

Monthly Threat Report August 2023: WormGPT and an Increase in Email Security Threats
Introduction
The Monthly Threat Report by Hornetsecurity brings you monthly insights into M365 security trends, email-based threats, and commentary on current events in the cybersecurity space. This edition of the Monthly Threat Report focuses on data for the month of July.
Executive Summary
- Our tracked threat categories saw a net increase across the board for the month of July vs. June.
- HTML files were the top file type for email attacks last month. This is largely because there was a significant decrease in malicious PDF usage by Qakbot.
- The entertainment and research verticals were the most targeted businesses in the past month.
- DHL continues to be the most impersonated brand, with impersonation attempts increasing for Sparkasse, LinkedIn, Mastercard, and Netflix.
- New dark-web generative AI tools like WormGPT will likely increase Business Email Compromise attacks over the coming weeks and months.
- There continue to be privacy failures, double-extortion attacks, and other fallout associated with the MOVEit file transfer software vulnerabilities from earlier this summer. If you haven’t patched yet, do so. TODAY.
- A recent breach of Microsoft Cloud services by a Chinese threat actor is leading some experts in the industry to call Microsoft’s response to the breach into question. It is also likely to renew the conversation about cloud providers’ role in Security.
Threat Overview
Unwanted Emails By Category
The following table shows the distribution of unwanted emails per category for July 2023 compared to June 2023.
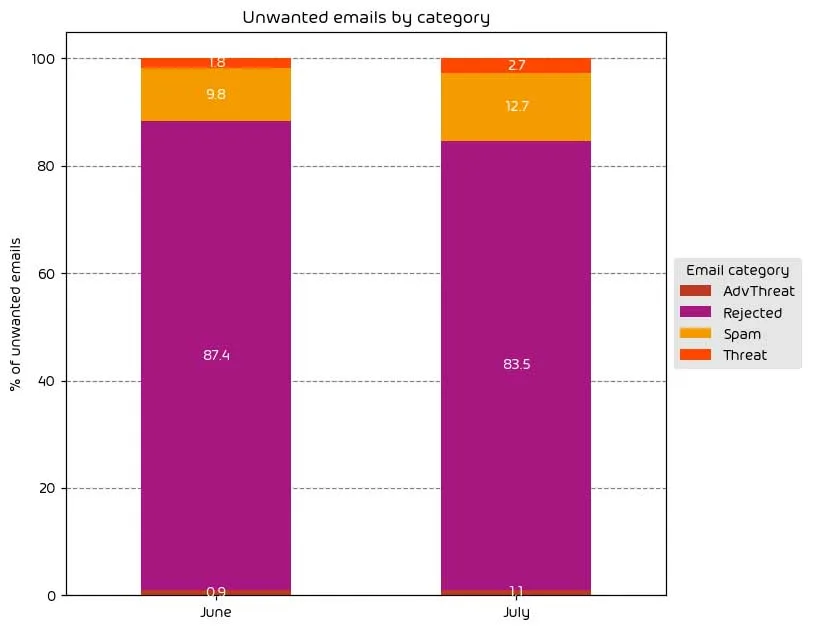
This month saw a slight increase in the number of threatening emails. The amount of mail classified as “Spam” is up 2.9%, while the amount of mail classified as “Threat” and “AdvThreat” increased by 0.9% and 0.2%, respectively. This led to the amount of “Rejected” mail seeing a 3.9% reduction.
NOTE: As a reminder, the “Rejected” category refers to mail that Hornetsecurity services rejected during the SMTP dialog because of external characteristics, such as the sender’s identity or IP address. If a sender is already identified as compromised, the system does not proceed with further analysis. The SMTP server denies the email transfer right at the initial point of connection based on the negative reputation of the IP and the sender’s identity.
Other categories in the image are described in the table below:
| Category | Description |
| Spam | These emails are unwanted and are often promotional or fraudulent. The emails are sent simultaneously to a large number of recipients. |
| Threat | These emails contain harmful content, such as malicious attachments or links, or they are sent to commit crimes like phishing. |
| AdvThreat | Advanced Threat Protection has detected a threat in these emails. The emails are used for illegal purposes and involve sophisticated technical means that can only be fended off using advanced dynamic procedures. |
| Rejected | Our email server rejects these emails directly during the SMTP dialog because of external characteristics, such as the sender’s identity, and the emails are not analyzed further. |
File Types Used in Attacks
The following table shows the distribution of file types used in attacks.
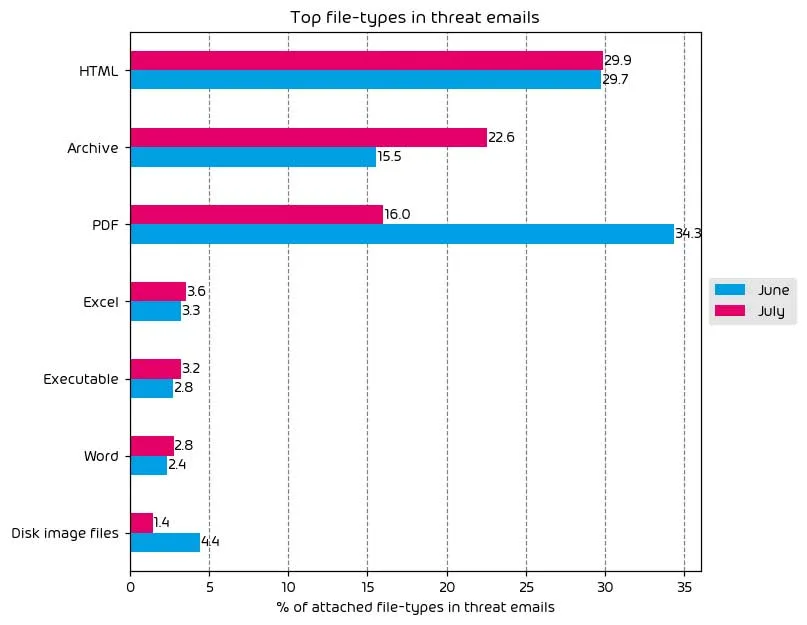
HTML files have taken the top place as the most used file type in email attacks over the month of July. This was primarily because of a reduction in the use of malicious PDF files, which were predominantly used to distribute the Qakbot malware. While the Qakbot malware is still active, during this month, it was not distributed via email-based attacks.
NOTE:If you would like to learn more about Qakbot and botnets, check out the Security Swarm Podcast episode below.
Other notable changes over the last month include a noticeable increase in malicious archive files and slight increases in the use of Excel files, Word docs, and executable files. With this in mind, we continue to attribute the current low usage of Office documents for payload delivery as a direct result of Microsoft’s decision to disable macros in Office applications by default.
Industry Email Threat Index
The following table shows our Industry Email Threat Index calculated based on the number of threat emails compared to each industry’s clean emails (in median). Different organizations receive a different absolute number of emails. Thus, we calculate the percent share of threat emails from each organization’s threat and clean emails to compare organizations. We then calculate the median of these percent values for all organizations within the same industry to form the industry’s final threat score.
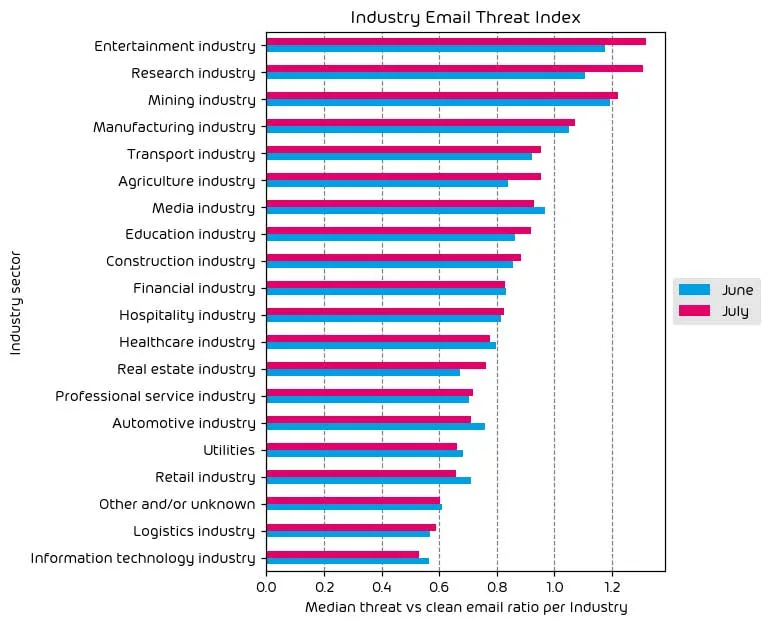
Most industry verticals saw a net increase in their given threat index for the month of July. To put it simply, the data shows that more threats were levied at (most) businesses than the previous month. Attacks always have an ebb and flow, and even though last month saw a universal decrease in the number of threats, the data is swinging back in the other direction for this data period.
Regarding the top targeted industry, the entertainment sector remains near the top, with research firms seeing a significant increase in the number of attacks in the last 30 days as well. Threat actors know that intellectual property is valuable, so it’s common for research firms to be a heavy target for ransomware and IP theft. Nonetheless, the increased amount of attacks was noticeable.
Impersonated Company Brands and Organizations
The following table shows which company brands and organizations our systems detected most in impersonation attacks.
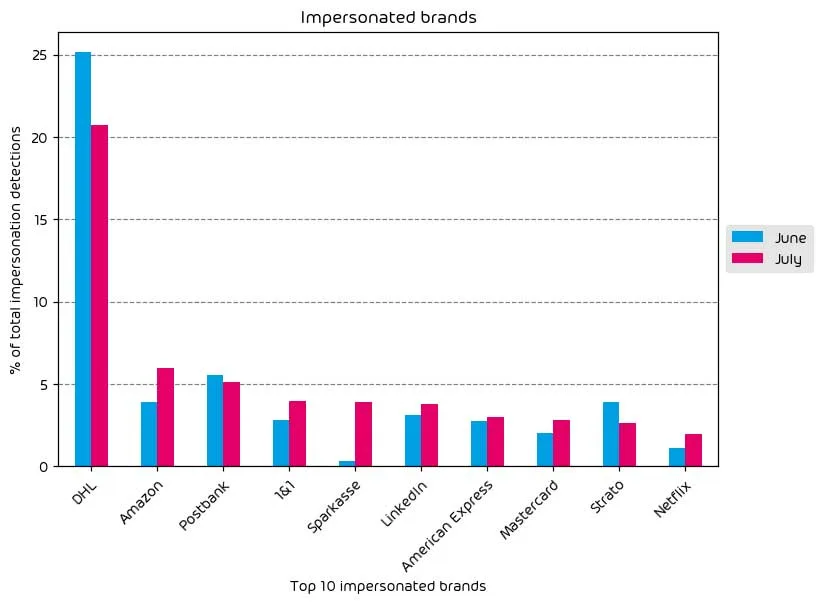
This month’s data also shows that we’ve had some changes in brand impersonation attacks. For example, even though impersonation attempts for DHL saw a net decrease from last month, it remains the most largely impersonated company for these styles of attacks BY FAR. Amazon impersonation attempts saw a noted increase as well. Shipping companies remain high on the list, with an apparent reason for this. Many of us are waiting for a package delivery at any given time. If a threat actor just happens to deliver one of these malicious “shipping emails” to a user’s inbox at just the right time, it’s probable the user may fall victim to the payload. Threat actors see a significant degree of success in this style of attack.
Other notable monthly increases include Sparkasse (German Banking), LinkedIn, Mastercard, and Netflix. Among those increases, nothing has been out of the norm for the last 30 days except a minor spike in Netflix impersonation attacks. Even though there isn’t a high chance of pulling sensitive information, like payment details, out of a target’s Netflix account, threat actors can still leverage the knowledge gained for use in other attacks, such as credential stuffing, or sell access to the Netflix accounts in Darknet forums for lower prices.
Other Interesting Findings in Our Data This Month
Every month we keep a lookout for anything else that’s interesting in our data. This often surfaces new attacks, attack types, and threat-vector variations. During the last month, we’ve identified several cases where a malicious QR code is embedded within an email. While that isn’t out of the ordinary, and we’ve identified increased use of malicious QR codes industry-wide in the past years, there is a stark difference in what we’ve observed in this case.
A typical defense against malicious QR codes (if you don’t have a security vendor that scans them like Hornetsecurity) is to scrutinize the associated URL of the QR code highly. We’ve seen a trend in the last month where threat actors are obfuscating the use of IP addresses within their URLs by making them appear without separated octets. For example, the URL http://194.6.209.34 pointing to the www.hornetsecurity.com web server can also be written as http://3255226658. End users have been somewhat trained to be suspicious of IP addresses. With this formatting, a potentially malicious link may pass this trained practice for some users.
Major Incidents and Industry Events
There are several exciting developments in the cybersecurity news space for the month of July.
Notably, the MOVEit file-transfer software vulnerabilities continue to plague the industry. This attack stems from a collection of SQL injection attacks that enable privilege escalation and unauthorized access to target environments. The most recent vulnerabilities are being tracked as CVE-2023-36934 if you want to read more about it.
The Clop ransomware gang continues to exploit these vulnerabilities, and has even started double-extortion attacks on targets by threatening to leak stolen data if the ransom isn’t paid. Meanwhile, the number of breaches attributed to these vulnerabilities continues to stack up. The affected organizations now include Deloitte, the Hallmark channel, and various government entities.
The use of generative AI in cyber-attacks has continued to evolve over the past month. The Independent has reported that as many as 200k compromised OpenAI accounts are now for sale on the dark web. This is up from the 100k number that we commented on in last month’s report. On top of that, the hacking community has now developed its threat-actor variant of ChatGPT, dubbed WormGPT, which lacks any of the controls or ethical barriers that are present in ChatGPT itself. This highlights that generative AI will continue to change the threat landscape and make launching attacks more accessible to less skilled threat actors.
Our final news item for the week focuses on Microsoft directly. In a July 11th announcement, Microsoft indicated that a Chinese threat-actor designated Storm-0558 had somehow gained access to a Microsoft account consumer signing key. The threat actor then used the stolen signing key to forge authentication tokens that allowed them unauthorized access to data in Exchange Online, and Outlook.com accounts across “approximately 25 organizations” Experts were quick to point out that the potential list of impacted services was likely more than just Exchange Online and Outlook.com. Some commented that the list potentially includes services like SharePoint, OneDrive, and Teams. According to Microsoft, the vulnerability that led to this breach has now been patched.
It’s still early days for this breach, and more information will be forthcoming, but this highlights the growing industry problem of “vendor overdependence”. For those unfamiliar with this concept, it’s the act of utilizing one vendor for an increasing percentage of critical business functions with a potential lack of independent oversight. In this case, you have the same vendor (Microsoft) not only holding onto and providing access to customer production data through services like Microsoft 365 but also the party involved in providing Security for those services. There is a potential conflict of interest.
Arguably, third-party involvement in this recent case wouldn’t have helped, as the breach was due to a vulnerability in Microsoft’s authentication process. Still, the point is that a third party can help keep an objective eye on potential threats. It is generally healthy for the IT security community and businesses to consume services from a major cloud provider.
Predictions for the Coming Months
- We predict that malicious use of generative AI will continue to increase and will likely be part of this section of our monthly report for some time. It’s clear that generative AI is the next stage of the ever-present “arms race” between blue teams and threat actors. Knowing that new dark-web-specific generative AI tools are being developed (like WormGPT), it’s reasonable to assume that attacks like Business Email Compromise (BEC) will likely increase. These tools provide the necessary skills and access for lucrative attacks like BEC to threat actors lacking the skills needed.
- The fallout from the Storm-0558 Microsoft breach will be a recurring theme as more information comes to light in the coming weeks. The conversation around vendor overdependence and the role of 1st party providers in the cloud will likely come under heavy scrutiny by the community and government entities.
- Finally, we suspect persistent threats like Qakbot will continue to evolve. While there are signs that the threat actor behind Qakbot has pivoted to other styles of attacks with lower volume, the threat remains. We will continue to provide updates on persistent email threat actors like Qakbot and Emotet on a month-to-month basis as needed.
Expert Commentary from Hornetsecurity
We asked some of our internal experts about the news from this month. We have posted their responses below!
From Andy Syrewicze, Security Evangelist, on vendor overdependence:
There’s something to be said about a tightly integrated service like M365. I get it, but some service areas should only be provided by the same vendor with heavy oversight. For example, productivity solutions (like M365) and Security. There is an inherent conflict of interest in a vendor selling a solution like M365, which then is also the party responsible for transparent Security. As discussed in a recent episode of the Security Swarm Podcast, there is very little transparency on the state of Security internally within many major cloud platforms, and third-party security providers play a key role in keeping everything transparent and keeping everyone honest. Microsoft seems to have done an OK job in terms of communication with the recent Microsoft Cloud breach, but it’s sure to bring the whole conversation around vendor overdependence back to the fore in the coming weeks, and frankly, it should.
From Jan Bartkowski, Team Lead Security Architecture & Engineering, on the challenges blue teams face with cloud applications:
Security teams face the difficult challenge of monitoring all IT resources their company uses. Monitoring the activity on cloud applications is crucial but often impossible or heavily restricted: Many cloud applications simply do not provide auditing logs or similar options to help identify suspicious behavior. Microsoft’s recent announcement of expanding their logging in the non-E5 plans was overdue. Locking, sometimes even basic security features behind additional required licenses, is a way too common practice that vendors and customers should question to enable security teams.
Monthly Recommendations
Given the current state of the landscape, what are our recommendations for this month?
- If your organization uses the MOVEit file transfer software and still needs to apply the patches for the recent string of vulnerabilities, please do so ASAP.
- With email threats increasing across categories this month, now is an excellent time to evaluate your email security posture. Look at the solutions you have in place and ensure the proper rules and mitigations are present. If you’re in need of a solution in this space, we offer a robust and feature-rich solution for email security in our 365 Total Protection suite.
- With the rise in Business Email Compromise attacks, end users must learn to detect fraudulent emails well. If you still need to invest in security training for your end users, do so now. Like the point above, if you need a solution, we have an effective and time-friendly solution in the Hornetsecurity Security Awareness Service.
- Even though Microsoft claims the damage from the Storm-0558 breach is contained, check your security and M365 audit logs for suspicious behavior. Ideally, you have a security logging solution, e.g., SIEM, that highlights suspicious user logins and interactions for you. Ensure you have internal processes defined on how to handle security incidents.
About Hornetsecurity
Hornetsecurity is a leading global provider of next-generation cloud-based security, compliance, backup, and security awareness solutions that help companies and organisations of all sizes around the world. Its flagship product, 365 Total Protection, is the most comprehensive cloud security solution for Microsoft 365 on the market. Driven by innovation and cybersecurity excellence, Hornetsecurity is building a safer digital future and sustainable security cultures with its award-winning portfolio. Hornetsecurity operates in more than 120 countries through its international distribution network of 12,000+ channel partners and MSPs. Its premium services are used by more than 125,000 customers.


