

The Value of a Single Third-Party Vendor Strategy for M365 Security
Cybersecurity is an interesting space to be in, because it’s changing so fast. This, combined with the serious risk criminals pose to businesses worldwide leads to fast innovation, with cyber security start-ups springing up, offering solutions to specific problems.
For quite some time, this meant that businesses and CISO / CIOs looked for the “best” solution for each particular cyber security problem (and there are a lot of them). This worked for some organizations with deep enough pockets to operationalize each of these disparate solutions, but it also led to the famous quip – CIO doesn’t mean “Chief Information Officer”, it’s “Chief Integration Officer”. But attackers are like a water leak, they find any crack and move with ease between systems.
The current trend in cyber defense is thus not to deploy specific solutions for each gate of the castle that needs defending, and then try to cobble them together in the backend as one integrated defensive system, using Security Orchestration Automation and Response (SOAR) tools. Instead, you buy an already integrated system from a single vendor, improving your overall cyber defense, because defenders don’t have to jump between screens, manually correlating alerts in one system, with further alerts in other siloed systems.
In this article we’ll look at the value of this approach, in the context of our solution – Microsoft 365 Total Protection. Microsoft 365 is the business world’s most popular collaboration suite, with many, many components suitable for any size organization. The core workloads are email through Exchange Online, collaboration in Teams and SharePoint Online, backed by identities in Entra ID.
The Defenders Dilemma
The old saying in cyber security is that “defenders must get it right, every single time, whereas attackers only need to get it right once”. And that then leads to another common human trait, if you have lots of things you need to do and keep track of in your personal life – what do you do? You make a list, preferably a checklist, so that you can inspect every task, make sure it’s been done and tick it off the list.
That then leads to the second famous saying, “defenders think in lists, attackers think in graphs” (John Lambert). A business might have to comply with a particular compliance regulation, they prepare, tick every task off the list, pass the audit and then sit back, comfortable in their knowledge that they have secured every possible attack vector. And then they’re surprised when the criminals simply pay the help desk staff $3000 to give them admin access, or the business is compromised because one of their software / service suppliers were owned.
Because attackers think in graphs, they move from one compromised system or identity to the next that’s easiest to attack, and they’ll happily pivot from on-premises to the cloud (or vice-versa), or from database servers to file servers for example.
This is the reality of cyber-attacks today, and it requires a more integrated approach to your defenses for Microsoft 365. You need a layered approach that covers compliance requirements, data protection, backup and security awareness training for end users. If you use different vendors for each of these, you end up with multiple portals, the integration challenges we’ve already mentioned, plus higher training costs and the risk of miss configuration. It’s a well-known “secret” in the cyber security industry, that security controls often fail, not because the organization hadn’t thought of the risk, but because the implemented control was misconfigured, and to mitigate this risk requires more staff training in each separate product, leading to higher costs.
The benefits of a single vendor approach
By consolidating your Microsoft 365 security needs in a single suite, from a single vendor independent of Microsoft, you’ll be able to:
- Eliminate the need for costly, complex, bespoke integration between disparate systems
- Reduce the time from identified threat to contained attack due to simplified correlation of signals
- Reduce training needs for your administrators
- Considerably simplify licensing
- Maximize resource allocation for enhanced productivity
Strong cyber security resiliency comes from a layered approach, covering all the different components of the system, in this case Microsoft 365. For example, to protect against incoming malicious emails you have basic protection that catches “run of the mill” attacks, followed by an advanced solution that contains customized attacks and in the rare case that both these layers fail, you continuously train your users to be suspicious, so they can catch and report the few that slip through.
365 Total Protection
This integrated suite of services comes in four flavors: Business, Enterprise, Enterprise Backup, and Compliance and Awareness. All components are managed from an easy-to-use control panel interface which increases efficiency for administrators and security analysts. Licensing is simple, based on a per-user, per-month consumption model, based on the flavor that you select for your organization.
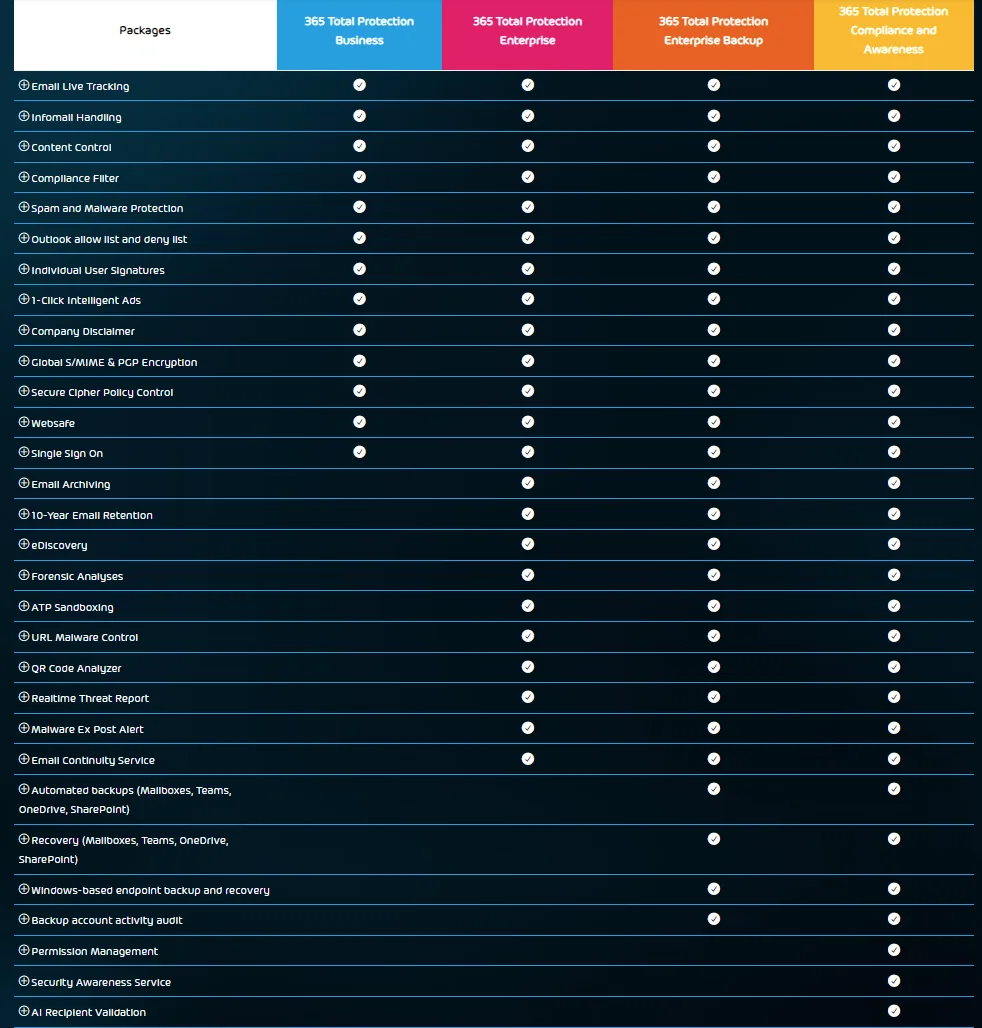
It starts with email hygiene, the biggest vector for attackers to gain a foothold in your organization is still through phishing / spear phishing emails. All versions of Total Protection provide easy to use spam and malware protection for email, the ability to block newsletters, control unwanted content, individual email signatures based on data from Active Directory which can optionally include ads for your organization’s services, disclaimers, S/MIME and PGP encryption plus the ability to send encrypted emails to any recipient through a websafe solution and of course they all provide single-sign-on with the user’s Entra ID accounts.
As discussed above though, you need more than just email hygiene to protect your business, so the Enterprise version of Total Protection adds email archiving to comply with many data regulation frameworks around the world. This feature also helps when you’re performing incident response, and you need to go through older emails to find particular data. Emails are kept automatically, for up to 10 years, whilst allowing full control over exemptions to the retention rules. eDiscovery lets you search through all emails very quickly, handy for legal situations where you must produce all emails between specific people.
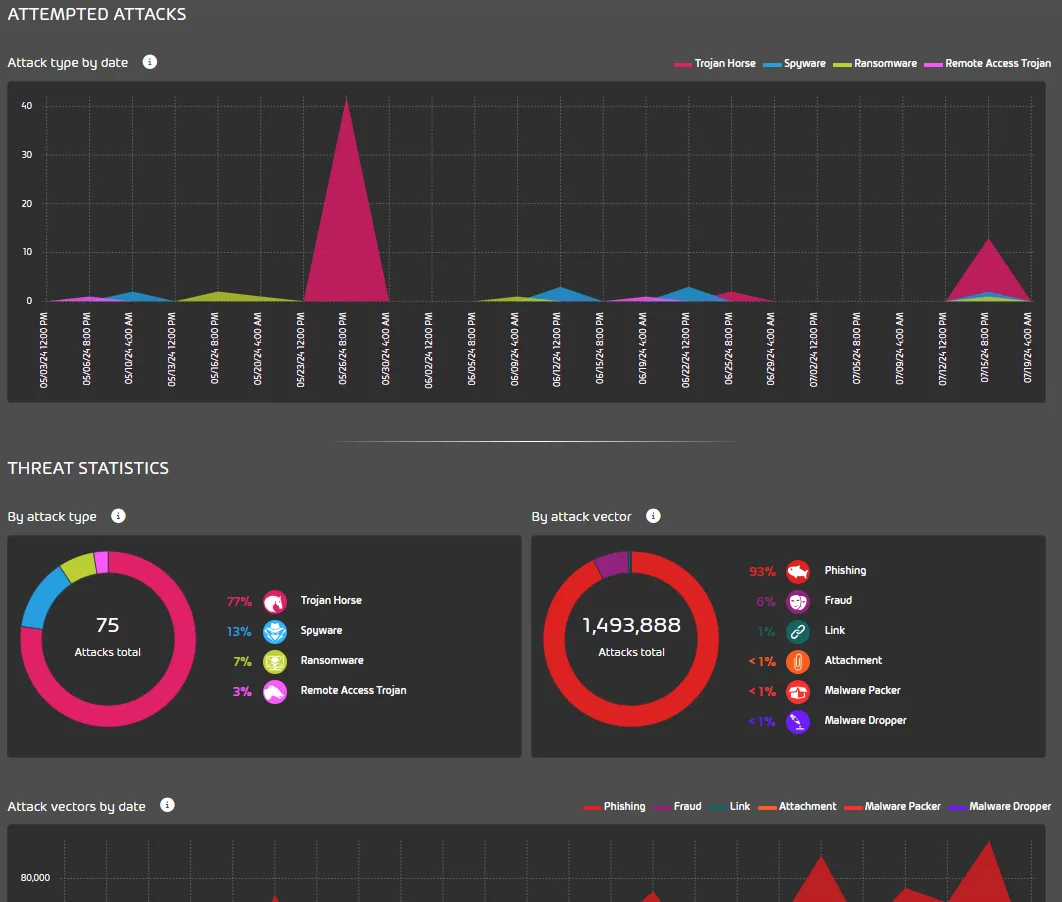
Forensic analysis uses Machine Learning (ML) and AI to spot malicious intent in emails, as well as identity spoofing, fraud and if an attack is targeted to specific accounts in your business. ATP (Advanced Threat Protection) Sandboxing is the solution for spotting malicious email attachments. Any competent email hygiene solution will scan email attachments with several anti-malware engines, but this only catches already known malware, whereas ATP Sandboxing will open the attachment in an isolated environment and inspect it for malicious behavior, thus catching new variants of malware and quarantining it. Oftentimes phishing emails don’t come with malware attachments, rather they attempt fly under the radar with a link to a malicious site or file. Secure links rewrites all links to go through Hornetsecurity’s secure web gateway, where every click is scanned and only when the target site or file is deemed safe is access granted.
The last year or two has seen a huge increase in attackers hiding their malicious URLs in QR codes, tricking users into scanning these using their phone which often has less protection than a corporate managed PC. The Enterprise version was very early in the market to scan and identify malicious QR codes in email. This version also brings it all together in the Realtime Threat Report dashboard that shows you all the threats in your email feeds. For the occasional time where a malicious email sneaks through initially, and is later identified as bad, the Malware Ex-Post-Alerts allows analysts to isolate the threat before it can spread further. For times when Microsoft has an outage affecting email, Email Continuity Service can be activated and allows you to continue sending and receiving email.
As you can see, the Enterprise version offers comprehensive email security, archiving and more, but there are two more areas that must be included to have a single integrated solution: backup and training end users.
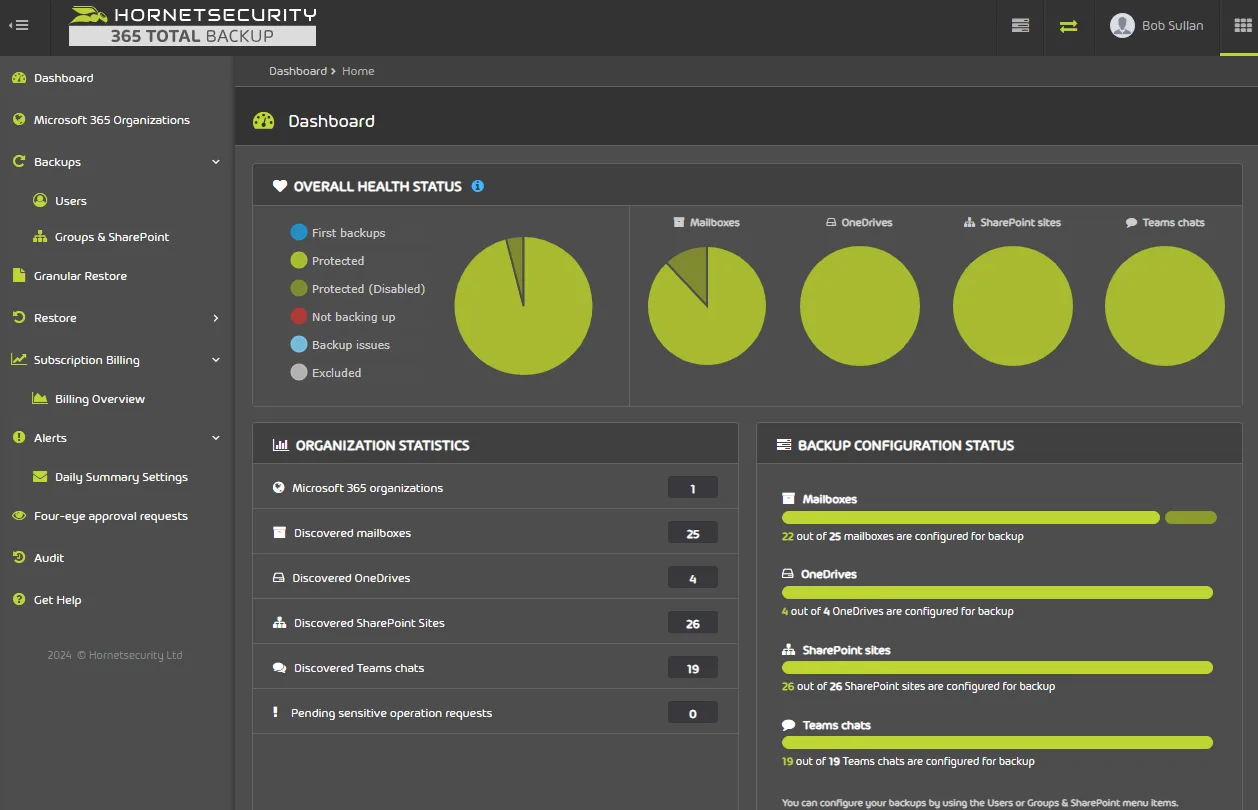
Enterprise Backup does everything already mentioned but adds automated backup and recovery of Microsoft 365 data (Exchange Online Mailboxes, OneDrive for Business, SharePoint sites and Teams content). Also, backup your Windows based endpoints without requiring a VPN connection, all backup / restore operations are kept in the activity audit log.
For a true “all in one” solution for Microsoft 365 security, Compliance and Awareness adds the unique Permission Manager solution to apply sharing policies across all SharePoint and OneDrive for Business sites, spot oversharing of data, see exactly which documents a user has access to in an entire enterprise estate, and also helps with fixing permissions issues at scale. This is particularly useful if your organization is looking to deploy Microsoft 365 Copilot, which relies on a well governed data estate to avoid accidental data leakage. It also uses AI Recipient Validation to check every sent email in real time against previous communications and warns against missing or unintended recipients, and if the email contains PII.
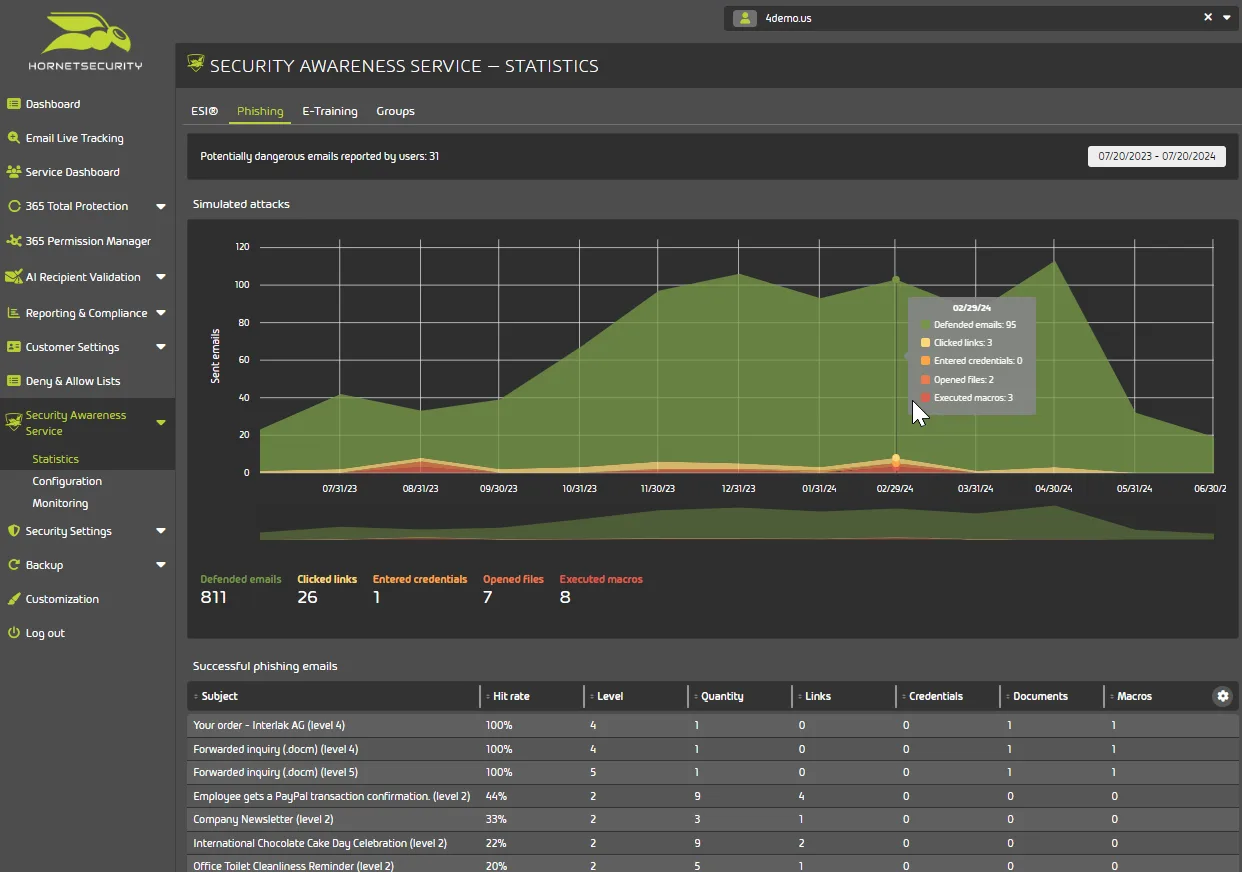
Finally, our best-in-class Security Awareness Service offers low administrative overhead phishing email simulations, and engaging, short video training for staff that fail the test, increasing your staff’s overall cyber security resiliency.
Case Study
It’s very efficient for us, you know, having to have a single product which delivers the entire Microsoft 365 security. That for us was one of the key reasons why we’ve adopted 365 Total Protection and changed the 2 or 3 products we were previously using.
To properly protect your Microsoft 365 environment, use Hornetsecurity one-of-a-kind services:
- 365 Total Protection
- 365 Total Backup
- 365 Permission Manager
- 365 Total Protection Compliance & Awareness
- 365 Total Protection Enterprise Backup
To keep up with the latest Microsoft 365 articles and practices, visit our Hornetsecurity blog now.
Conclusion
There are definite benefits for businesses that use a single vendor approach for their Microsoft 365 security posture, which include cost savings, simplified licensing, enhanced security and a more efficient security team. It also future proofs your organization against cyber threats.
FAQ
A single vendor approach simplifies management, reduces costs, and enhances security by offering integrated solutions.
365 Total Protection provides comprehensive email security, backup, compliance management, and security awareness training.
It offers integrated tools that prevent, detect, and respond to threats across all M365 services, reducing vulnerabilities and response time.

