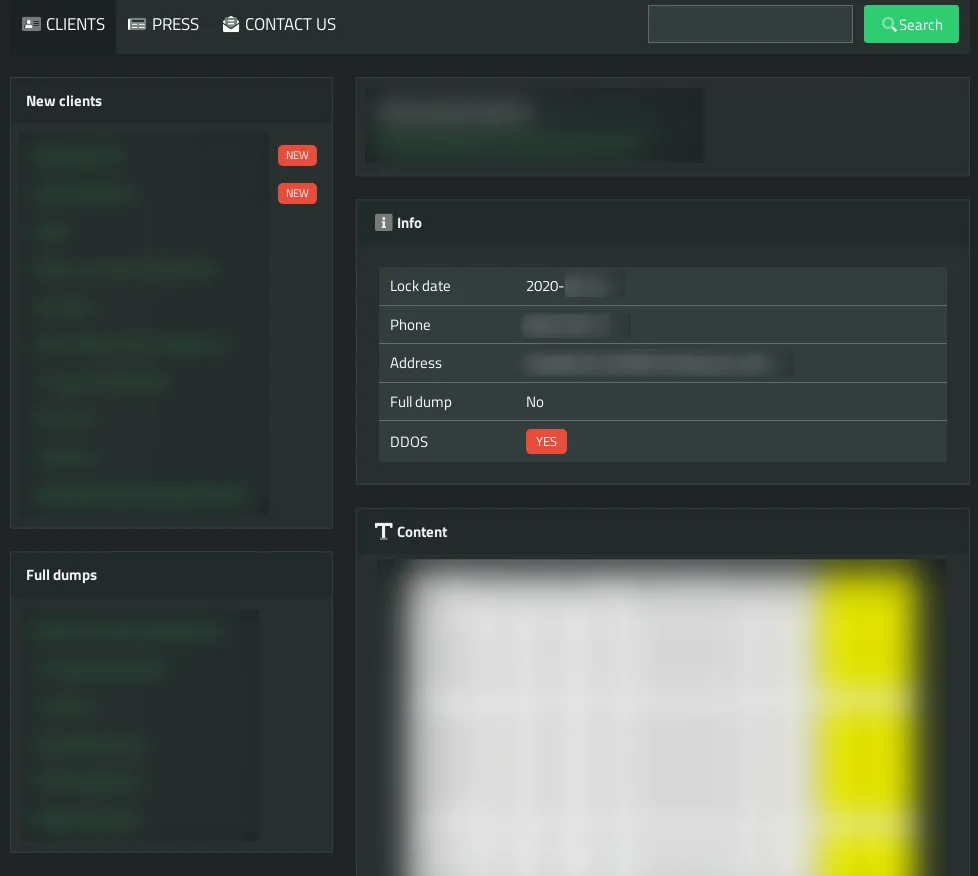
Ransomware leaksites are Tor hidden service websites on which ransomware threat actors threaten to publish data stolen from victim computer networks before encrypting them if the victim refuses to pay the ransom. We have reported on this practice.2
DDoS
Ransomware actors may also, in addition to the already existing issue with encrypted files, DDoS a victim network. One ransomware operation doing so is SunCrypt.
Harassing the victim’s customers and/or business partners
Another tactic is to “notify” the victim’s customers and/or business partners of the compromise. This can happen via spam emails—for example, the threat actors behind the Clop ransomware are using this tactic in the following message:
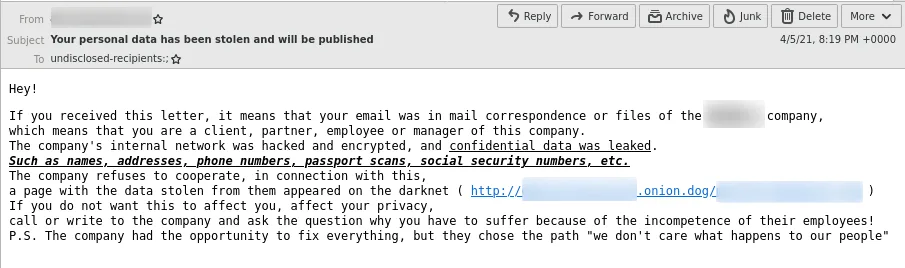
Spamming journalists and news outlets
Ransomware actors will also “notify” journalists and news outlets of the data breach with instructions on where to download the leaked data. Here is again an example of the Clop ransomware using this tactic.
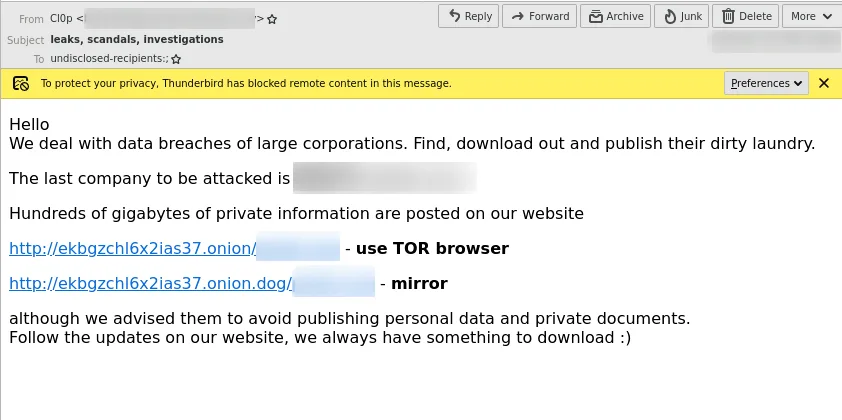
Notifying authorities
Some ransomware operations also threaten to inform the responsible data protection authorities about the breach if the victim does not pay the ransom. They will often cite the EU GDPR and the potential fines that authorities can incur for data leaks.
Prices for ransomware
The cost for a threat actor to acquire ransomware software varies. A threat actor can develop their own ransomware. This will only incur the development time as a cost. However, many criminals are technically unable to develop malware themselves or it is too much additional work. Alternatively, they can buy, rent, subscribe and/or partner with a ransomware developer and/or operator. To this end, the ransomware developer can sell the entire source code of their ransomware software for a one-time payment. However, this is often not attractive given the large ransom payments generated with such ransomware software. But demanding tens or even hundreds of thousands of US $ for the ransomware software may not get the software sold, as a ransom payment is not guaranteed.
To resolve this, ransomware as a service (RaaS) operations established themselves. A threat actor with access or means to access company networks can rent, subscribe and/or partner with a ransomware operation. The threat actor gets the ready-made ransomware software for deployment on victim computer systems. In contrast, the ransomware operator provides the ransomware software and—if available and/or necessary—the backend infrastructure for the ransomware, such as an online ransomware portal to support victims in buying and using the decryption software.
Like the demanded ransom, the price for ransomware varies. The entry price can be as low as hundreds of US $, as can be seen from the following example offers from the Egalyty ransomware.
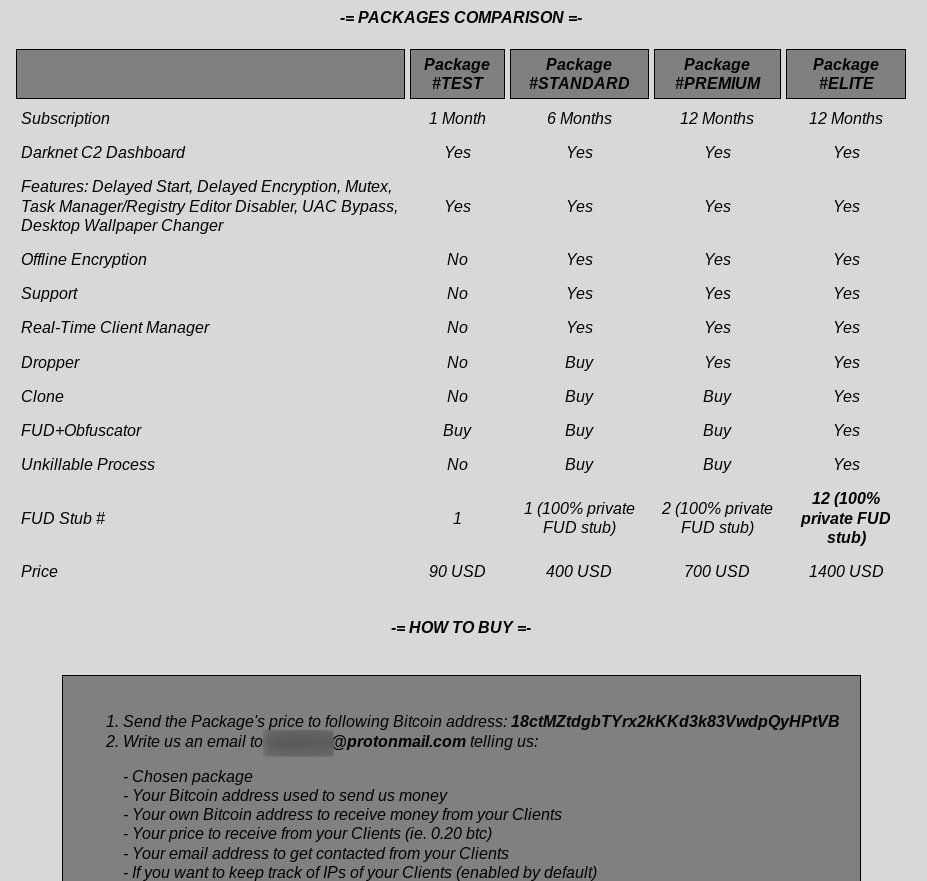
Profit-sharing affiliate schemes will split the paid ransom between the party supplying the ransomware and the party facilitating the intrusion. Also, here, the split ratio widely varies. While we have seen notices in cybercrime forums offering 90% of the ransom to the intruding party, this is not the norm.
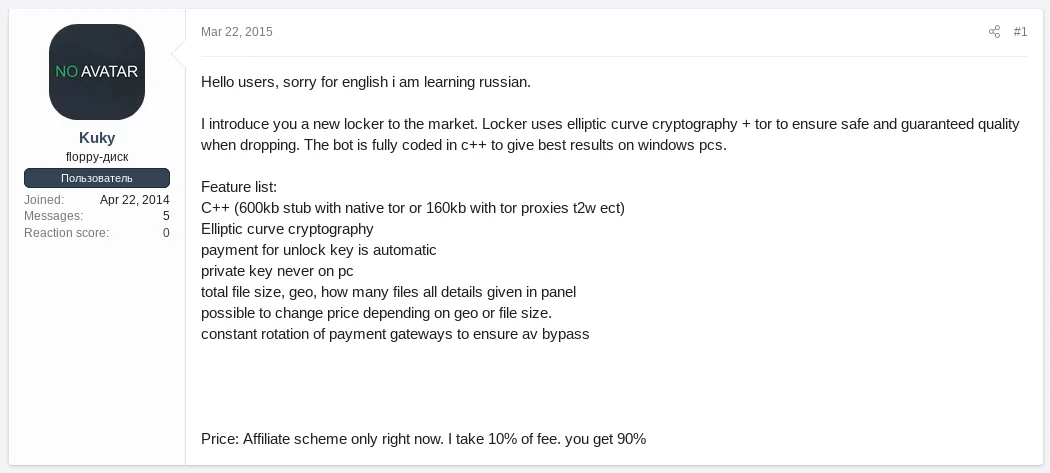
The usual reported split ratio for well-established ransomware affiliate programs only awards 10% to 30% of the ransom to the intruding party.
Conclusion and Countermeasures
These new developments in ransomware tactics make malware infections more dangerous to businesses than ever before. While good backups, preferably using the 3-2-1 backup strategy,2 helped against classic ransomware attacks, they do not provide any protection against private and/or confidential data being intentionally leaked to the public. The broad announcement of the data leak to business partners and customers will cause further damage and loss of reputation to victims, business partners, and customers. Worse still, competitors will also get unfettered access to internal documents, such as contracts, pricing, research, and development results. The media will start contacting the affected company, causing further stress in the ransomware crisis. Additionally, suppose the network is DDoS’d. It would be tough to recover from that situation, as this will likely affect any remaining network infrastructure a company might have to relay information, such as its public website.
Next, do not upload the ransomware that infected you to the Internet. Even though online services such as VirusTotal or other online sandboxes are convenient, they grant registered users access to the sample. The URL of the ransomware note may point at a “support” website that features an online chat for negotiation. These online chats are accessible to anyone with access to the data in the ransom note, thus everyone with access to the ransomware sample. So if you, in addition to all the other problems, do not want media outlets to leak your negotiation chat logs, keep your ransomware samples private. Or follow good practice and do not negotiate but share the ransomware sample with the security research community.
Paying a ransom is not recommended anyway:
1. The data breach remains. Even if a company pays to have the leaked data deleted, it must adhere to its respective breach notification laws.
2. Paying a ransom to a threat actor located in a country on sanction lists can violate trade and/or export sanction laws and cause the victim even more trouble in the long run.
3. There is no guarantee of decryption nor that leaked data is deleted.
Once leaked data has already been downloaded from the leaksite, there is no way to contain the leak.
Hornetsecurity, with its cloud offerings, can help organizations to prepare and prevent ransomware. Hornetsecurity’s Spam Filtering Service and Malware Protection, with the highest detection rates on the market and Hornetsecurity’s Advanced Threat Protection can detect and quarantine email-based malware attacks before they can lead to a ransomware infection. Hornetsecurity’s Email Archiving is a legally compliant, fully automated audit-proof email archiving solution for long-term, unchangeable and secure storage of important company information, data, and files. This way, important communication cannot be destroyed by ransomware.
But even if your company is affected by ransomware, offerings such as Hornetsecurity’s Email Continuity Service will keep your email communication available if ransomware has put your local mail server out of service.


