

How DMARC Prevents Email Spoofing and Why It Matters
Trust. Trust is a critical currency for so many interactions we have, both in our personal lives and in business. We trust that invoices from service providers are genuine, we trust our boss when we are asked to perform a task in haste, and we trust that a colleague or CEO is in genuine distress when they ask for help. Do these scenarios sound familiar? These are some of the ways cyber criminals misuse our trusting instincts in Business Email Compromise (BEC) attacks using a technique called email spoofing.
In its simplest form, email spoofing is a means by which an email appears to come from a trusted person or organization. As email is a critical tool for businesses, email spoofing is a significant threat and often used as a launching point for many other types of attacks. These attacks can have far-reaching consequences, may have legal implications and can result in a loss of reputation and revenue. To reduce the likelihood and impact of these attacks, businesses need to focus on protecting the integrity of mail domains and ensure that email authentication mechanisms they use are suitably configured, maintained, and monitored.
Understanding DMARC
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an effective technology email authentication protocol businesses can use to prevent their email domains from being misused to perform email-related attacks using email spoofing. DMARC works with two other authentication protocols, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to ensure email originating from domain is legitimate.
Let’s discuss the purpose of each DNS record, how these authentication protocols differ, and how they work together to create a layered defense against email spoofing:
- SPF – Includes the IP addresses or mail servers are allowed to send emails on behalf of that domain.
- DKIM – Contains a digitally signed record to provide an assurance that a message has not been tampered with in transit.
- DMARC – Uses a policy to instruct receiving mail servers on how to handle emails from that domain when they fail either SPF or DKIM checks, or both.
Now that we have more details about the protocols and their DNS records, we can use this to walk through the process for what happens once an email arrives on a mail server. For brevity, “receiving” refers to the receiving mail server, and “sending” the mail server from which the email was sent.
- SPF checks the sending server’s SPF record to verify that the email was sent from an authorized IP address. If the IP address is listed in the SPF record it passes the check, otherwise it fails.
- DKIM checks if the email is cryptographically signed with the private key of the sending domain, then validates it against the corresponding public key. A positive match results in a passed check, otherwise it fails.
- DMARC checks that the “From” address in the email is aligned to the same email domain that SPF and DKIM validated in their own checks.
- Finally, the policy tag (“p”) in the sending domains DMARC record tells the receiving server how to treat the email based on the check results.
| Value (policy tag) | Result |
| None | Deliver the message |
| Quarantine | Treat the messages as spam |
| Reject | Block the message |
DMARC policies provides flexibility for businesses to decide how prescriptive they want to be when telling mail servers who receive the emails to allow, reject or quarantine suspicious emails. For a business that has just configured DMARC for example, they should probably start with the “none” policy and use the reports they receive from receiving email servers to refine and improve the configuration of their SPF and DKIM records.
Once satisfied with how well the other two authentication protocols are configured, they could change the policy to quarantine suspicious emails and start using the “pct” tag to specify the percentage of emails to which the quarantine DMARC policy should be applied. Finally, confident that the configuration of the authentication protocols is optimized to strike the right balance, change the DMARC policy to outright reject any emails received from their domain that fail DMARC.
Configuring these DNS records can get a bit tricky, so I encourage you to have a look at these guides and resources to get you started:
- Official website for DMARC
- Background, step-through of the email authentication process with DMARC, and deployment of DMARC using the available tags
It should be evident by this point that to ensure email delivery success for everyone, it relies on as many businesses as possible becoming DMARC compliant. The good news is that there’s been a steady increase of businesses whose DMARC DNS records are being actively used, as tracked and recorded here.
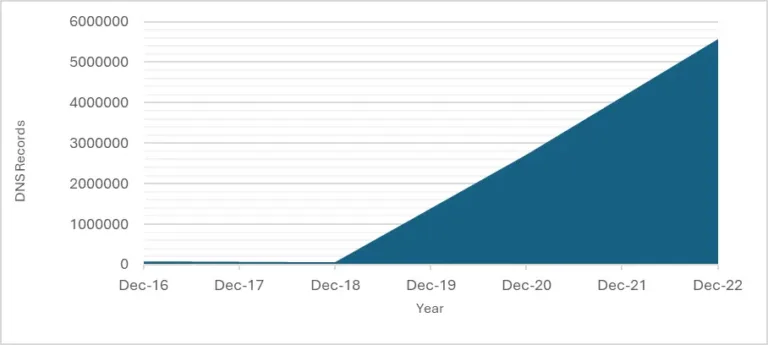
Even though the growth since December 2022 isn’t yet available, I think it’s safe to say that adoption will have only increased since then. Particularly with Yahoo and Google leading the charge, announcing in late 2023 that from February 2024 the requirement for any service sending more than 5,000 messages a day to have a DMARC policy in place.
You don’t have to look much further than this case study shared by Maropost from 2018 to see just how effective implementing DMARC really can be! Their clients faced an unusual issue in which even though SPF and DKIM checks were passing, emails were still being marked as spam. Implementing DMARC resulted in all phishing alerts disappearing, and more importantly a 100% success rate for email delivery!
In case that wasn’t enough to convince you, here’s one more case study by DMARC Report from February 2023, which has some very interesting insights that demonstrate DMARC’s effectiveness in reducing email spoofing and improving security for globally recognized organizations like PayPal and LinkedIn.
How DMARC Prevents Email Spoofing
You might have noticed that I’ve mentioned a few times already about how DMARC is used to combat email spoofing, so let’s talk about what it is, and then the mechanisms DMARC uses to prevent it. In its simplest form, email spoofing is a technique used by bad actors to send an email that appears to originate from a particular domain, commonly one that is reputable or trusted, when it does not.
Email spoofing is a really significant threat. FBI’s 2023 Internet Crime Report found that of the 880,418 complaints received from the American public, almost 34% of respondents (298,878) reported complaints related to spoofing. In more positive news, from that same report, 75% of companies said that they are in the process of rolling out DMARC!
Here are three key mechanisms that makes DMARC highly effective at stopping spoofing:
- Alignment
SPF checks the “Return-Path” value in the header, while DKIM checks the “d=” tag in the DKIM signature. These need to match (align) to the “From” value in the header.
- Policy Enforcement
The action to take for emails that fail the DKIM or SPF checks.
- Reporting
Aggregated reports with insights and statistics domain owners can use to improve their overall email security controls and practices.
In the introduction of this blog, I touched on how email spoofing is used by cyber criminals to perform BEC attacks, and this is good point at which to provide some examples of common email spoofing scenarios and how DMARC addresses them.
| Scenario | DMARC Protection |
| A fake email appearing to originate from the addresses of the CEO, or another C-suite executive is sent to one or more employees asking for immediate payment. | A spoofed email will be rejected or quarantined by a DMARC policy that specifies what to do if the SPF and DKIM checks fail. |
| An attacker sends a phishing email with a link to a website with a similarly named domain as that in the target business to steal their credentials. | These will be marked as spam with a DMARC policy set to quarantine emails if they fail the SPF or DKIM checks. |
| A fake invoice impersonating a legitimate business is sent to an organization requesting immediate payment. | The SPF record for the email domain being impersonated specifies the IP addresses authorized to send emails on their behalf, and the DMARC policy will mark as spam or reject when this SPF check fails. |
DMARC Manager
DMARC Manager from Hornetsecurity empowers organizations to actively control and monitor all emails sent under their domain, preventing unauthorized use of their brand in phishing attempts and spam campaigns. It provides visibility into who else is sending emails under a domain and returns control to the domain owner, strengthening and securing brand reputation. The tool provides an admin with an easy way to set up and maintain DMARC, DKIM and SPF best practice-policies for multiple domains.
Are you unsure if your domain is at risk? Check out our free security check to analyze your domain’s SPF, DKIM, and DMARC settings.

By analyzing incoming DMARC reports, DMARC Manager offers insights into email delivery and authentication status, helping identify legitimate campaigns and potential spoofing attempts. Additionally, it enables businesses to enhance their email marketing strategies by ensuring that their emails are perceived by customers as authentic and trustworthy. This comprehensive tool centralizes management of various domains and configurations, facilitating DMARC compliance while protecting your brand’s email reputation.
Request a demo today and see how DMARC Manager safeguards your domains against email impersonation, phishing, and spoofing with intuitive management:
Conclusion
Cyberattacks using email spoofing can be incredibly damaging, and we’ve discussed the anecdotal evidence which shows that using SPF and DKIM alone is no longer sufficient when combating email spoofing and enhancing email security. Implementing DMARC and using its key mechanisms like alignment and policy enforcement are powerful tools to prevent email spoofing.
DMARC shouldn’t be considered as the only tool though. Establishing a comprehensive email security strategy plays a significant role in developing your defense-in-depth approach for email protection. These protection settings will need to be regularly enhanced, informed by the DMARC reports received from other mail servers. Keeping up with all of this can be complex and time-consuming, but using a DMARC manager can make it much easier.
Although DMARC will do a lot of the hard work for you, high security standards are still needed and must be regularly maintained, monitored, and updated to effectively counteract email spoofing. An overall proactive approach to email protection is vital to preventing security threats and protecting your brand and reputation.
FAQ
The DMARC Manager is a tool that centralizes the setup and maintenance of DMARC, SPF, and DKIM records. It simplifies email security by providing insights from DMARC reports, ensuring unauthorized emails are blocked and legitimate emails are delivered.
It analyzes DMARC reports to identify who is sending emails from your domain, detects spoofing attempts, and allows you to enforce strict email policies across all domains.
Yes, it improves deliverability by ensuring emails are trusted and not flagged as spam, helping your campaigns reach recipients securely and effectively.
