

There’s a Way to Reduce Work for SOC Teams Whilst Improving Your Company’s Security Posture
Your Security Operations Center (SOC) is a vital tool, front lining your strategy for how to defend your organization’s digital assets through detecting, investigating and responding to threats almost literally every moment of every day.
Tasked with proactive monitoring and acting as the central hub for an organization’s cybersecurity operations, they provide critical functions including:
- Incident Response
- Threat intelligence and analysis
- Vulnerability management
The balance of power between Security Operations Centers (SOCs) and threat actors is constantly shifting, often leaving security teams stuck in a relentless game of “whack-a-mole.” For those unfamiliar, “whack-a-mole” is a game where players use a mallet to hit moles that pop up randomly and rapidly from holes.
As the game progresses, the moles appear faster, making it increasingly difficult to keep up. Similarly, in the SOC environment, the pace and volume of cyber threats are accelerating.
This surge in threats – both in frequency and complexity can overwhelm security teams, as the number of incidents continues to grow exponentially with no signs of slowing down.
Other Key factors faced by SOC teams affecting their ability to operate effectively:
- Burnout: The 2023 “Voice of the SOC” report from Tines found that already back then nearly two-thirds (63%) of SOC professionals reported experiencing burnout from the increasing workloads.
- MTTR (Mean Time To Respond): Meanwhile the ReliaQuest Annual Cyber-Threat report found that the average time to respond to a security incident using traditional methods is a staggering 2.3 days!
- Alert fatigue: Of the three most reported burdens draining valuable time for SOC Teams in the Global State of Security Report by Cisco, 59% said that it was down to having to deal with too many alerts.
Security Operations Center (SOC) teams are under more pressure than ever – managing constant alerts, investigating threats, and responding to incidents at a relentless pace. But there’s a better way.
This blog will examine the challenges SOC teams face in today’s cyber threat landscape, including alert fatigue and resource limitations.
It will show how businesses can reduce the burden on SOCs through smarter security automation and unified platforms like Hornetsecurity’s 365 Total Protection to streamline workflows, improve detection, and enhance the company’s overall security posture.
It’s crucial that organizations continuously monitor their security posture and develop a regular cadence of evaluating metrics to measure how effective their controls are, ensuring they are suitably resilient and deliver business continuity.
A failure to be vigilant and maintain a modern and fit-for-purpose security infrastructure can result in being a victim to a breach, as the NHS in the UK found out in 2024.
Why Traditional SOC Workflows Are Failing Modern Businesses
It’s time for a transformational shift in the approach and methods for SOCs to continue to be effective and protect organizations from threats. The traditional model, relying on a patchwork of disparate tools, each with their own data siloed data sources, has outlived its usefulness.
Let’s talk about the bottlenecks reported and experienced by SOC staff and why this is happening more and more.
Too many tools
In researching this blog, a recurring theme keeps emerging when it comes to tooling: SOC teams are overwhelmed. The 2023 “Voice of the Tines” reported that 12% of respondents are using between 11-24 different tools for their security-related work! It won’t come as a surprise that the efficiency gains invariably have an inverse relationship.
SOC teams grapple with having to use additional tools to do their job, creating frustrations and bottlenecks while trying to perform their core duties.
The annual Splunk State of Security reports from 2021 through to 2025 paint a grim picture demonstrating the increasing struggles for SOC teams with these extra tools, combined with too many alerts.
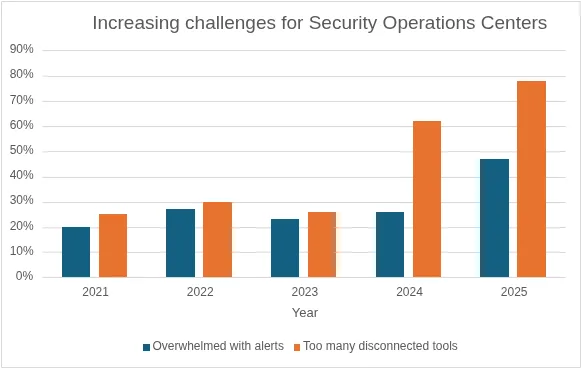
Excessive alerting
It won’t come as a surprise the number of alerts flooding SOC staff, based on which report you read, anywhere from 10,000 – 20,000 per week, the triaging and further investigations across in each resulting in bottlenecks.
By design, some tools are narrowly focused on what they deliver, leaving SOC staff finding themselves spending additional time due to the lack of context and having to correlate across multiple data sources.
Insights & Reporting
A less “exciting”, yet critical responsibility working in a SOC is reporting. That old saying, ‘you can’t manage what you can’t measure’. The vast telemetry collected is crucial for reporting on security incidents to determine the root cause and reconstructing the chain of events, particularly when writing up a Post Incident Report (PIR) for example.
Collecting and collating from multiple tools requires extra time most teams simply don’t have.
User account management
Granting access based on a verified identity rather than merely passing through a secure network entry is increasingly becoming a standard practice.
With the spotlight shining brightly on identity and access management (IDAM), increasing the number of user accounts not only adds to administrative burden and expands your attack surface, but it’s taking you in the entirely wrong direction.
The Consequences of Alert Fatigue
Every security tool needs fine tuning to ensure legitimate threats are detected, carefully balanced with generating minimal false positives (alerts that at first appear legitimate but on further inspection are found that not).
Invariably, false positives do slip through creating distractions for SOC teams and taking important time and focus away from prioritizing real threats. With all the multiple tools used by SOCs, the high volume of false positives can become unmanageable leading to:
- Missed threats
- Analyst burnout
- High turnover rates
- Reduced security effectiveness
You don’t need to look hard to see the real-world consequences of missed threats. Remember the 2013 Target breach? Almost 40 million credit card numbers stolen and incalculable reputational damage to Target.
Later reports found that a contributing factor was that analysts had become desensitized to alerts, frequently dismissing legitimate ones amongst the thousands received daily. Caught amongst these were the alerts from their monitoring system. Oops.
Four years later in the 2017 Equifax breach, it was found that their security team missed multiple alerts (including one from the Department of Homeland Security) to patch the Apache Struts vulnerability that was ultimately exploited.
Smarter Security Operations Through Automation and Integration
I think it’s safe to say that most people who choose to work in a SOC are not attracted to the idea of going through the same set of high-frequency tasks and low-complexity tasks. They are there for the action, catching bad people doing bad stuff!
The reality is that these more mundane activities are often part-and-parcel of this job. The good news is that it can be reduced by increasing automation, integration processes, and technology into SOC operations.
Some of the key benefits of security automation:
- Speed. The scale and pace at which automation can identify, analyze, validate threats.
- Consistency. Using prescribed and uniform methods to minimizes the chances of human error.
- Scalability. SOCs can take on larger volumes of threats without increasing the resourcing.
Integration between the various tools and platforms with centralized management frees up analysts to spend more time focusing on complex threats, for example saving them logging into all those extra consoles!
A unified view makes it easier to identify patterns and trends and respond quicker to threats, especially when handling vast amounts of data. Places like National Public Data (NPD) used for online backs and fraud prevention is one such place who suffered from a data breach of almost 3 billion records!
Working in synergy, automation and integration provides real-time correlation and threat prioritization to improve SOC performance and increase its effectiveness.
How 365 Total Protection Lightens the Load for SOC Teams
- Hornetsecurity’s 365 Total Protection is designed to address these exact challenges, offering a platform that streamlines SOC workflows and enhances security for Microsoft 365 environments. Its layered protection and incident response readiness capabilities are aligned with NIST and other security frameworks, providing a protective layer to defend networks in the modern threat landscape.
- It offers threat protection for email, Microsoft Teams, SharePoint, and OneDrive, with automation capabilities and integration to reduce SOC workload while improving threat prevention and visibility.
- 365 Total Protection uses behavior-based analysis to learn typical communication patterns, user behaviors and business workflows and flags anomalies and Natural Language Processing (NLP) when analyzing emails for signs of social engineering.
- It also comes with preconfigured security policies based on industry best practices and Hornetsecurity’s “secret sauce”, automatically applied upon deployment providing immediate protection and preventing misconfigurations.
- It is hugely valuable and cost-efficient for small organizations or without a dedicated security team.
- Admins get real-time visibility for common threats like phishing, malware and spam as well as more high-impact advanced threats such impersonation attacks. The insights and detailed reporting enable faster responses and improve decision-making.
Let’s go into a bit more detail and see how it replaces complexity with simplicity, and chaos with clarity.
Automated Threat Prevention
At the heart of 365 Total Protection, well perhaps more accurately the brain, is AI Cyber Assistant from Hornetsecurity. An automated security power-up that empowers end users and admins in their day-to-day operations, providing secure communication and a lightened workload.
Its seamless integration into 365 Total Protection reduces the need for manual intervention through key features like Automated email filtering, sandboxing, and AI Recipient Validation.
Working in concert, the Automated email filtering and sandboxing detect and block common social engineering threats such ransomware, phishing and BEC (Business Email Compromise), while the AI Recipient Validation proactively identifies misdirected or malicious emails before they even reach a user’s Inbox.
Simplified Management Across Microsoft 365
SOC teams will be glad to know that the unified console in 365 Total Protection streamlines workflows through an intuitive design for managing their security services and the access controls across the estate.
Underpinning this workflow is 365 Permission Manager, a convenient, user-friendly and time-saving solution you can bolt on, providing admins with a simplified and comprehensive view of permissions across your Microsoft 365 estate.
Bringing us to the subject of compliance, something Security Teams working in the Healthcare industry and HIPPA will be acutely familiar with in their day-to-day management and practices to maintain compliance.
With the spotlight on compliance for organizations only growing larger, 365 Permission Manager takes away some of these headaches through features like comprehensive reporting and an audit function to detect and take action on policy violations.
Reduced False Positives, Faster Resolution
The advanced threat intelligence and machine learning increases the speed at which emails are analyzed for sophisticated social engineering attempts to accurately distinguish between legitimate and malicious emails.
The spam and malware protection has proven to generate less than 0.00015 false positives: “out of one million emails scanned a maximum of four are falsely classified as spam and quarantined.
All of this results in reducing the likelihood of false positives cluttering up dashboard and cutting down on false alarms.
Is your SOC team drowning in alerts, struggling with manual processes, and still missing threats?
It’s time for a smarter approach. Hornetsecurity’s 365 Total Protection helps you:
- Automate threat detection and response
- Eliminate alert fatigue with AI-powered precision
- Manage Microsoft 365 security from a single console
- Improve your organization’s overall security posture
Less noise. More impact. Book a demo to learn more – let’s help your SOC thrive.
Conclusion – Empower Your SOC and Secure Your Business
Your SOC is your frontline of defense, your staff putting themselves onto the battlefield, engaging on multiple fronts with threat actors from all over the world, preventing, detecting, analyzing, and responding to cybersecurity incidents.
They are the backbone of your cybersecurity strategy, and more hands on deck only goes so far. What is needed is automation of routine tasks, more visibility, and integrated tools that deliver real-time actionable insights reduces noise and increases focus.
It’s time to turn up the dial for SOC teams and empower them as they evolve from reactive defense capability to proactive protection. By doing all this, it strengthens your overall security posture and makes an effective use of people, processes, and technology to continuously monitor and improve an organization’s security posture.
FAQ
SOC teams struggle with alert fatigue, burnout, and long response times. This is due to overwhelming volumes of alerts and multiple disparate tools hindering their effectiveness.
Automation streamlines workflows, reduces manual tasks, and enhances threat detection. It enables SOC teams to focus on complex threats rather than routine activities, thereby improving overall security performance.
This unified platform enhances Microsoft 365 security by automating threat detection and managing alerts. As a result, it aims to reduce fatigue, enhance response times, and strengthen the organization’s security posture.

