

Monthly Threat Report February 2024: A Month for Breaches and Ransomware
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data gathered from the month of January.
Executive Summary
- Low-effort – high-volume email attacks continue to abate, while more targeted complex email attacks are on the rise.
- There has been a near universal increase in the use of malicious file attachments, likely driven by the noted increase in more complex attacks.
- HTML, PDF, and Archive files were the top 3 most used file types for malicious payloads over the data period.
- Most targeted industries for the month of January were Mining, Media, and Manufacturing, with the Research industry coming in at a VERY close 4th place.
- FedEx was the single most impersonated brand during this month’s report, while we also saw notable increases in brand impersonation for both Amazon and Facebook.
- The threat actor group dubbed “Midnight Blizzard” by Microsoft was able to access and ex-filtrate Microsoft executive team emails. The industry has been reacting with some questioning Microsoft’s response to the breach.
- Remote Access Provider AnyDesk has reported a breach that led to the theft of code signing keys. Customers need to apply the latest patches ASAP to ensure the continued safe operation of the application.
- Johnson Controls fell victim to a significant ransomware attack with costs to recover totaling $27 Million USD.
- The Midnight Blizzard breach of Microsoft highlights the dangers of malicious OAuth applications and it’s recommended that system admins review their currently used OAuth apps in M365 as well as the settings associated with who is able to approve OAuth apps within the environment.
- M365 users looking to enable Co-Pilot for the first time are urged to review permissions within their M365 tenant (including for SharePoint Online, Teams, and OneDrive for Business) before enabling the feature. The ease with which Co-Pilot can surface information could lead to potential data leaks within the company in the presence of permission misconfiguration.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for December 2023 compared to January 2024.
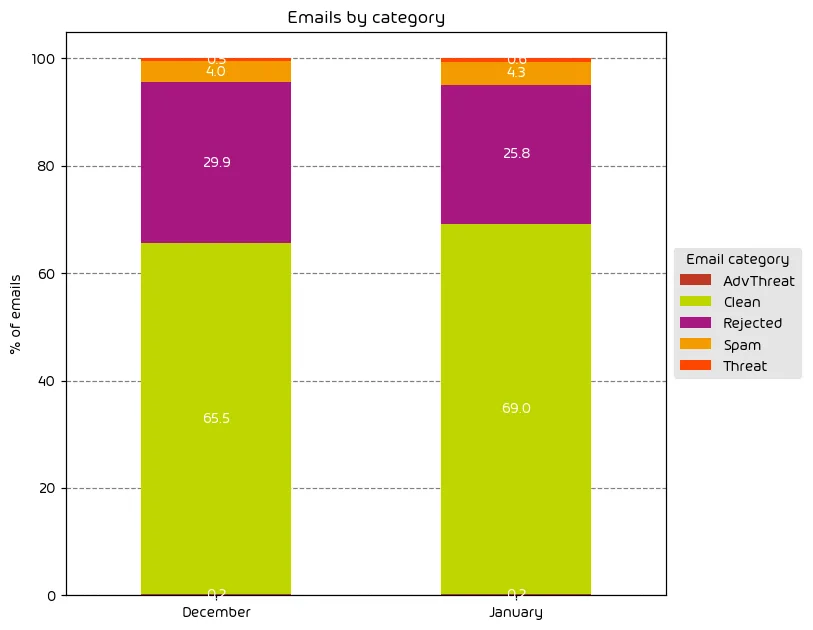
Our data from this data period continues the expected trend of the overall number of email attacks decreasing after the holiday season. That said, the number of targeted email attacks (those classified as “Threats” and “AdvThreats”) saw a slight increase for the month. This is indicative of the fact that with the holidays over, threat-actors are relying less on low-effort, high-volume email attacks (typically classified as “Rejected” in our data) and have moved to more targeted campaigns.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
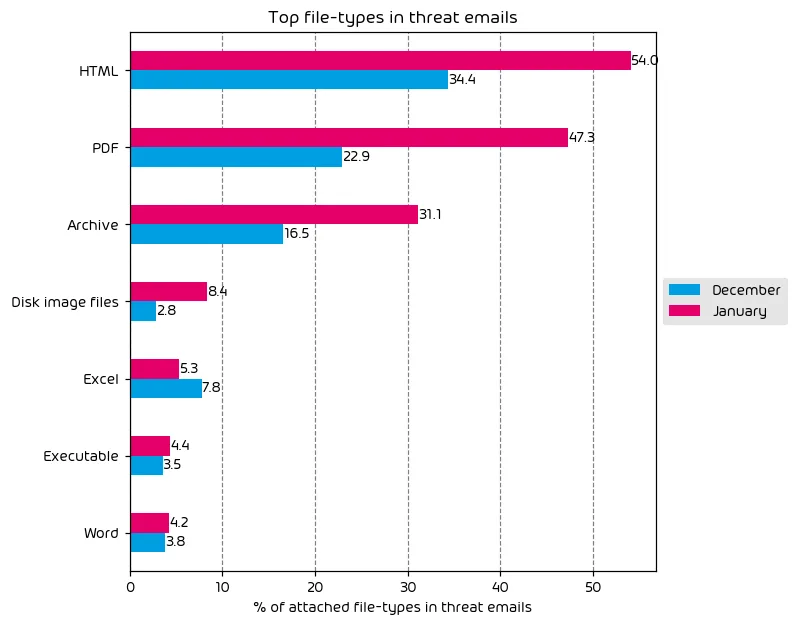
Along with the increase in targeted attacks, we’ve also seen an increase in the use of HTML, PDF, and Archive files for the delivery of malicious payloads. Targeted attacks are often more complex, with the attacker looking to more complex methods, including malicious attachments. With that in mind, it’s not surprising to see an increase in the use of malicious attachments when we see an increase in more advanced threats during the same data period.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percentage values for all organizations within the same industry to form the industry’s final threat score.
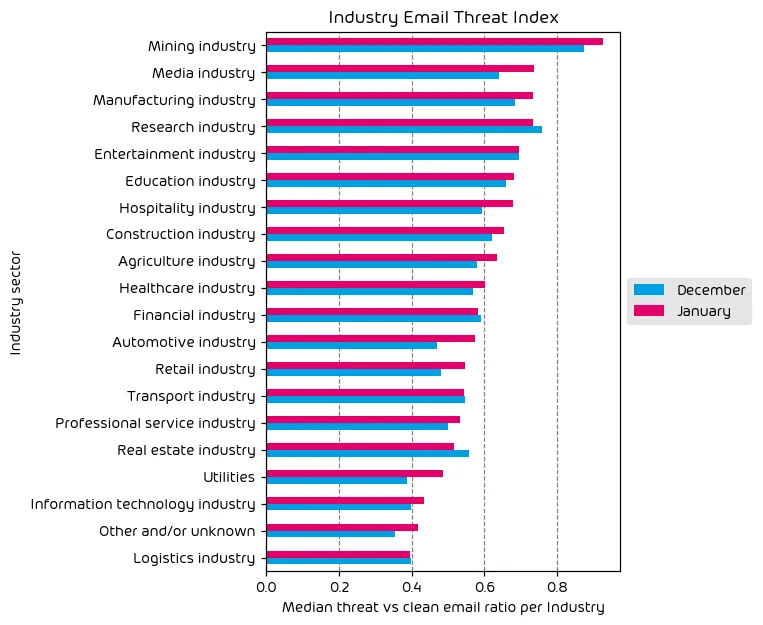
Our data for this month has shown that some industries have seen an increase in the amount of malicious/unwanted email vs clean emails. The Mining, Media, and Manufacturing industries topped the list this month, with the research industry in a very close 4th place. The core story that the data shows this month, is that despite a decrease in overall email threat volume, the email security landscape remains dangerous.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
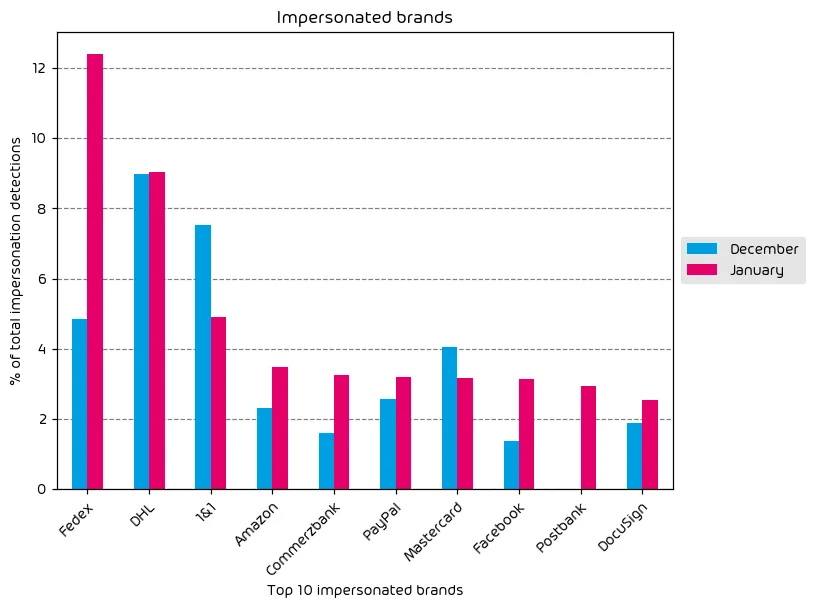
In terms of top impersonated brands, we have some interesting changes this month when compared with last month’s report. The shipping company DHL was long the topmost impersonated brand, but a recent impersonation campaign involving FedEx has seen the number of FedEx brand impersonation emails skyrocket. In other changes, Facebook and Amazon saw notable impersonation increases, while Mastercard saw a decrease during this data period, likely due to the end of the holiday season. Also worth noting is the slight increase in DocuSign brand impersonations. As tax season nears in the US, threat actors know that more eyes will be on DocuSign emails in the coming months and threat actors are pivoting predictably.
Major Incidents and Industry Events
Midnight Blizzard
According to this MSRC blog post, Microsoft detected a nation-state attack on its corporate systems on January 12th, 2024. The threat actor was identified as the Russian State-Sponsored actor Nobelium and given the code name “Midnight Blizzard”. In a notice providing a bit more detail on the attack, Microsoft states:
Midnight Blizzard utilized password spray attacks that successfully compromised a legacy, non-production test tenant account that did not have multifactor authentication (MFA) enabled.
This statement has brought up a number of questions for security professionals over the past couple of days.Why was this “Legacy, Non-Production Test Tenant” still being used?
- Why was this “Legacy, Non-Production Test Tenant” still being used?
- Why was MFA not enforced on this tenant leading it to be compromised by a password spray attack?
- Why did this test tenant have any rights to the Microsoft corporate tenant?
- How did internal red teaming processes NOT discover the linkage between the two tenants?
- How did Midnight Blizzard accomplish infiltration from the “Test Tenant” to the corporate network?
We at least got an answer to one of these four questions later in the same article:
Midnight Blizzard leveraged their initial access to identify and compromise a legacy test OAuth application that had elevated access to the Microsoft corporate environment. The actor created additional malicious OAuth applications. They created a new user account to grant consent in the Microsoft corporate environment to the actor controlled malicious OAuth applications. The threat actor then used the legacy test OAuth application to grant them the Office 365 Exchange Online full_access_as_app role, which allows access to mailboxes.
This attack method highlights the risk of OAuth applications that we’ve talked about here at Hornetsecurity, including the podcast episode embedded below. Microsoft themselves have even cited the risk posed by malicious and uncontrolled OAuth apps but seems to have fallen victim themselves in this case.
Ultimately this incident has led to the ex-filtration of Microsoft Executive team emails, and there are those in the security community that are speculating that the blast radius will become larger in the coming days. The possibility of a proper cultural shift in security at Microsoft seems to be woefully needed.
The Security Swarm Podcast – The Dangers of Malicious OAuth Applications
AnyDesk Breach
Popular Remote Access solution creator AnyDesk has also experienced a major breach. According to an article from Bleeping Computer, this breach led to the theft of source code and private code signing keys. In their official statement AnyDesk stated that situation is under control and that the application is safe to use with the latest update which provides an updated code signing certificate. AnyDesk claims that no passwords were stolen as part of the attack but is recommending that AnyDesk users change passwords if they have not done so already.
This incident highlights the fact that any and all IT toolkits are under attack by threat actors in an attempt to pull off another impactful supply chain attack like the Solarwinds supply chain attack years ago. It’s also worth highlighting the fact that source code was stolen in this incident. With this in mind it’s feasible we could see other AnyDesk targeted attacks in the coming days once threat-actors have a chance to look over code.
Johnson Controls Ransomware Attack Cost the Company $27 Million
The cost associated with ransomware attacks continue to rise. So, it’s sadly becoming more common that we see successful ransomware attacks associated with an eye-watering dollar amount. The good news (if there is any to be had in this story) is that $27 Million USD was not used for paying a ransom. According to reports on the web, the $27 Million was used to restore affected systems while also taking cyber insurance payouts and external cybersecurity professional services into account.
This story was worth including in this month’s report for one simple reason. So often the monetary damage associated with a ransomware incident is attributed to a ransom payout. So often the astronomical cost of a ransomware incident is caused by the mere act of having to address the damage of the attack. This is one of the reasons that cyber insurance has become so expensive in the past couple of years. It is EXPENSIVE to deal with an extensive and targeted ransomware attack. A fact that far too many organizations realize once it’s too late.
Predictions for the Coming Months
- With the holiday season well behind us now, we’re likely to see a return to “business as usual” for threat actors. That said, with tax season coming up in the US we’ll likely see attackers make a more targeted effort to inject themselves into the tax season to capitalize on the exchange of Monday and sensitive info.
- We expect the fallout of this most recent Microsoft breach to become clearer in the coming days. As that process plays out, more details will emerge about threat-actor activities leading to the breach, as well as how other entities have been impacted as a part of this incident.
- Co-Pilot for Microsoft 365 has been released and provides tremendous capabilities in surfacing stored M365 data to end users in prompts. We’re likely to see emerging cases where misconfigured permissions in SharePoint Online, Teams, and OneDrive for Business lead to the accidental exposure of data within organizations using Co-Pilot for the first time, raising the concern of insider threats.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on Microsoft’s Security Culture:
I want to start by saying that I’m often the first to give the benefit of the doubt in these situations – especially so with Microsoft due to my involvement with the Microsoft MVP program over the years. However, the recent breach of Microsoft executive emails by Midnight Blizzard paired with other recent security lapses such as that caused by Storm-0558, really brings the security culture at Microsoft into question. There have been repeated security issues at Microsoft over the past several years now and the community has been waiting for clear acknowledgement that there is a systemic problem to be solved. While the SFI (Secure Future Initiative) is a step in the right direction, it still lacks the impact of the trustworthy computing memo that came directly from then CEO Bill Gates some 20+ years ago. Time will tell if the SFI has the same level of impact within the organization.
From Yvonne Bernard, CTO Hornetsecurity on Copilot:
Walled-off generative AI like Copilot is the often searched for possibility to enhance productivity with a well-defined training data scope. Nearly every business I am talking to nowadays is currently testing it. I believe this is just the beginning and future applications are endless to help employees and companies work more efficient. However, the risk of misconfiguration, hacked accounts etc is probably not in everyone’s mind yet so I strongly advice to invest into employee training on AI and data protection and the definition of proper AI policies prior to rollout.
Monthly Recommendations from the Hornetsecurity Security Lab
- The Midnight Blizzard breach shows us that now is a good time to re-evaluate your current list of OAuth applications within your M365 environment. Remove any apps that your organization no longer uses and verify that the users allowed to approve OAuth applications are tightly controlled and configured for least possible access, given business needs.
- If you use AnyDesk within your organization, make a plan to apply the latest patches ASAP if you have not already done so.
- If you plan on enabling Co-Pilot for M365 within your M365 environment discuss and make a plan around the potential governance and data safety issues that this new product may surface. If you’re looking for an easy solution to this problem, a trusted permissions management tool like 365 Permission Manager can help.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


