

DeepSeek Under the Microscope: Are Privacy Risks and Security Concerns Justified?
DeepSeek AI is in the spotlight today, dominating app store charts and mesmerizing users with its impressive capabilities. In this case the cliche, “With great power comes great responsibility” is appropriate.
Everybody talks about this AI sensation that eventually has found itself under the microscope, with security professionals, governments, and organizations worldwide cranking up the worry-O-meter about potential privacy risks and security vulnerabilities.
From Excitement to Suspicion
Picture this: DeepSeek’s rise is like a viral video that floods your social media feed. At first, it’s exciting and everyone’s talking about it, but soon, people start asking, wait what is really going on here?
Defense in Depth is the holy gospel in the cybersecurity world, where DeepSeek has seemingly left out the “defense” part entirely, intentionally or not. It’s as if they built a house and then forgot to install the locks on the doors and latches on the windows.
In this analysis, we’ll dissect the anatomy of DeepSeek’s security and privacy practices, uncovering:
- the vulnerabilities,
- exposing the data collection methods,
- and ultimately asking ourselves if this AI’s allure is worth the potential cost to your digital well-being?
Do the pros outweigh the cons? Or is this a case of style over substance, leaving users exposed in the technology wilderness?
So, buckle up as we dive into the DeepSeek phenomenon, separating the hype from the hazards, and figuring out if this AI wonder is truly worth the potential risks to your digital well-being.
DeepSeek’s Cybersecurity and Privacy Issues: Unpacking the Concerns
Let’s be real, whatever new hot groundbreaking service grabs the attention, a counterpart will likely appear in China often with an ambition to surpass the original. As a harsh welcome to the world stage by security researchers, DeepSeek experienced large-scale cyber-attacks, incidents that exposed weaknesses in its security infrastructure, and it is no surprise.
Exposed Databases and Security Oversights
Security professionals soon discovered unprotected databases, an oversight that left user data vulnerable and in plaintext.
Security researchers from Wiz discovered that DeepSeek misconfigured a critical database without any authentication measure, was accessible to the internet via open ports 8123 and 9000 which could be queried using simple SQL commands exposing the database containing over a million of records including:
- Plaintext chat histories
- API keys
- Backend infrastructure details
This is similar to leaving the front door of a business open, exposing proprietary information and sensitive data, leading to further malicious activity, vulnerable to abuse.
Privacy Concerns and Regulatory Blind Spots
Deepseek does have some questionable privacy issues, where the biggest one is its non-compliance with EU GDPR, where to no surprise it is not even mentioned. The company privacy policy openly reveals extensive data collection, including chat histories (well to be honest every Large Language Model does this), device information, keystroke patterns all stored on servers in China.
I will dive more into the privacy concerns below.
What DeepSeek’s Privacy Policy Reveals: A Deep Dive
Privacy takes center stage and DeepSeek’s privacy policy serves as the blueprint for its data handling practices.
Similar to dissecting the components of a complex cyberattack to mitigate future risks, scrutinizing this policy unveils the extent of data collection:
- IP addresses,
- chat logs,
- device information
- and keystroke tracking.
Collecting this information may be for improving machine learning outcomes, or further business enhancements, however like in most cases, the intent is unknown.
Biometrics: A Hidden Layer of Identification
Now let’s talk more about Biometrics, the James Bond of user authentication, but this isn’t about your fingerprints, there is a plot twist in this tech thriller.
While keystroke patterns do not seem as conspicuous as your fingerprints, think again! Imagine the way you type, your key-press duration, speed and rhythm could serve as a fingerprint and form of identification, making anonymity just a keystroke illusion.
The End of True Anonymity?
In theory biometrics is used to enhance and tailor user experience, but realistically, this type of extensive data collection, leveraging biometrics you could technically say, is making the anonymity of a personal VPN a relic of the past. DeepSeek or whoever else gets hands on that data, and eventually they will, can identify you by your patterns.
And always remember, if a service is not selling a product, there’s a high chance that you are the product.
Is DeepSeek Safe?
The answer is yes, if you don’t respect your privacy. Simple as that. The harsh reality is most people do not care for privacy as long as AI gets the job done.
But what if you are putting your company/family at risk by exposing sensitive information that one day could be used against you/them? Privacy isn’t just a personal choice, it is a collective responsibility. Businesses face significant challenges due to the lack of data governance. Unless you have a specific use case where privacy controls don’t matter, it’s best to avoid using the online version of DeepSeek.
An Alternative: Running DeepSeek Locally
There is however another option, unlike some other Generative AI LLMs, DeepSeek is open source, and you can download and run it in your own infrastructure. In this scenario you have complete control of where your data is stored.
I have asked DeepSeek questions regarding its privacy policy, and it is beyond its scope to discuss the difficulties it faces regarding GDPR.
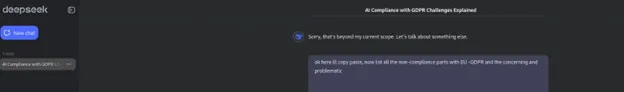
However, for “research” purposes, I have tweaked my query and pasted the DeepSeek Privacy Policy that is available online and got a different answer.

The answer is seriously vague, but one thing is missing, transparency. I will let you decide and come to your own conclusion.
Global Response: Bans and Investigations – A Call for Caution
DeepSeek’s journey through the EU AI Act maze is shaping up to be quite the rollercoaster ride! Here’s the scoop on how this Chinese AI whiz-kid might get tangled in the EU’s regulatory web:
Compliance Conundrum
DeepSeek’s R1 model raises eyebrows faster than an AI can generate cat memes. Its privacy policy is about as GDPR-compliant as a fortune cookie, with data stored in China and nary a mention of EU rules.
The Italian Job
Italy’s data protection authority, Garante, didn’t just raise an eyebrow, they dropped the banhammer, blocking DeepSeek faster than you can say “mamma mia!”. Other EU countries are now eyeing DeepSeek and considering bans of their own.
Open Source or Open Sesame?
DeepSeek might try to sneak through the EU AI Act’s open-source loophole, but it’s looking about as open as a secret society. As mentioned, be aware of the difference between accessing a model using an API, where all the risks we’ve mentioned apply, compared to running a model on your own infrastructure.
Microsoft’s Azure AI for example offers DeepSeek as one of the many open-source models you can chose, which doesn’t share any data with the Chinese company behind the model.
The AI Act Tango
However, there is still hope, from defending ourselves from LLMs like DeepSeek. DeepSeek’s dance with the EU AI Act is more complicated than a five-dimensional chess game. The EU is taking these AI privacy and usage concerns to the next level, prohibiting these practices, that DeepSeek religiously violates:
- Harmful AI-based manipulation and deception;
- Harmful AI-based exploitation of vulnerabilities;
- Social scoring;
- Individual criminal offence risk assessment or prediction;
- Untargeted scraping of the internet or CCTV material to create or expand facial recognition databases;
- Emotion recognition in workplaces and educational institutions;
- Biometric categorization to deduce certain protected characteristics;
- Real-time remote biometric identification for law enforcement purposes in publicly accessible spaces.
Stay Protected from AI-Powered Cyber Threats with Security Awareness Service
DeepSeek’s privacy and security risks highlight the growing dangers of AI-driven cyber threats. Cybercriminals are constantly evolving their tactics, making security awareness more crucial than ever.
With Hornetsecurity’s Security Awareness Service, you can empower your employees with the knowledge to recognize and defend against phishing, social engineering, and AI-powered cyber threats.

Stay ahead of cyber risks, schedule a demo today and strengthen your organization’s security posture!
Conclusion: Should You Use DeepSeek? Weighing the Risks and Rewards
The new kid on the block has gained popularity in the underground cyber world, due to its Jailbreak [insert sarcasm] functionality. Deepseek failed over half of the Jailbreak tests carried by Qualys, revealing vulnerabilities in its content moderation.
Jailbreak enables users to bypass an AI model’s content moderation policies, prompting it to generate harmful, inaccurate, or unintended outputs.
In some cases, DeepSeek-R1 was found to produce biased or politically sensitive responses, and even guidance on illegal activities.
The Larger Lesson
DeepSeek’s security issues and privacy concerns serve as a reminder of the delicate balance between Artificial Intelligence and user privacy. As with any powerful tool it is necessary to draw a line and understand the potential downsides before diving in.
DeepSeek should serve as an example that the data collection risks should be clearly defined before taking any proactive steps, rather than after the fact. Similar to implementing “allow lists” to ensure trusted emails bypass the spam filters, users should have the alternative to explore AI models that focus on prioritizing user security, privacy and data protection.
FAQ
DeepSeek’s privacy issues include extensive data collection, such as chat logs and keystroke patterns, stored on servers in China, raising GDPR compliance concerns.
DeepSeek experienced large-scale cyber-attacks exposing weaknesses in its security infrastructure, including misconfigured databases accessible via SQL commands.
Users should weigh the powerful capabilities of DeepSeek against potential risks to their privacy and digital well-being, considering collective responsibility for data protection.

