Ransomware
Was ist Ransomware? Wie schützt man sich davor?
Ransomware, oder auch Verschlüsselungstrojaner oder Erpressungstrojaner, ist ein Schadprogramm für Computer, welches dafür sorgt, dass der Rechner für den Nutzer gesperrt und nur gegen ein Lösegeld wieder freigeschaltet werden kann. Wie genau eine Ransomware funktioniert, wie groß die Gefahr vor Ransomware ist und wie man sich vor Ransomware schützen kann, klären wir in diesem Artikel.
Was ist Ransomware?
Das Wort „Ransomware“ stammt aus dem Englischen und enthält den Begriff „Ransom“, was übersetzt „Lösegeld“ bedeutet.
Ransomware ist Malware, die unbemerkt auf dem PC einer fremden Person installiert wird. Der Unterschied zu anderer Schadsoftware ist der, dass Ransomware mit dem Benutzer des betroffenen Systems direkt in Kontakt tritt. Die Schadsoftware verschlüsselt entweder die Dateien oder den gesamten Computer. Der Hacker hat die Kontrolle über den Computer und fordert ein Lösegeld. Solange das Opfer das Lösegeld nicht bezahlt, bleibt das Gerät verschlüsselt.
Befindet sich das infizierte Gerät in einem Netzwerk, beispielsweise in einem Unternehmen, kann die Schadsoftware sich auf das gesamte Netzwerk ausbreiten und alle Geräte in diesem Netzwerk verschlüsseln. So können komplette Unternehmen, Krankenhäuser und Universitäten lahmgelegt werden.
Ransomware und Malware: Was ist der Unterschied?
Malware ist der Überbegriff jeglicher Programme, die einem Gerät Schaden zufügen. Sowohl Viren, als auch Ransomware sind somit Malware. Bei Ransomware handelt es sich um Malware, die sich bei der Aktivierung verbreitet und Dateien im infizierten Computernetzwerk verschlüsselt. Nur durch das Bezahlen eines Lösegeldes wird das Gerät vom Hacker wieder entschlüsselt.
Ist Ransomware ein Virus?
Nein, Ransomware ist kein Virus. Viren und Ransomware sind zwar beides Malware, unterscheiden sich jedoch. Viren infizieren Daten und replizieren sich. Ransomware hingegen verschlüsselt Dateien. Aus diesem Grund ist auch der Name „Cryptovirus“ irritierend.
Was ist ein Cryptolocker / Cryptotrojaner?
Ein Cryptolocker gehört zur Familie der Ransomware. Das Ziel ist es Lösegeld vom gehackten Opfer zu erhalten. Der Cryptolocker infiziert die Dokumente des Users und zwingt ihm zu einem Lösegeld. Ransomware-Angriffe durch Kryptotrojaner können schwere (finanzielle) Folgen für Unternehmen haben. Kryptotrojaner haben sogar bereits einige Firmen in ihrer Existenz bedroht oder sogar in die Insolvenz getrieben. Es ist die Horrorvorstellung schlechthin: Ein Mitarbeiter eines Unternehmens fängt sich auf dem Dienst-Rechner einen Kryptotrojaner ein. Anschließend dauert es nicht lange, bis sich der Schädling über das gesamte Firmennetzwerk ausgebreitet hat.
Ransomware – Wie groß ist die Gefahr?
Die Gefahr vor Ransomware ist größer als man denkt. Vor allem Unternehmen sollten auf der Hut vor infizierten E-Mails sein. Bereits 2018 konnten Cyberkriminelle 8 Milliarden Euro erbeuten. Eine beträchtliche Summe, doch 2019 konnte noch mehr erbeudet werden: Der generierte Schaden hat sich im Jahr 2019 gegenüber dem Vorjahr sogar mehr als verdreifacht, auf ca. 24 Milliarden Euro.
Wie kommt es zu diesem schnellen Anstieg an erfolgreichen Ransomware-Attacken? Hacker haben die richtige Nische gefunden. Ausgeklügelte Techniken und einige wenige Informationen über die Mitarbeiter eines Unternehmens (Social Engineering) ermöglichen es Hackern, die IT-Infrastruktur mit einer einfachen bösartigen E-Mail zu infizieren. Besonders häufig wurden Krankenhäuser Opfer von Verschlüsselungs-Angriffen.
Wie funktioniert Ransomware?
Meistens beginnt es mit einer klassischen Phishing E-Mail, die als Köder zum Download einer infizierten Datei dient. Meistens geschieht die Infizierung mit der Ransomware durch eine verseuchte PDF-, DOC- oder XLS-Datei.
Durch Öffnen der schädlichen Datei, hat der Täter die größte Hürde überwunden. Die Installation auf dem jeweiligen System erfolgt. Dabei bleibt zu erwähnen, dass die Installation unabhängig von der Aktivierung der Ransomware ablaufen kann. Die Ransomware-Attacke kann somit frühzeitig vorbereitet, aber beispielsweise erst zu einem späteren Zeitpunkt tatsächlich gestartet werden.
Sobald die Ransomware aktiviert wird, beginnt der eigentliche Schaden: die Verschlüsselung beginnt. Dabei können einzelne Dateien auf einem System oder sogar mehrere Systeme innerhalb eines Unternehmensnetzwerkes verschlüsselt werden.
Von nun an hat der User keinen Zugriff mehr auf bestimmte Dateien oder seinen gesamten Rechner. Seine Admin-Rechte hat er komplett verloren. Die Kontrolle liegt in den Händen des Hackers. Sobald alles verschlüsselt ist, erscheint eine Benachrichtigung auf dem Bildschirm des Opfers. Hier fordert der Hacker ein Lösegeld, um die Ransomware wieder zu entfernen. Sobald dieser Vorgang abgeschlossen ist, müssen die Angreifer nur noch darauf warten, dass das jeweilige Opfer die Lösegeldzahlung vornimmt. Die Kopplung der Lösegeldforderung an eine Deadline ist ein probates Mittel der Cyberkriminellen, um den Druck auf die Betroffenen zu erhöhen. Sollten die Inhaber der Systeme bis zum Zeitpunkt der Deadline keine Zahlung getätigt haben, erhöht sich entweder die Lösegeldforderung oder es wird mit dem Löschvorgang von Daten begonnen.
Ransomware-Attacken können zu großen Schäden führen, vor allem bei Unternehmen. Experten und Behörden raten in der Regel vom Zahlen eines Lösegeldes ab. Oft bleibt den Opfern aber keine andere Wahl, als auf die Gutmütigkeit der Hacker nach der Zahlung zu hoffen. Häufig bleibt die Entschlüsselung nach Zahlung des Lösegeldes nämlich aus.
Der Ablauf eines Ransomware-Angriffs am Beispiel von Wanna Cry
Stufe 1: Tarnung und Übersendung
Angriffsstrategie:
Die Schadsoftware wird in der Regel durch den Cyberkriminellen geschickt verschleiert und das Schlüsselpaar für den Verschlüsselungsvorgang ebenfalls eingebettet . Um mit der Angriffsausführung zu beginnen, greift der Angreifer auf eine Schwachstelle zurück. Während bei herkömmlichen Ransomware-Angriffen Phishing-Mails zur Anwendung gelangen und so die infizierten Dateianhänge eingebunden oder Links platziert werden, kann wiederum bei anderen Ausprägungen auch eine Webseite sowie schadhafte Werbung als Übertragungsweg dienen. Sobald der Betroffene den Dateianhang geöffnet hat, ist der Köder des Angreifers erfolgreich gewesen. Der Fortsetzung des Angriffs steht dann nichts mehr im Weg.
Gegenmaßnahmen zur Verteidigung:
Unternehmen sollten sich zunehmend bemühen, die Gefahren, die von Ransomware ausgehen, nachvollziehen zu können. Hierzu benötigen die Verantwortlichen in Unternehmen eine gewisse Weitsicht, die Praxiserfahrungen und Wissen vereint.
Insbesondere die Weiterbildung von Mitarbeitern gehört hier zu den wesentlichen Punkten. Dies gilt vor allem für den Fall, dass eine effektive Angriffsabwehr gegenüber Ransomware im Unternehmen etabliert werden soll.
Aufgrund der Aktualität von Ransomware-Angriffen auf Unternehmen, ist dies genau der richtige Zeitpunkt, um Mitarbeiter für diese Problematik zu sensibilisieren.
Insbesondere ein Spamfilter für den E-Mail-Verkehr, kann dabei helfen, den Eingang von etwaigen schadhaften Inhalten zu verhindern. Nur so können Sie auf lange Sicht, den Zugang zu Ihrem System im Unternehmen sicherstellen.
Zur präventiven Vorbeugung bietet es sich zudem an, auf eine Sandbox-Engine zurückzugreifen, die beispielsweise mit Hornetsecurity Advanced Threat Protection optional erhältlich ist.
Dieses dort enthaltene Tool untersucht das Verhalten von E-Mail-Dateianhängen bei Öffnung und filtert sie bei einem positiven Fund heraus. So haben Mitarbeiter eines Unternehmens die Möglichkeit, Angriffe bis ins Detail nachvollziehen zu können.
Stufe 2: Download und Ausführung
Angriffsstrategie:
Von Wanna Cry unabhängige Ransomwarestämme benötigen lediglich einen Klick, um ein Exploit auszuführen. Daneben wird der Payload der Malware über das TOR-Netzwerk heruntergeladen und auf dem Zielsystem installiert. Durch die Nutzung des EternalBlue Exploits im SMB-Protokoll ist es möglich, die Schadsoftware unbemerkt einzuschleusen. Gleichzeitig versucht der betroffene Rechner, bis zu 10 weitere Systeme über den SMB-Port zu erreichen. Dieses Verhalten ist für viele Clients nicht ungewöhnlich, weshalb herkömmliche Antivirenprogramme die Infektion zunächst nicht erkennen.
Gegenmaßnahmen zur Verteidigung:
Bei der Ausführung von Schadsoftware, werden Prozesse durchgeführt, die von den herkömmlichen Abläufen abweichen. Sobald solche Abweichungen von Benutzern eines Systems oder Netzwerks wahrgenommen werden, heißt es: Strom aus! Rechner vom Netz! Die Sensibilisierung der Mitarbeiter bei auftretenden Veränderungen im System ist für ein nachhaltiges Reporting elementar. Denn auf dieser Basis können die entsprechenden Notfallmaßnahmen umgehend eingeleitet werden. Dies beinhaltet ebenfalls die Aktualisierung von Sicherheits-Patches. Gleiches gilt für die stetige Aneignung von Wissen hinsichtlich neuer Bedrohungen. Dadurch können Unternehmen wesentlich frühzeitiger auf einen „worst case“ reagieren.
Stufe 3: Verschlüsselung
Angriffsstrategie:
Auch der Verschlüsselungsvorgang bei Wanna Cry unterschiedet sich nicht wesentlich von dem einer anderen Ransomware. Ziel ist auch hier die Verschlüsselung des Systems, damit der Betroffene nicht mehr auf seien Dateien zugreifen kann. Das System des Betroffenen ist folglich unbrauchbar. Jede Datei wird mit einem separaten symmetrischen AES-Schlüssel verschlüsselt. Zudem wird jeder benutzte AES-Schlüssel separat mit einer 2048bit RSA Public-Key-Encryption verschlüsselt. Dieser Vorgang macht die Datenwiederherstellung für den Anwender unmöglich.
Gegenmaßnahmen zur Verteidigung:
Die Hauptproblematik bei den jeweilig unterschiedlichen Ransomwarearten liegt darin, dass es für eine Vielzahl der Angriffe keine entsprechenden Decryptor gibt – so wie es auch lange Zeit bei Wanna Cry der Fall gewesen ist. Lediglich ein Frühwarnsystem bietet Unternehmen die Möglichkeit, den Vorgang verschiedener Systeme im Netzwerk zwar nicht ganz zu verhindern, jedoch deutlich einzuschränken. Exemplarisch ist hier Advanced Threat Protection anzuführen. Mit Hilfe von Hornetsecurity ATP können Sie polymorphe Viren in E-Mails rechtzeitig aufspüren. Dadurch kann ein „worst case“ mit größerem Ausmaß deutlich eingeschränkt werden.
Stufe 4: Die Verbreitung von WannaCry
Angriffsstrategie:
Im Vergleich zu anderen Formen, nutzt Wanna Cry als Einfallsvektor ungepatchte Systeme, die über den EternalBlue Exploit im SMB-Protokoll die Ransomware folglich auf Netzwerkebene verbreiten. Hierbei handelt es sich um eine zusätzliche Verbreitungsmethode. Denn normalerweise verbreitet sich Ransomware ebenfalls lokal über die einzelnen, freigegebenen Netzwerkfestplatten.
Gegenmaßnahmen zur Verteidigung:
Die Kontrolle des Netzwerkverkehrs – insbesondere des Datenaustausches – kann effektiv dazu beitragen, Angriffe dieser Art einzuschränken. Im Vordergrund steht die Beschränkung der Zugriffsrechte.
Hierbei handelt es sich um eine zentrale Verteidigungsstrategie gegen Wanna Cry. Insbesondere das Zugreifen von Arbeitsplatzrechnern auf sensible Unternehmensdaten im Netzwerk kann durch ein entsprechendes Zugangsmanagement zielgerichtet beschränkt werden.
Die Zugangsrechte sollten hierbei immer derart ausgestaltet sein, dass nur die Dateifreigaben erfolgen, die für die Erledigung des täglichen Aufgabenbereichs der Mitarbeiter auch wirklich benötigt werden.
Unter Berücksichtigung dieser Möglichkeiten, die Sicherheitsbeauftragte bzw. Netzwerkadministratoren in einem Unternehmen haben, können Ransomware-Angriffe, wie die durch Wanna Cry eingegrenzt werden.
Stufe 5: Die Lösegeldzahlung
Angriffsstrategie:
Um als betroffenes Unternehmen wieder an die Daten zu gelangen bzw. Zugang zum System zu erhalten, wird, wie wir bereits wissen, ein einzigartiger Schlüssel zur Entschlüsselung benötigt. Diesen bekommen die Betroffenen nur in Aussicht gestellt, wenn die Zahlung einer bestimmten Lösegeldsumme in einer Online-Währung (z.B. durch Bitcoin) erfolgt.
Gegenmaßnahmen zur Verteidigung:
Als betroffenes Unternehmen ist es wichtig, zu verstehen, dass die Zahlung eines Lösegelds nicht zwangsläufig zur Erlangung des Zugriffs auf die eigenen Daten führt. Ein Ransomware-Angriff ist unweigerlich eine Angriffsform mit erpresserischer Absicht. Aus diesem Grund raten wir, aber auch andere IT-Security-Experten von der Zahlung eines Lösegelds ab. Denn jede Zahlung sorgt letztlich dafür, dass die Täter Ransomware als Angriffsform – aufgrund der Lukrativität – weiter etablieren.
Ein für den eintretenden „worst case“ vorhandener Notfallplan ist daher besonders wichtig. Natürlich kann es – wenn auch nicht empfohlen – in einer solchen Situation von Relevanz sein, im Detail zu wissen, wie die Zahlung durch einen Mitarbeiter über ein Online-Bezahlsystem in der Währung Bitcoin zu erfolgen hat. Schließlich könnte dies im Idealfall den Zugriff auf die Daten bedeuten. Wesentlich wichtiger erscheint jedoch die Implementierung von Backup-Lösungen in Unternehmen, die letztlich den Verlust von Dateien bis zu einem bestimmten Grad verhindern. Hierbei kommt es natürlich auf die jeweilig gewählten Backup-Zeitpunkte sowie der Backup-Verfahren an. Erfolgt die Sicherung beispielsweise auf Magnetbänder, kann Wanna Cry darauf nicht zugreifen.
Ransomwareschutz
Um sich vor Ransomware zu schützen, sollten Unternehmen proaktiv handeln und einen Cybersecurity-Plan gegen Malware entwickeln. Da es sehr schwer ist Ransomware zu erkennen und zu bekämpfen, sollte man verschiedene Schutzmechanismen nutzen. Der wichtigste Schutz ist die Schulung und Sensibilisierung von Mitarbeitern. Nur wer weiß, dass es Ransomware gibt und wie diese vorgeht, der kann solche Angriffe auch erkennen.
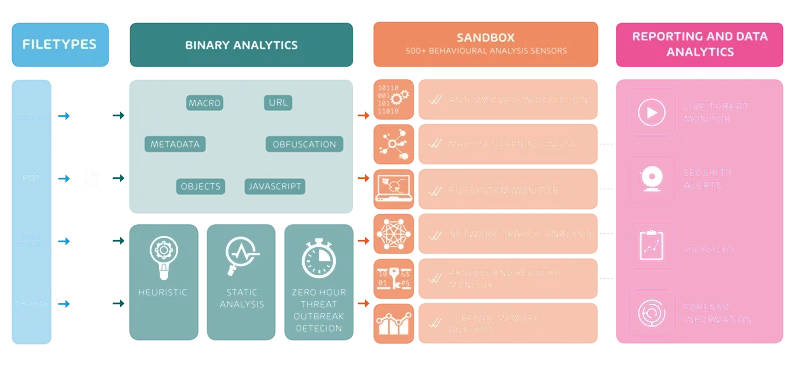
Da das E-Mail-Postfach eines der klassischen Einfallstore von Schadsoftware ist, sollte ein guter Spamfilter alle ausführbaren Anhänge, Zip-Dateien und Microsoft-Dokument-Makros blockieren oder mindestens in Quarantäne schieben. Hornetsecurity bietet eine Lösung und filtert mit Spam and Malware Protection diese Gefahren heraus, bevor die Mail zugestellt werden kann.
Die ständige Weiterentwicklung der Filter sorgt dafür, dass den immer professionelleren Angriffsmitteln und –methoden entgegengewirkt wird. Mit einer der höchsten Erkennungsrate am Markt (99,99%) überprüfen 18 verschiedene Virenscanner den E-Mail-Verkehr. Ein verseuchter Anhang, der mehrfach verpackt und unkenntlich gemacht wurde, wird von dem Virenscanner von Hornetsecurity erkannt und als Spam kategorisiert.
Advanced Threat Protection geht noch einen Schritt weiter und erkennt zuverlässig Ransomware-Attacken sowie unterschiedliche Malware-Arten, die noch unbekannt sind. Hornetsecurity Advanced Threat Protection (ATP) bietet Lösungen auf breiter Ebene an. Hierzu gehören URL-Rewriting und URL-Scanning.
Sollte ein Angriff erfolgreich sein, ist es wichtig, aktuelle Backups parat zu haben. So kann ein älterer Stand, ohne Infizierung, aufgespielt werden. Dies hält den Datenverlust möglichst gering. Die Sicherung kann manuell oder automatisch durchgeführt werden. Eine Cloud-Lösung für Unternehmen wäre z.B. eine Möglichkeit der Datensicherung.
Für Ransomware-Attacken wird primär der Angriffsvektor E-Mail genutzt. Gut getarnt, gelangen Sie als PDF-, EXE- oder JPEG-Datei auf den Zielrechner des Mitarbeiters im betroffenen Unternehmen. Die Anzeige von Dateiendungen ist in den meisten E-Mail-Clients standardmäßig deaktiviert, weshalb der Nutzer das Format der Datei meist nicht auf den ersten Blick erkennen kann. Ungewollt werden die infizierten Dateien geöffnet und die Ransomware ausgeführt. Folglich ist es wichtig, dass Sie über die Einstellungen des E-Mail-Clients die Ansicht von Dateiendungen aktivieren.
Das Schließen von Schwachstellen ist ebenfalls sehr wichtig. Microsofts Remote Desktop Protokoll dient als Schwachstelle. Durch diese Funktion kann sich die Ransomware im Einzelfall innerhalb des lokalen Netzwerkes verteilen. So verteilt sich die Schadsoftware innerhalb kürzester Zeit im Netzwerk.
Auch das Updaten der Systeme ist zwingend notwendig. Je älter die Software, desto mehr Einfallstore sind bekannt und vorhanden. Wer heute noch Windows 7 oder sogar Windows XP nutzt, der braucht sich nicht wundern, wenn der Computer infiziert und verschlüsselt wird. So nutzte WannaCry eine Lücke in veralteten Windows-Systemen (EternalBlue). Sie wurde von vielen Unternehmen einfach ignoriert. Updates bzw. Patches wurden nicht durchgeführt. Dadurch kam es zu einer Vielzahl von erfolgreichen Ransomware-Attacken auf Unternehmen.
Gibt es Ransomware Scanner?
Ist die Ransomware bereits auf dem Computer, ist es meistens schon zu spät. Sollte die Schadsoftware noch nicht aktiviert worden sein, hilft ein aktuelles Anti-Viren-Programm. Am sinnvollsten sind jedoch Lösungen, die Ransomware bereits erkennen, bevor diese auf den Rechner gelangt. Hier helfen ebenfalls klassische Virenscanner, wie zum Beispiel GDATA, die gegen jede Art von Malware vorgehen.
Geht es jedoch um den Schutz vor infizierten E-Mails, sollte ein erweiterter Spamfilter zum Einsatz kommen. Hier unterstützt zum Beispiel ein Anti Ransomware Scanner wie die Cloud-Lösung Advanced Threat Protection von Hornetsecurity. So schützt der Service vor Angriffen mit Ransomware wie Locky, Tesla oder Petya, filtert Phishing-Mails heraus und wehrt sogenannte Blended Threats ab. Um dies zu bewerkstelligen, nutzt Hornetsecurity ATP verschiedene Erkennungsmechanismen: So kommt neben einer Sandbox auch das URL-Rewriting und URL-Scanning zum Einsatz. Freezing, also das „Einfrieren“ von verdächtigen E-Mails, ist ebenfalls Bestandteil von Hornetsecurity ATP.
Ransomware entfernen: was kann ich nach einem Angriff noch machen?
Ist die Ransomware erst einmal auf dem Rechner und hat diesen infiziert, dann gibt es meistens keinen guten Ausweg mehr. Entweder man bezahlt das Lösegeld (Die Polizei rät davon ab) oder man setzt den Computer neu auf (Mit der Hoffnung auf ein aktuelles Backup). Für einige Ransomware-Angriffe gibt es jedoch Entschlüsselungs-Werkzeuge. Besuche dafür einfach die Seite https://www.nomoreransom.org/crypto-sheriff.php?lang=de
No More Ransom bietet Entschlüsselung von Ransomware für über 50 verschiedene Ransomware-Typen.
Welche Typen von Ransomware gibt es?
Grundsätzlich gibt es zwei unterschiedliche Arten von Ransomware. Crypto-Ransomware verschlüsselt Dateien, sodass der User keinen Zugriff auf diese hat. Locker-Ransomware schließt den User aus seinem Computer aus, sodass dieser auf diesen nicht mehr zugreifen kann.
Zudem gibt es noch Untertypen dieser zwei Varianten. Scareware ist gefälschte Software, die auf dem PC Fehler und Probleme findet, die gar nicht existieren. Die Software verlangt Geld, um dieses Problem zu beheben. Scareware kann ebenfalls den Computer sperren (Locker-Ransomware).
Doxware oder auch Leakware genannt erpresst User mit angeblich gestohlenen Daten. Wer nicht bezahlt, dessen Daten werden veröffentlicht, droht Leakware.
Ein Beispiel für eine Ransomware Attacke – Emotet
Emotet ist eine der bekanntesten Ransomware-Variationen und schaffte es sogar in die tägliche mediale Berichterstattung. Unser Security Lab hat Emotet genauer unter die Lupe genommen und untersucht.
Gefahr von Ransomware für Unternehmen
Die Gefahr für Unternehmen durch Ransomware ist enorm groß. Wird ein privater Rechner durch Ransomware verschlüsselt ist dies zwar ärgerlich, in der Regel aber kein Grund für eine Insolvenz. Wird ein Unternehmensrechner infiziert, kann dies jedoch zur Unternehmenspleite führen. Häufig verbreitet sich die Ransomware im gesamten Netzwerk und infiziert alle Geräte, die sich in diesem Netzwerk befinden. Die Folge: ganze Unternehmen können nicht mehr arbeiten. Dateien gehen verloren, Arbeitszeit geht verloren, die Arbeit kann nicht fortgeführt werden. In einem 15-minütigen Beitrag erklärt unsere IT-Expertin Dr. Yvonne Bernard ausführlich, wie Ransomware wie Emotet ein Unternehmen auseinandernehmen und zerstören kann.
Welche Ransomware ist 2020 im Umlauf?
Es ist Anfang 2020 und die erste Ransomware-Welle ist bereits im vollen Gange. Die täglichen Berichterstattungen zu Greta Thunberg und Fridays for future machen sich nun auch Kriminelle zu Nutze. Diese versenden nämlich E-Mails im Namen der jungen Aktivistin. Das Hornetsecurity Security Lab hat E-Mails abgefangen, in denen Cyberkriminelle die Empfänger um Unterstützung bei einer großen Demonstration für den Klimaschutz bitten. Die Uhrzeit und die Adresse des globalen Streiks sind angeblich in der angehängten Datei zu finden. Sobald der Empfänger den Anhang öffnet, erscheint ein verschlüsseltes Dokument. Der Nutzer wird aufgefordert, die Bearbeitung und den Inhalt des Dokuments zu aktivieren. Folgt man dieser Anweisung wird ein Makro ausgeführt, das die schädliche Malware herunterlädt.

Ransomware Impact Report 2025
Ransomware-Angriffe nehmen zum ersten Mal seit drei Jahren wieder zu und festigen damit ihren Status als eine der hartnäckigsten Bedrohungen für Unternehmen im Jahr 2025.
Erfahren Sie, wie sich Unternehmen anpassen, welche Trends sich abzeichnen und wo neue Risiken entstehen.
Sollte man bei einem Ransomware Angriff das Lösegeld zahlen?
Nein, Experten und Ermittlungsbehörden raten davon ab, das Lösegeld zu bezahlen. Häufig werden die Daten trotz Zahlung nicht mehr entschlüsselt und der Computer ist weiterhin nicht zu benutzen. Deshalb sollten lieber Anti-Ransomware Lösungen genutzt werden und präventive Maßnahmen getroffen werden, damit das Zahlen von Lösegeld gar nicht erst zu einer Option wird.
Mehr über HORNETSECURITYS SERVICES
Interessiert an verwandten Themen?
Hat Ihnen unser Beitrag zum Thema Ransomware gefallen? Dann könnten Sie auch andere Artikel in unserer Wissensdatenbank interessieren! Wir helfen Ihnen dabei, mehr über Cybersicherheitsthemen wie Emotet, Trojaner, IT-Sicherheit, Cryptolocker-Ransomware, Phishing, Cyber Kill Chain und Computerwürmer zu erfahren.