

Monthly Threat Report January 2024: Holiday-Focused Attacks on the Decrease, but Danger Remains
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data from the month of December 2023.
Executive Summary
- More advanced email threats are down during this data period, while we’re seeing slightly more low-effort email attacks that are ultimately rejected due to external indicators.
- We saw a reduction in the use of most file types for the delivery of malicious payloads. Despite the noted decreases, HTML, PDFs, and Archive files remain the top three offenders.
- The Mining, research, and entertainment industries were the most targeted industries during the data period.
- Brand impersonations are down, with DHL remaining the number one most impersonated brand.
- The MOVEit supply chain attack continues to rack up victims, and now that a considerable amount of time has passed, the industry is starting to get a clearer picture of the true scope of the damage
- The Albanian government and One Albania Telecom are currently under active attack by the Iranian hacking group “Homeland Justice.”
- We’re seeing new phishing campaigns targeting both Instagram and Twitter (X) users with the goal of account takeover or access to crypto wallets and other account assets.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for December 2023 compared to November 2023.
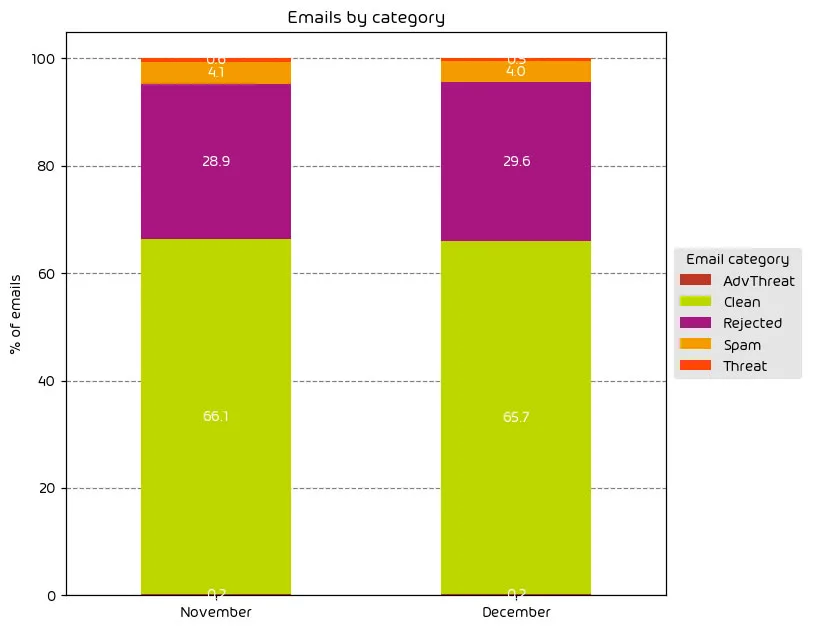
The past several months saw a recurring increase in malicious mail traffic, which we see every year around this time. We can attribute this increase to the holiday shopping season. With the holidays now over, it’s no surprise that we’ve seen the trend nearly plateau. Those emails categorized as “threats” and “AdvThreats” saw a decrease. The slight increase in those emails categorized as “rejected” drove a slight decline of 0.4% in “clean” emails. During the lead-up to the holidays, we see an increase in low-effort email attacks in the hope of capitalizing on holiday traffic. These types of attacks are frequently rejected outright due to external indicators. With the holidays now over, we expect this downward trend to continue for the time being.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
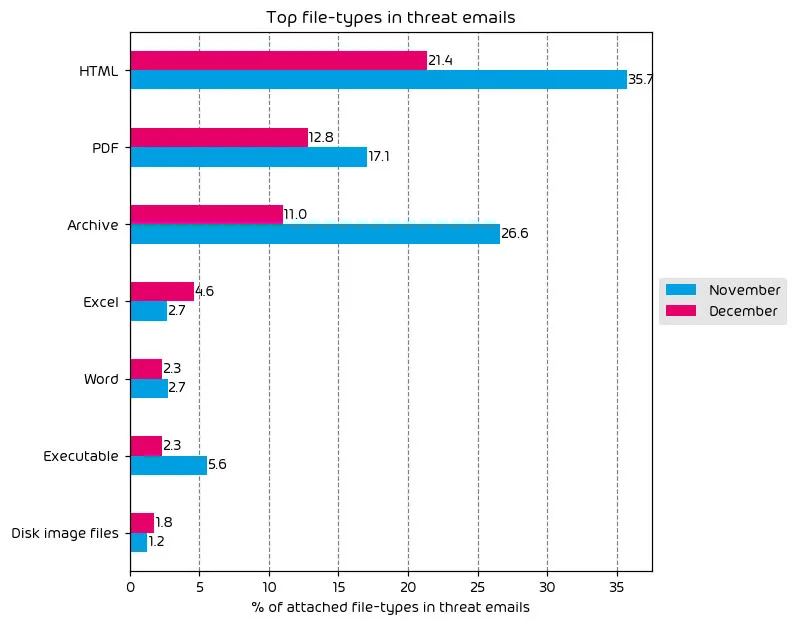
During this data period, we saw a net reduction in nearly every category. We attribute this to the observed reduction in the number of more sophisticated email attacks during the data period. Even so, HTML, PDFs, and Archive files remain the top three most used attachment types for delivering malicious payloads.
The noted increase in Excel files may seem like a noted campaign, but it’s not. We saw fewer attacks involving Excel documents during the data period when we looked at specific numbers. That said, when accounting for all file types in this category, Excel files saw a much smaller reduction, and due to the massive decreases in other categories, it appears as a percentage point increase in the data due to emails with malicious Excel files simply comprising a larger piece of the data set this month. Hence, it appears as an increase.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
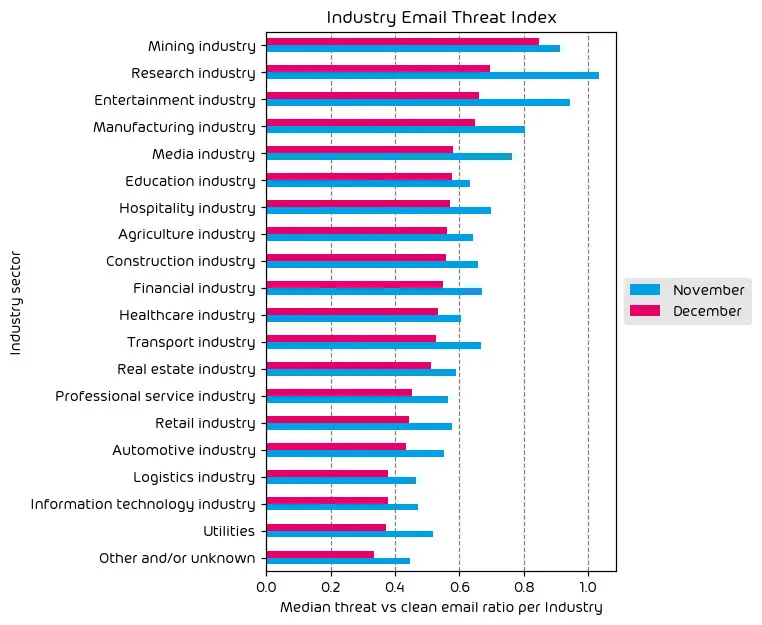
As expected, we saw a decrease in the threat index across all industries during the month of December. This lines up with our other data regarding the decrease in the amount of threats. In terms of the top targeted industries, the mining, research, and entertainment industries remained at the top.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
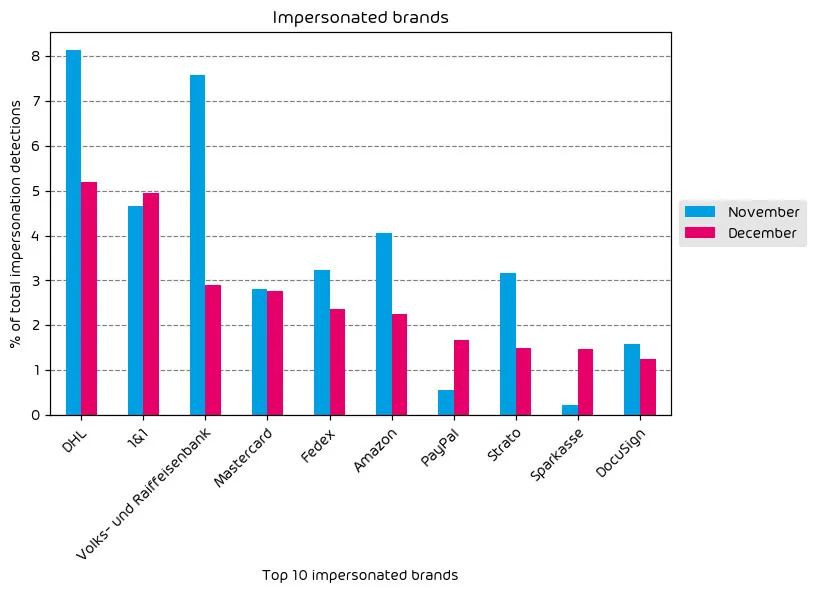
Like our other data sets listed above, we see evidence here of a decrease in the number of threats. Nearly every brand in our top ten most impersonated brands saw a decline with a few exceptions – notably Paypal and Sparkasse. According to our data, DHL remains at the top of the list as the most impersonated brand used by threat actors.
Major Incidents and Industry Events
MOVEit – The Damage So Far
We’ve discussed the MOVEit zero-day attack in several of these monthly reports. The damage is apparent, and the real-world harm is VERY real. That said, it takes time to get an accurate scope of large supply-chain attacks of this nature. Thankfully, enough time has passed for some gathered data regarding the event to start showing an interesting picture. Kon Briefing has compiled a data collection regarding the MOVEit supply chain attack. The report includes several useful data points, including:
- Victims
- Impacted Individuals
- Most targeted countries
- Affected organizations
- Links to official disclosures
- And more
US-based companies are at the top of the list for exploiting this vulnerability. Impacted US organizations number 2290, with the following most targeted country being Canada with 152 affected organizations. Perhaps the most jaw-dropping statistic is the fact that upwards of 90 MILLION individuals have been directly impacted as a result of exploitation. Yes, A fix exists, but it’s clear that many impacted organizations have been slow to roll out the needed patches. Whether this is due to negligence or overburdened IT departments remains to be seen. Time will tell; in the meantime, we expect the MOVEit supply-chain attack to remain an issue in the industry for some time.
Albanian Government and Telecom Hit By Cyberattacks
We always take note of major cyber attacks, especially when the target is a nation-state government. It’s been reported that both the Albanian government and One Albania Telecom have been under active attack in a cyber attack of unknown size/scope. This is notable due to the impact size (1.5 million in just one Albania Telecom). Still, it also serves as further confirmation of the trend we’re seeing where nations states’ digital infrastructure is under attack at a level we haven’t seen before. As of the time of this writing, the attack is ongoing, with the Iranian hacker group Homeland Justice taking responsibility for it.
Attacks will draw the attention of world governments as it becomes increasingly apparent that government regulation may ultimately be required to help stave off the wave of rising cybercrime. We’ve discussed the topic of government technology intervention in previous editions of this report and will continue to report on it in future instances as needed.
New Emerging Instagram Phishing Campaign
The industry saw a new Instagram Phishing campaign emerge just in time for Christmas. Target recipients are shown several convincing UIs that walk them through entering one of their 2FA backup authentication codes which the threat-actor then uses to take over the account. Marketing and social media departments will especially want to be on the lookout for this over the coming days.
The phishing email will claim that the account in question is “infringing on copyright.” The sender’s email address, instagram@contact-helpchannelcopyrights.com, even directly supports that claim. As the article states, the convincing UIs and the sense of urgency can make this a tough spot for some novice users.
Twitter’s (X) Status ID handling is Being Used to Forge Phishing Links
A new round of phishing attacks are making their way around the net. This time via Twitter (Now known as X). Due to how X handles status IDs, the username portion of an X URL can be replaced with any string, and the post that the status ID pertains to will still be opened regardless of the username change in the URL.
For example, if you got to the URL: https://twitter.com/hornetsecurity/status/1733207135247303132#, you would think you’d be navigating to the official Hornetsecurity X Page right? However, you’ll quickly find that it takes you to a post from our security evangelist Andy Syrewicze’s X profile. This is apparently a “feature” of how X works, but it can lead to phishing attacks by bad actors.
Many phishing attempts are making the rounds that use this technique to make the target think they’re being directed to a legit X post from large brands like Binance, the Ethereum Foundation, Chainlink, and other cryptocurrency-related entities. The goal for threat actors here is to gain access to the target user’s crypto wallet and drain it of assets. This is just another area where your average Joe user needs to be trained to make sure the page (or X profile) they’ve ended up at is indeed the legit profile they expect it to be.
Thankfully, most users capable of playing crypto tend to be tech-savvy, but even the most experienced user can be caught off guard. This type of phishing attempt via X could be used for other things as well, such as phishing credentials from other (non-crypto) services to be then used as part of credential stuffing attacks. This is not to mention the potential use for misinformation as well. Time will tell how threat actors make use of this method.
Predictions for the Coming Months
- While we expect the danger of the email threat landscape to remain high, the number of email-based attacks is likely to decrease somewhat as we move away from the holiday season.
- With the number of potential targets looking for holiday shopping and shipping emails decreasing, it’s feasible that the number of sophisticated email-based attacks will increase over the coming months as threat actors return to their “regularly scheduled programming.”
- The targeting of nation-state governments will continue, driving the international conversation about the government’s role in the security community.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Yvonne Bernard, CTO Hornetsecurity, on Instagram and Twitter(X) attacks:
It is interesting to see that attackers do not take vacation but rather tailor their attacks to the Christmas season: fake Instagram and Twitter(X) emails catch users when they are more active on social media, DHL and other transport industry phishing attempts use the greediness of the holiday shopping season – no surprise as everyone is waiting for their presents to arrive! It is good to know that our Security Lab is alert and protecting our customers 24/7 – if evil does not take a vacation neither do we!
From Umut Alemdar, Head of Security Lab, on Phishing and Fake Online Stores:
Looking back at December 2023, we witnessed a significant increase in phishing threats, capitalizing on the holiday shopping season. Scammers cleverly created fake online stores, targeting last-minute holiday shoppers. As we move into January, it is crucial to maintain vigilance. The risk of encountering these scams does not vanish with the holidays; leftover fake deals and cleverly disguised emails may still circulate. Therefore, it is advisable to remain skeptical of overly attractive offers and always verify the legitimacy of online stores before making purchases or sharing personal information. The start of a new year is a good time to reinforce safe online practices to protect against phishing threats.
Monthly Recommendations
- It’s a good time to revisit security awareness training with end-users. After the holidays and extended vacations, a friendly reminder of the dangers that lurk in mailboxes can help get workers on the defensive again as we move into the new year.
- Train your social media and marketing teams about the newly emerging phishing threats on both Instagram and X.
- If your organization uses the MOVEit file transfer software and you still need to apply the patches to fix last year’s major supply chain attack, plan to do so now.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


