A journey through the history of cryptography – Part 1
A never ending story? Data breaches at major companies dominate the headlines throughout the world’s newspapers. They have increasingly become a permanent topic in public reporting, but along with that, companies are also becoming more aware of the need to protect sensitive data from third-party access. The Ponemon Institute has observed a steady increase in the implementation of encryption strategies in companies over the past 14 years.
However, legal regulations, especially within Europe, force companies to use encryption. An important factor here is the General Data Protection Regulation (GDPR), which has been enforced since May of 2018. Personal data must be encrypted as soon as it is transmitted over the Internet or stored in the cloud, while encrypted communication was hardly considered at all a few years ago, it is currently “in vogue”.
It is important to note that encryption is not a modern invention. From a historical point of view, the beginnings date back for centuries of time, as we know the Roman commander Gaius Julius Caesar already exchanged encrypted messages with his military leaders. In this article, we will take a look back into the past to better understand today’s cryptography.
Before we enter our time machine, tighten our helmets and set off on a hunt for clues, we want to point out that side effects such as nausea, headaches and confusion can occur during this journey. We will attempt to provide the best possible service during your trip through the history of cryptography. Fasten your seat belts!
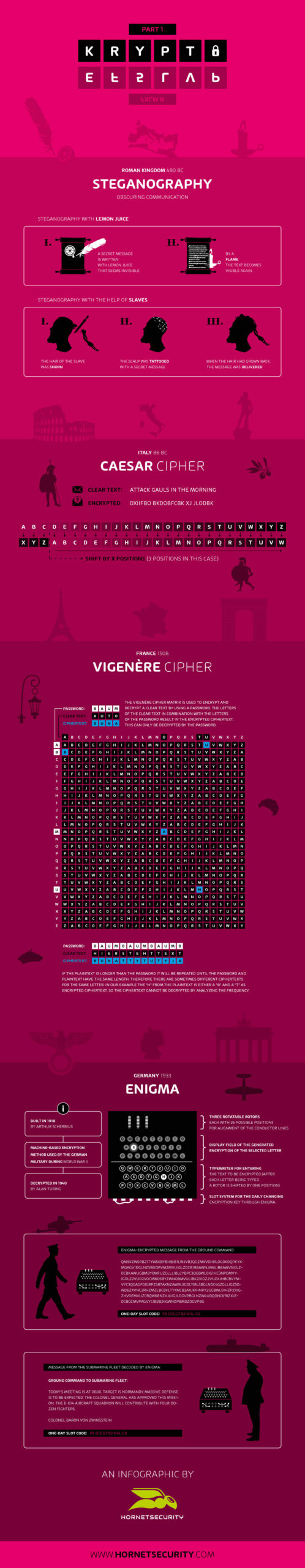
Historical cover-up – also known as: lemon juice on parchment
In the year 480, we are in the middle of the age of antiquity. Roman commanders compete for the rule of the Roman kingdom. Intrigues, murders and other fraudulent activities must be planned and executed. But how can such a planned assassination be transmitted to the contractor, undetected? Have you ever heard of lemon juice on parchment? It represents a classic secret communication channel.
The text is written on parchment using lemon juice. After the lemon juice has dried, the parchment gives the impression of a blank sheet. The recipient of the message can still decode the message very easily. For example, in those days he would hold a candle behind the parchment and thus be able to make the lemon juice visible and read the message.
In addition, there were several other methods that were used in antiquity. Slaves were used to shave the hair off their heads, tattoo the message on the back of their heads and wait for the hair to grow back to deliver the message to the rightful recipient. Without question, this was one of the more radical means of communication, and was not suitable for urgent messages either.
The procedures just described belong to steganography, which is clearly distinguishable from cryptography. Steganography is based on the hope that an outsider does not notice that two private parties are communicating with each other.
Beginnings of cryptography: Asterix and Obelix visiting Caesar
Opposite of steganography, cryptographic communication happens between two or more communication partners with language that may be visible, but remains confidential. Only the information itself is not visible to outsiders, through the encryption of the message.
Let us stay in Rome. Let’s immerse ourselves in the world of the Gauls and Romans.
A popular encryption technique was developed by a very well-known historical personality: Gaius Julius Caesar. Known today as the Caesar cipher, the later Roman emperor communicated with his military leaders through encrypted messages. Neither unauthorized persons nor the enemy, in this case the Gauls, knew the purpose of the coded texts. But as time passed, this encryption method could be cracked in quite a few simple ways.
The Caesar cipher is a simple symmetric encryption method, and is based on a substitution. This means that each letter used in the message is replaced by a new letter. The substituting letter results from a letter offset within the alphabet that is determined in advance. For example, a shift of three digits. In this case, “Thank you” becomes “Gdqnh”. For the decryption a cipher disk was often used to avoid having to constantly repeat the alphabet. With this type of encryption, the recipient only had to be informed in advance about the offset with a secret key.
An unauthorized person could not initially get anything out of the message without the key, but once he or she has spent some time on it, it is easy to decrypt the message after an average of 25 attempts. This is because they had to check the alphabet at a maximum of once to discover the correct letter offset. Today’s computers would take less than a second to do this. The Caesar cipher is therefore no longer considered secure and has been replaced by newer methods. All aboard, we’re off to France in the 16th century.
From Rome to France
One of the methods that replaced the Caesar cipher as a more secure alternative was the one developed by French diplomat and cryptographer Blaise de Vigenère in the 16th century, also known as the Vigenère cipher. It is comparable to the Caesar cipher, and is also based on the substitution of letters, but it uses several ciphertext alphabets.
How many alphabets are used, is determined by a key. Instead of a number, a keyword is chosen, which is written under the encrypted message. The keyword specifies the letter offset for each letter. The first letter of the keyword defines the alphabet for the first letter of the clear text, the second letter of the keyword determines the alphabet for the second letter of the clear text.
Example Vigenère Chiffre
Keyword: Present | Message: We give Tom a voucher for his birthday
W E G I V E T O M A V O U C H E R F O R H I S B I R T H D A Y
P R E S E N T P R E S E N T P R E S E N T P R E S E N T P R E
The “P” now gives a letter offset of sixteen letters, since the “P” is in the sixteenth position in the alphabet. The “R” shifts eighteen letters and so on. So the “WE” becomes a “MW”.
The safety of this encryption method is strongly related to the key length and whether the key is used multiple times. The keyword in our example is therefore not really secure.
However, some years later this encryption method turned out to be easily decoded. We will now take a look at another encryption method that was considered indecipherable for a long time.
Enigma and the Turing Machine
We make a stop in Germany in the 1930s. Similar to the Caesar cipher, encryption methods were mainly used in a military context. Therefore, it is hardly surprising that Germany also made use of encrypted communication during the Second World War. The special aspect of this type of encryption was that it was encrypted and decrypted by using a machine. The key was modified every day, so that it lost its validity after 24 hours. That machine is called Enigma.
Enigma was invented by Arthur Scherbius in 1918 as a special machine for routine cipher and decipher. The basic operating concept dated back to the years of the First World War. The First World War is considered the first war in which cryptography was systematically used. Already during the war and in the years after it, the first machines were developed which offered a significantly higher level of security than the manual methods. Enigma was offered for sale, but was met with very little interest from both the business community and government agencies. It was not until 1933, under Hitler, that Enigma became part of the standard equipment of the National Socialists. But how exactly does this odd machine work?
At first sight it resembles a classic typewriter, but inside it hides a rather complicated system. The operating principle is based on simple electric circuits, each of them connecting a letter key on the keypad to an electric light that illuminates a letter on the display. However, the “A” is not connected to the “A” on the display panel: all the rollers are interlocked according to a specific system. The message can therefore only be decoded if the recipient knows all the settings of the transmitting enigma.
Sounds like an insurmountable encryption, doesn’t it? But it was cracked by a British computer scientist in 1941. Alan Turing declared war on Enigma with a self-developed “Turing machine” and eventually won. Historians claim that this machine ended World War II prematurely and saved millions of lives.
Principle of modern cryptography
Before we now start our journey back to your offices, we would like to give you something to conclude:
As you have now learned at our various stations, even systems whose encryption algorithm was known only by the receiver and sender were able to be deciphered. One principle of modern cryptography, also known as Kerckhoff’s principle, therefore states that the reliability of a (symmetric) encryption method is based on the security of the key rather than on the secrecy of the algorithm. It is therefore advisable to use public algorithms that have already been sufficiently analyzed.
However, our journey into the history of cryptography is not over with this article, because one question remains open: Are there secure methods for encryption? To be continued …