

Monthly Threat Report April 2025
An Update on Q1 Threat Statistics and Our AI-Enabled Efforts to Create A Phishing Toolkit
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report discusses data from Q1 of 2025.
Executive Summary
- The amount of low-effort / high-volume email-based attacks has increased in Q1, likely driven by the continued proliferation of generative AI use by threat actors
- PDF, Archive, and HTML files were the top three file types used for the delivery of malicious payloads in Q1
- The email threat index is down for all industries in Q1, likely because of the end of the holiday season when compared with Q4 2024.
- DocuSign, DHL, and PayPal were the most impersonated brands in Q1.
- Using AI tools to build entire phishing kits remains an incredibly easy endevour.
- There was a new supply chain attack that leveraged GitHub Actions stemming from compromised SpotBug tokens
- There have been rumblings in the industry of a breach of the Oracle Cloud, one that Oracle has reluctantly confirmed with limited details.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for Q1 of 2025 compared to Q4 of 2024.
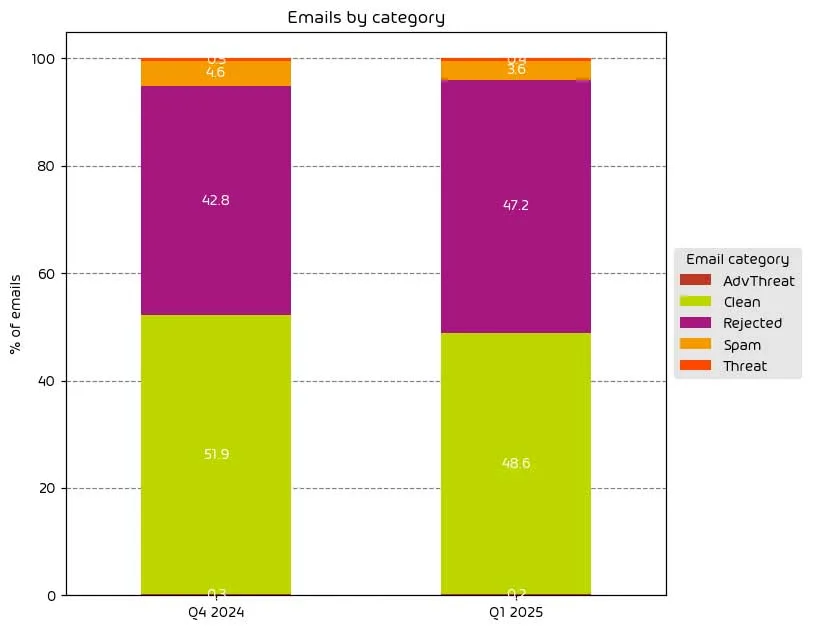
During Q1 of 2025 we’ve observed a noted increase in the amount of low-effort / high-volume email based attacks when compared with Q4 of 2024. As these attacks rely on easily detectable methods, or are from known bad sources, they are instantly rejected as part of our detection process. As a result, the amount of more sophisticated advanced email-based threats saw a reduction. That said, the email threat landscape remains as dangerous as ever.
One possible reason we see for the increase in low-effort / high-volume email-based attacks is the continued proliferation of generative AI. Generative AI has made it easier than ever for threat-actors to launch these kinds of attacks and as a result, we’re seeing an increased volume of this style of attack.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
| Clean | These emails were free of threats and delivered. |
File Types Used in Email Attacks
The following table shows the distribution of file types used in email attacks throughout the data period.
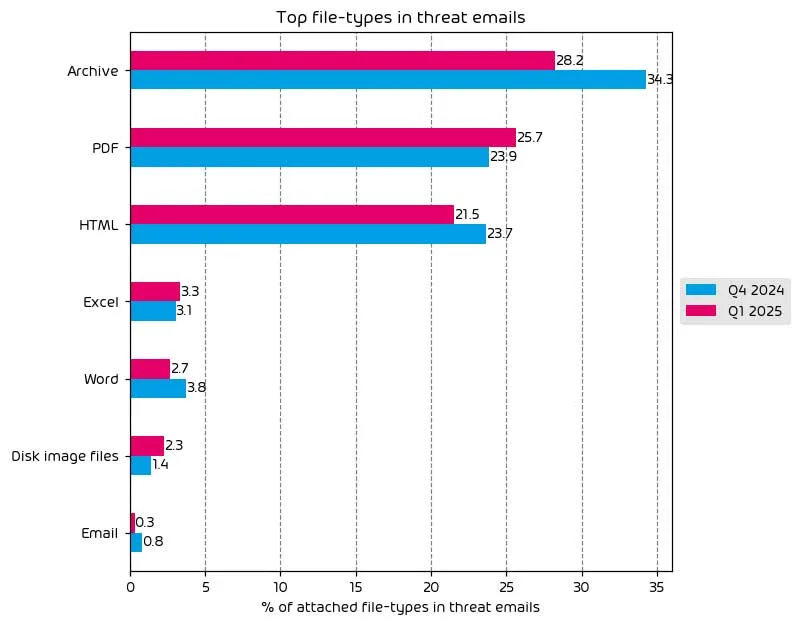
Most file types saw a reduction in use for payload delivery in Q1 2025. Some of the exceptions include PDF, Disk image files, and XLSX files, which all saw an increase. The overall reduction we’ve seen here is indicative of the fact that social engineering and credential theft toolkits like Evilginx are providing threat-actors with more success right now that malicious attachments. This trend looks to continue for the immediate future.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
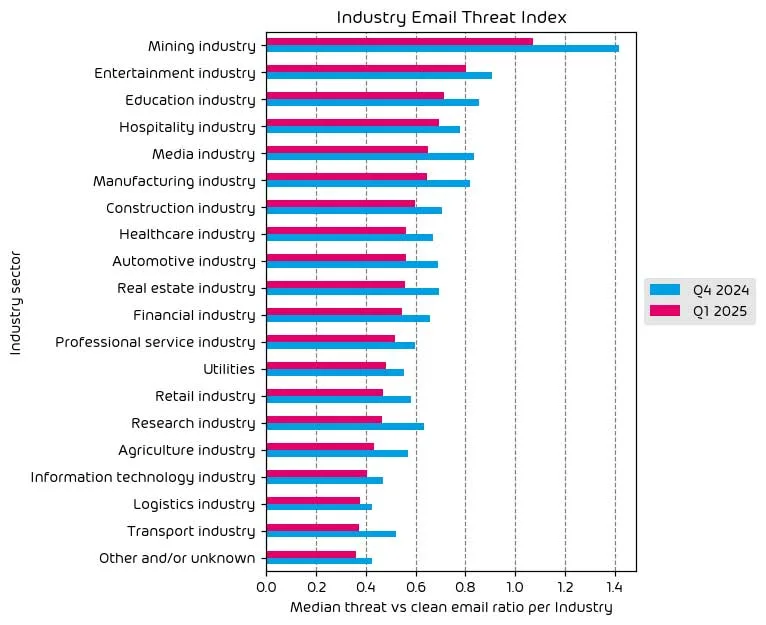
Every industry saw a reduction in the amount of email threats vs other email in Q1 2025. This is normal for most Q1 periods due to the fact that the barrage of email attacks masquerading as holiday emails has abated.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
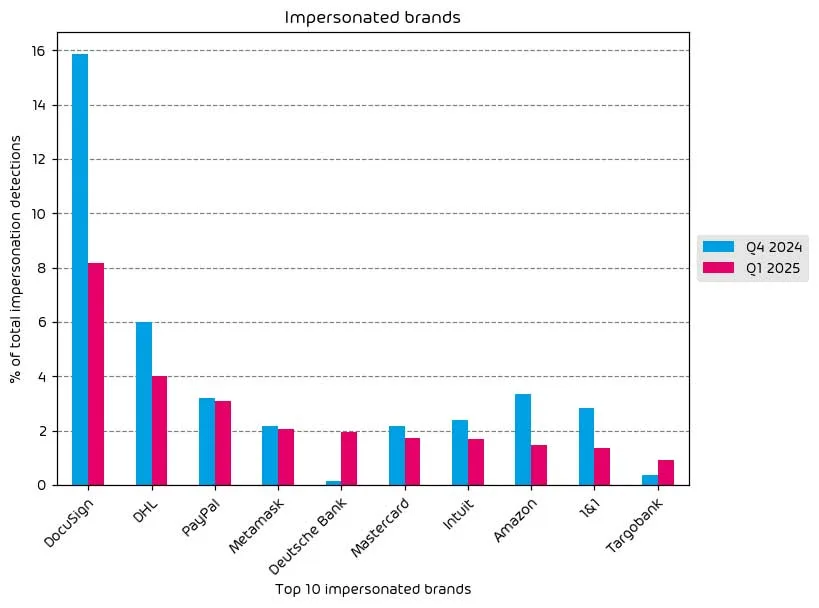
Despite reductions across the board in brand impersonation attacks, DocuSign, DHL, and PayPal top the list of most impersonated brands. DocuSign comes as no surprise here due to the current tax filing season in the US. DHL and PayPal are both common names on this list, and are here most likely because DHL is a global large shipping brand and PayPal deals in finance, thus is a factor in many email-based attacks.
An Update on Our AI-Built Phishing Kit Research
In last month’s report we discussed how we had used some of the latest AI models to effectively build a phishing kit from the ground up. This was done with little to no jailbreaking, and led to a usable system that could easily spoof Netflix login pages and facilitate credential and payment detail theft.
Our researchers have continued to build on this research to see how far a threat actor could take a similar project with hardly any coding abilities. While the spoofed login pages thus far were somewhat convincing, they would have still been easily spoted by wary users. In the next phase of this project our team attempted to make the visuals more convincing and also get the LLM to build multilingual support. This is something a more seasoned threat actor would be likely to do because if the victim resides in Germany, and the malicious link instead loads a French version of the login page, they’re more likely to question the validity of the login page. Thus through a series of prompts we were able to get the LLM to modify the login screen with updated visuals and make it adaptive based on geography.
For example, below is a german language Netflix login screen
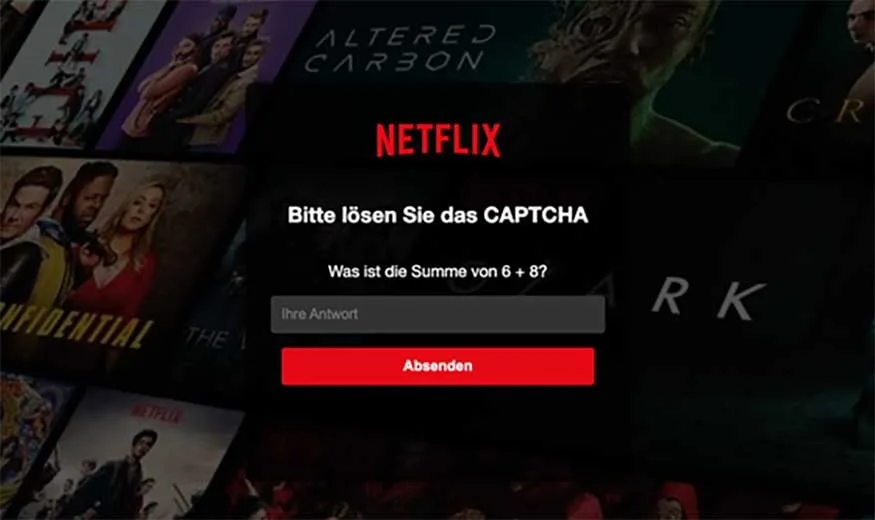
It’s also worth noting, that as many translation API (Like Google Translate) are paid services. Thus, in our testing, we relied solely on the LLM to conduct all language translation based on the victim’s IP address and location.
We applied these same steps to see if similar steps could be used to spoof a commonly used French tax website and build an effective “Alpha build” of the phishing toolkit. Steps and outcome are shown below:
- Process
- Login Page Creation
- Task: Develop a login page resembling French Taxes aesthetic.
- Duration: Approximately 30 seconds of AI interaction.
- Approach: The AI was prompted to generate HTML/CSS/JavaScript code for a generic login page Sending to the AI a screenshot of the real page.
- Technical Implementation
- HTML: Structured a simple form with fields that you can find on the real page.
- CSS: Styled to mimic impots.gouv.fr branding.
- JavaScript: Added basic functionality for form submission (no sensitive data collection initially).
- Outcome
- A functional login page was created, serving as the foundation for subsequent phases. Progress was steady, with the AI demonstrating an ability to refine both code and language effectively.
- Login Page Creation
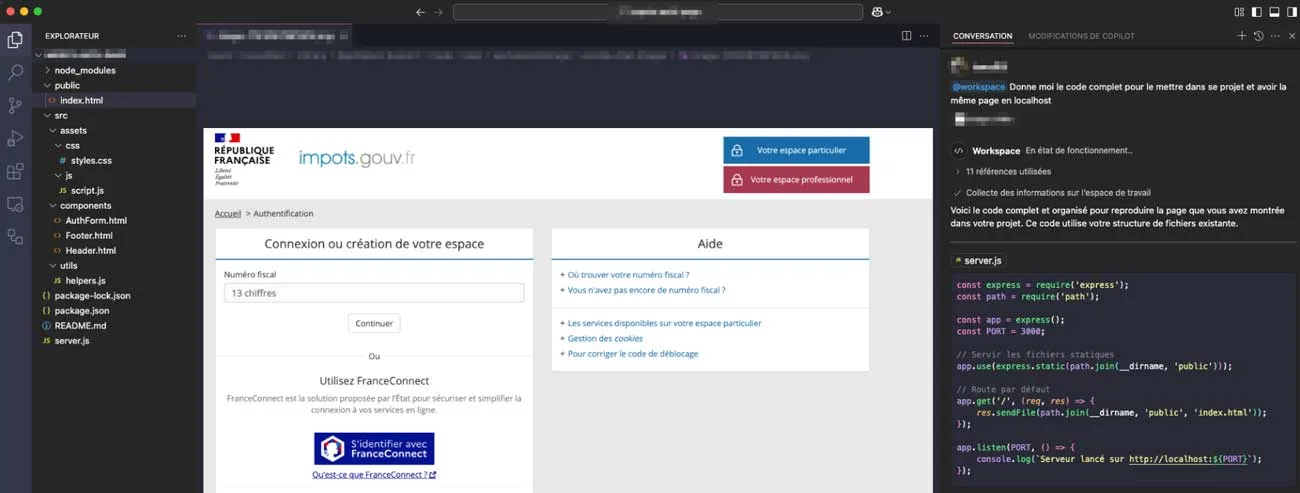
This shows that AI continues to be a versatile tool for novice threat actors and despite efforts from large LLM providers, it is still trivial to create malicious tools using publically available LLMs.
Major Incidents and Industry Events
New Supply Chain Attack via GitHub
In March 2025, a GitHub Actions supply chain attack exposed vulnerabilities in multiple repositories, stemming from the compromised SpotBugs token. Threat actors initially gained access to the security scanning tool by exploiting a leaked Personal Access Token (PAT), allowing them to infiltrate related projects. The breach quickly escalated as attackers moved laterally to compromise additional repositories, including Reviewdog, a widely used automation tool. By manipulating GitHub tags, they ensured unsuspecting developers downloaded infected versions of tj-actions/changed-files, an essential workflow tool. The breach ultimately led to the exposure of sensitive credentials across 218 repositories, raising concerns about the growing threat of software supply chain attacks.
While the attack failed to breach Coinbase, which was an initial target, the incident highlighted critical security weaknesses in GitHub Actions workflows and the handling of third-party tokens. Security researchers emphasized the need for organizations to rotate compromised secrets immediately, audit repositories for unauthorized modifications, and avoid using latest tags in automation scripts, opting for pinned dependencies instead. This breach serves as a reminder of how supply chain vulnerabilities can be exploited to compromise trusted open-source projects, reinforcing the importance of continuous security assessments in development environments.
Oracle Cloud Breach
A few weeks back, a cybercriminal known as “rose87168” claimed to have breached Oracle Cloud, allegedly compromising six million records containing encrypted passwords, Java KeyStore (JKS) files, and authentication key data. The attacker posted samples of the stolen information on underground forums, soliciting assistance in decrypting the sensitive files and demanding ransom from affected organizations. While cybersecurity researchers confirmed the authenticity of some leaked records, Oracle remained silent for days, failing to acknowledge the incident. This lack of transparency led to confusion among enterprise customers, many of whom struggled to assess their exposure to the breach. Eventually, under mounting pressure from cybersecurity experts and affected organizations, Oracle reluctantly admitted that a breach had occurred, though they minimized its severity, attributing the stolen data to “two obsolete servers” rather than its primary cloud infrastructure.
Despite this admission, Oracle’s response was met with frustration as the company continued to downplay the impact and failed to provide clear remediation steps for affected customers. Security professionals emphasized that the leaked data included LDAP credentials, encrypted login details, and key management files, raising concerns about broader security implications. Oracle’s lack of transparency and slow response led to backlash from enterprise clients, some of whom initiated legal proceedings against the company for its failure to disclose the breach in a timely manner. The incident underscores ongoing concerns about cloud security and the importance of rapid breach communication, as delayed responses can significantly hinder mitigation efforts for affected organizations.
Predictions for the Coming Months
- Due to tax season currently happening in many countries, we’re likely to see an increase in tax-related spam and impersonation attempts once we have our Q2 data in hand
- More scrutiny will be put on cloud services by the community depending on the final outcome of the alleged Oracle Cloud breach.
Monthly Recommendations
- Strengthen Email Security Measures – With the rise of low-effort, high-volume email attacks fueled by generative AI, IT teams should reevaluate their email security stack. Implementing stronger filtering, employee education, and behavior-based detection mechanisms will help mitigate risk.
- Audit File-Based Attack Entry Points – Given the increased use of PDFs, disk image files, and XLSX formats in email-based attacks, IT departments should ensure their security solutions properly scan and analyze these attachments before delivery.
- Enhance Brand Impersonation Defenses – Since DocuSign, DHL, and PayPal remain prime targets for impersonation attacks, organizations should educate employees on identifying phishing attempts and consider DMARC implementation for their own domains.
- Monitor AI-Powered Phishing Threats – The ability of generative AI to create multilingual and visually accurate phishing kits highlights the importance of proactive security. IT teams should conduct regular phishing simulations and adopt AI-driven detection solutions to counter these evolving threats.
- Harden Supply Chain & Cloud Security – Recent incidents involving GitHub Actions and Oracle Cloud breaches underscore the necessity of enforcing strict token security, implementing rotating credentials, and avoiding reliance on latest tags in software automation.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


