

Email Threat Review November 2022
Executive Summary
Emotet started to use social engineering tricks to bypass Microsoft’s recent macro restrictions for documents downloaded from the Internet.
Summary
In this monthly email threat review installment, we present an overview of the email-based threats observed in November 2022 and compare them to the previous month’s threats.
The report provides insights into the following:
- Unwanted emails by category
- File types used in attacks
- Industry Email Threat Index
- Attack techniques
- Impersonated company brands and organizations
- Highlighted threat email campaigns
Unwanted emails by category
The following table shows the distribution of unwanted emails per category.
| Email category | % |
| Rejected | 86.29 |
| Spam | 10.28 |
| Threat | 2.45 |
| AdvThreat | 0.98 |
The following histogram shows the email volume per category per day.

Many rejected emails around 2022-11-14 to 2022-11-16 were related to an extensive periodic reoccurring sextortion scam campaign targeting German-speaking victims.
Methodology
The listed email categories correspond to those listed in the Email Live Tracking of Hornetsecurity’s Control Panel. So our users are already familiar with them. For others, the categories are:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File types used in attacks
The following table shows the distribution of file types used in attacks.
| File type (used in malicious emails) | % |
| HTML | 31.3 |
| 25.8 | |
| Archive | 20.3 |
| Excel | 6.7 |
| Executable | 5.2 |
| Word | 4.1 |
| Disk image files | 3.5 |
| Script file | 0.5 |
| Other | 2.6 |
Despite the efforts of Microsoft to make Excel documents less attractive for attackers by disabling macros in documents downloaded from the Internet by default, malicious Excel documents made a comeback. The previous month the use of malicious Excel documents in attacks was in decline. However, Emotet started to use Excel macro documents despite Microsoft making it less attractive for attackers by combining it with a social engineering attack to bypass Microsoft’s mitigation. We outline this social engineering component in the highlighted threat email campaigns section.
Industry Email Threat Index
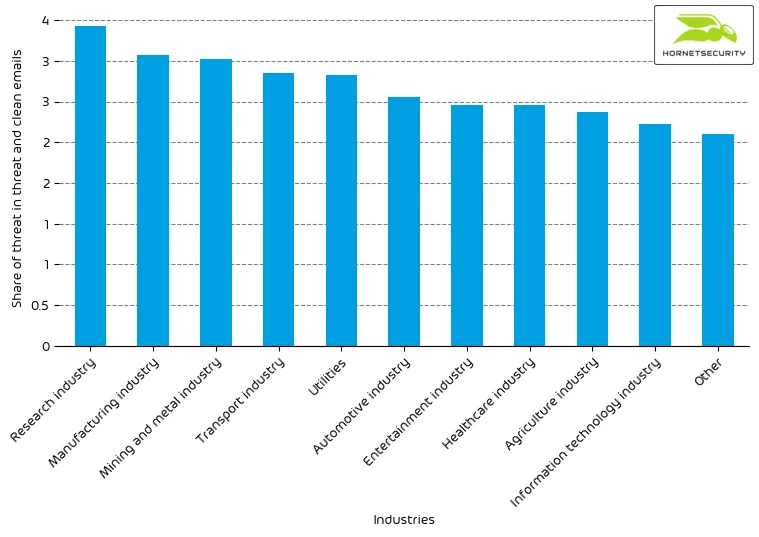
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median).
| Industries | Share of threat in threat and clean emails |
| Research industry | 3.9 |
| Manufacturing industry | 3.6 |
| Mining and metal industry | 3.5 |
| Transport industry | 3.4 |
| Utilities | 3.3 |
| Automotive industry | 3.1 |
| Entertainment industry | 3.0 |
| Healthcare industry | 3.0 |
| Agriculture industry | 2.9 |
| Information technology industry | 2.7 |
The following bar chart visualizes the email-based threat posed to each industry.
Methodology
Different (sized) organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
Attack techniques
The following table shows the attack techniques used in attacks.
| Attack technique | % |
| Phishing | 26.2 |
| URL | 14.2 |
| Extortion | 6.3 |
| Advance-fee scam | 4.8 |
| HTML | 3.0 |
| Executable in archive/disk-image | 2.7 |
| Impersonation | 2.5 |
| Maldoc | 1.7 |
| 0.6 | |
| Other | 38.0 |
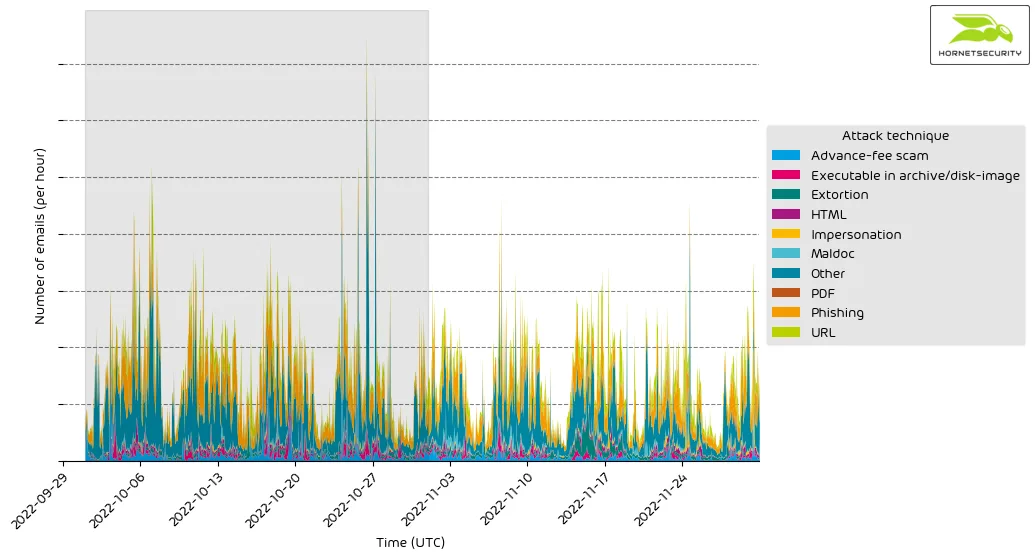
The following histogram shows the email volume per attack technique used per hour.
Impersonated company brands and organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
| Impersonated brand or organization | % |
| DHL | 12.8 |
| Postbank | 9.4 |
| Amazon | 9.4 |
| Sparkasse | 7.1 |
| 3.9 | |
| Microsoft | 3.2 |
| DocuSign | 3.0 |
| Strato | 2.8 |
| Fedex | 2.6 |
| Other | 45.8 |
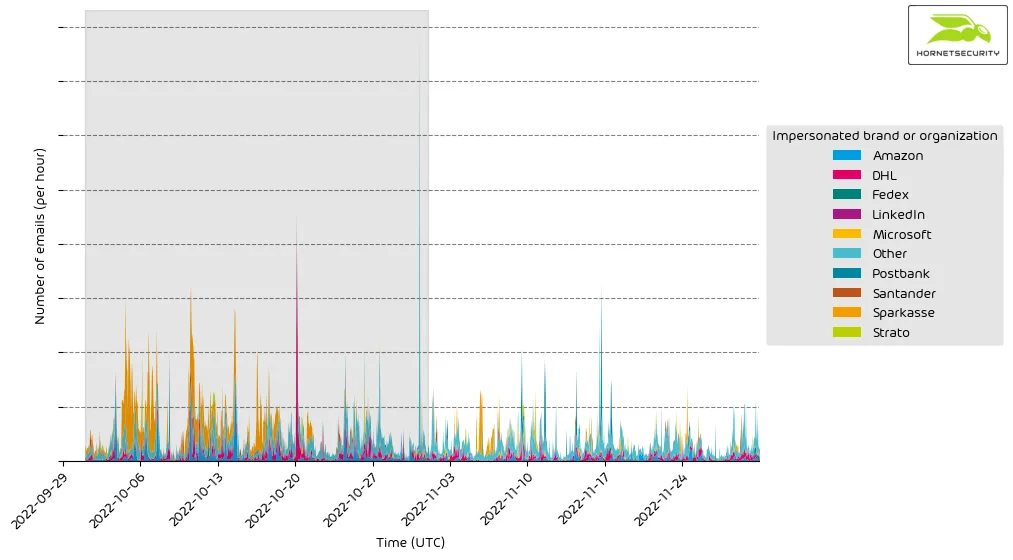
The following histogram shows the email volume for brands and organizations detected in impersonation attacks per hour.
Highlighted threat email campaigns
Previously many attackers, including the threat actors behind Emotet, stopped using macro documents. This is likely because Microsoft started disabling macros from documents downloaded from the Internet in their Office products per default. Attackers used other malicious files such as shortcut files (.lnk) or HTML files instead. Despite this, Emotet started to use malicious macros in Excel documents again this month. They used email conversation thread hijacking attacks as well as generic emails. However, the attached malicious Excel documents contain social engineering to bypass the macro restrictions imposed on documents downloaded from the Internet. To this end, the malicious document will tell the victim to copy the document to the Microsoft Office Templates folder. This Templates folder is a trusted location from which Microsoft Office will allow macros in the document again.
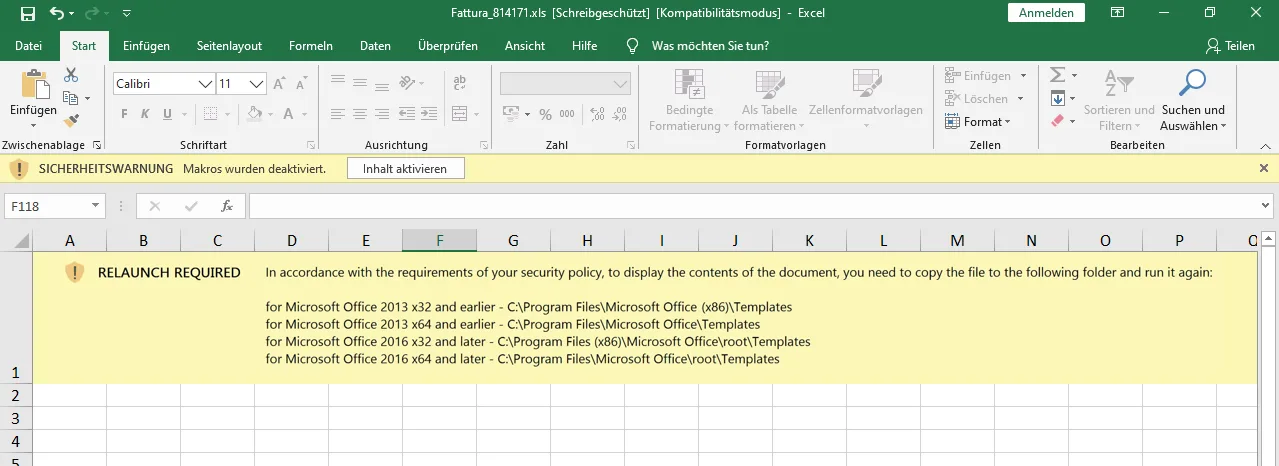
Like older Emotet macro documents, the macros will download the Emotet malware and execute it on the victim’s system.
Methodology
Hornetsecurity observes thousands of threat email campaigns of varying threat actors ranging from unsophisticated low-effort attacks to highly complex obfuscated attack schemes. Our highlighting includes only a subset of those threat email campaigns.


