

Email Threats in 2024 Are Evolving – How Advanced Threat Protection Keeps Your Business One Step Ahead of Attacks
The most common way that criminals gain access to your business is through malicious emails. This is often a phishing email, asking the recipient to change their corporate password with a link to a site, or to approve a parcel delivery, or in what’s becoming more common, scan a QR code on your phone to access a business application.
These risks are all real, and they are used to compromise businesses every day.
To make sure your business isn’t the next one in the headlines for all the wrong reasons, you need a strong and layered defense, that adapts and evolves with the ever-changing threat landscape.
In this article we’ll explore how Hornetsecurity’s email security services seamlessly integrates with your Microsoft 365 email services and protects you from simple, volume-based threats with smart tech, keeps you safe from advanced attacks such as spear phishing with Advanced Threat Protection (ATP), safeguards your users from malicious QR codes out of the box and if all of those layers fail, trains your users to spot and report malicious content.
We’ll go deep on ATP, without revealing details criminals can use to bypass your defenses.
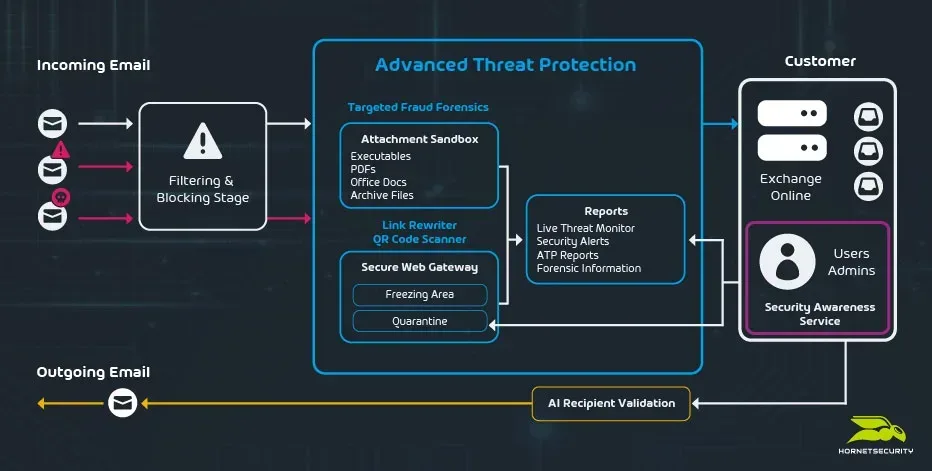
Two Ways to Integrate With Exchange Online
There are two technical approaches to layer email security on top of Exchange Online in Microsoft 365:
- The first involves changing the Mail eXchanger (MX) records for your email domain (“company.com”) in the internet’s Domain Name System (DNS) to point to our service. All incoming mail will pass through our services, providing a clean feed to your user’s inboxes.
- The second method is creating an application in Entra ID (formerly Azure Active Directory, AAD), the identity platform underlying Microsoft 365 and giving it specific permissions to the Graph Application Programming Interface (API) that exposes user mailboxes. This second approach allows additional flexibility, such as the ability to reach into user’s mailboxes after an email has already been delivered and deleting it, if the system has determined that something was missed in the original delivery scan and the email is now identified as malicious.
Hornetsecurity applies both methods, combining the best of both worlds for unsurpassed protection.
Dealing With Low Hanging Fruit
In our 2024 Cyber Security Report we saw that out of the 45 billion emails we scanned in 12 months, 36.4% were categorized as unwanted. That’s over a third of all emails that you want to keep out of your user’s inboxes. Out of that third, 3.6% were flagged as malicious.
Clearly you need a fast system to deal with the vast amount of junk quickly, which we do at the blocking phase, weeding out connections from known bad email servers, and traffic from known bad senders.
We have a 99.9% guaranteed spam detection and 99.99% virus detection, using 18 independent virus and phishing spam filters, and we scan both incoming and outgoing emails for spam, malicious URLs and viruses.
Sometimes an email bounces, meaning it’s sent back as the address is unknown (or accidentally mistyped) which is useful for the sender to know. However, sometimes you get bounced emails because an attacker used your email as the sending address, we filter out these fake ones to protect against backscatter and bounce attacks.
It’s an Arms Race
The above services deal with most of the incoming undesirable and malicious emails. However, attackers spend a lot of time and effort changing their attack methods to bypass email filters. This is where ATP comes in.
One popular option is attaching an encrypted document to an email. Normally anti-malware engines can’t scan these and so might miss a malicious file, ATP uses Malicious Document Decryption to protect against this.
QR codes in emails is an attack type that’s gained momentum in the last few months, partly because QR codes are now such a normal part of life (restaurant menus, paying for car parking etc.), and partly because it moves the attack from the (often) corporate owned and managed PC to a user’s personal phone.
It neatly bypasses all the protections in place on the computer and the URL in the QR code often leads to a familiar looking login page. ATP has had built in QR code scanning for common file types (GIF, JPEG, PNG and BMP) for over a year.
ATP has many layers of protection such as the Sandbox Engine, which will open all attached files, identifying malicious attachments and if they are, the email is quarantined.
The Sandbox Engine looks at if the attached files show signs of detecting that they’re running in a VM or a sandbox, which is a dead giveaway that it’s malicious. It also uses a file system monitor to see if the attachment writes or alter files, a process monitor to see if the file starts a child process (popular in malicious Adobe PDF files).
There’s also a registry monitor to spot unusual values being stored in the registry (often used for persistence when the PC is restarted) and network monitoring to see if the document is trying to communicate with an endpoint on the internet, another unusual behavior for a document.
Memory is inspected from a forensic point of view (again, documents accessing memory in unusual ways is a strong indication that it’s malicious). Tying it all together is a Machine Learning engine that looks at the above signals, and over 500 indicators, and separates malicious files from benign ones with very high accuracy.
Freezing is another approach, if an email is suspicious, but not clearly classified as bad yet, it’s held back for a short time. New data may lead to a positive identification of a virus attachment for example.
All links in emails (URLs) are rewritten with a link to our secure web gateway, and scanned both when the email is received and when the user eventually clicks on it.
To work around this, attackers often include the links in attached files, which can’t be rewritten (it would alter the integrity of the document), but our engine still follows these links to verify if there’s any malicious payload on the target end.
One very important feature of cyber security tools is to let you know when bad things are afoot, and ATP provides real-time alerts when your organization is under a targeted email attack.
A related feature is Ex-Post alerts: if emails that have already been delivered are subsequently identified as malicious your IT team is notified.
As mentioned, these emails can be automatically deleted, but the user may already have clicked a link, or opened an attachment, so your response team might want to investigate these user accounts / devices further.
Human beings are still the weakest link, and our psychology is used against us when attackers employ social engineering tactics.
Our Targeted Fraud Forensics uses automated fraud attempt analysis and intention spoofing recognition to detect and prevent social engineering attacks.
It looks at the language of the email, looking for patterns that indicate malicious intent, espionage attacks, or if the text presents false facts to get the recipient to respond, as well as spotting forged sender identities.
Sending to the Right Recipients?
Another feature that’ll assist your overall email security posture is AI recipient validation, which will warn you if you’re including an unintended recipient, or if you’re missing a recipient that should have been included.
It’ll also warn you if the email contains sensitive information, like Personal Identifiable Information (PII), inappropriate wording or if you’re replying to a large distribution list. This analysis is done locally in the Outlook client, no data is sent to our service.
Of course, there’s a dashboard for administrators to see what warnings the users had, and what their response was, and an admin can also disable particular warning scenarios, exclude users from different warnings, and add external domains to be treated as internal ones.
Improving Your Human Firewalls
No protection system is completely foolproof, there will be times when a malicious email sneaks through your defences, at least temporarily, and this is where training your users is vital.
Many other services for this take a lot of administrator time, planning, scheduling, and following up with the users who fell for the simulated phishing attacks. Hornetsecurity’s Security Awareness Service is different, and is mostly set-and-forget.
Each user is tracked with an Employee Security Index (ESI), users who rarely click on simulated malicious links or attachments aren’t bothered with simulations, whereas repeat offenders receive more simulated attacks, as well as short, relevant video training content.
It also uses gamification to increase engagement amongst your users.
Stay ahead of the evolution of email threats in 2024 with Advanced Threat Protection from Hornetsecurity. Protect your business and your employees against sophisticated attacks.
Don’t wait any longer; protect your email with Hornetsecurity and ensure the resilience of your digital assets.
Conclusion
Email is the most prevalent vector for attackers to compromise your users, and then used to further infiltrate your systems.
A comprehensive email hygiene service must deal with the easy threats, mass mailed spam and phishing, as well as advanced threats such as spear phishing and targeted email lures.
Hornetsecurity’s spam and malware filters, combined with Advanced Threat Protection, is the best defence. Add in the additional services such as AI Recipient Validation, along with Security Awareness Service and you have a winning combination.
FAQ
ATP uses malicious document decryption, a sandbox engine and a machine learning engine to inspect file behavior, registry changes, network communication and memory access, achieving high accuracy in distinguishing malicious files.
Suspicious emails are temporarily held back using a freezing approach. During this time, new data may lead to positive identification, and all links are scanned through Hornetsecurity’s secure web gateway before being delivered to the user.
The Security Awareness Service employs an Employee Security Index (ESI) to track user behavior. It automatically tailors simulated attacks and video training content based on individual responses, utilizing gamification to enhance user engagement with minimal administrative effort.
