Email Conversation Thread Hijacking
Summary
“You should only open email attachments and links from senders you know” is a common piece of advice when it comes to preventing email-based malware and phishing attacks. However, in this article we outline an attack technique called email conversation thread hijacking, which uses existing email conversations of its victims and thus trust relationships to spread to new victims. Against this attack the previous advice will not help. We explain how email conversation thread hijacking is used by attackers, and why it dramatically increases the likelihood for victims to open malicious links or malicious attachments.
Background
Malicious actors try to get victims to open malicious links or malicious attachments. To this end, they often mimic genuine emails, such as invoices. However, if a victim is not customer of a particular company or service they will likely not open invoices claiming to be from those companies or services, especially knowing that this is the most common scheme for malicious actors to lure victims into executing their malware. Malicious actors are thus also often using current events to spark an interest in victims to open their malicious links or malicious attachments. Examples of such events are Christmas, Black Friday, Halloween, Valentines Day, but also currently the SARS-CoV-2 pandemic. However, users are often also aware of these schemes and do not open any malicious links or malicious attachments, especially when they come out of the blue without any context.
Hence, more and more attackers are leveraging a technique called email conversation thread hijacking, also known as email reply chain attack or email thread hijacking. In this technique, an attacker uses existing email conversations of victims to spread to new victims. Previously attackers only used the email addresses listed in victims address books. Email conversation thread hijacking uses also victim’s past existing email conversation threads to spread to new victims. To this end, the attackers will reply to the conversations the victim has in his mailbox.
How does email conversation thread hijacking work?
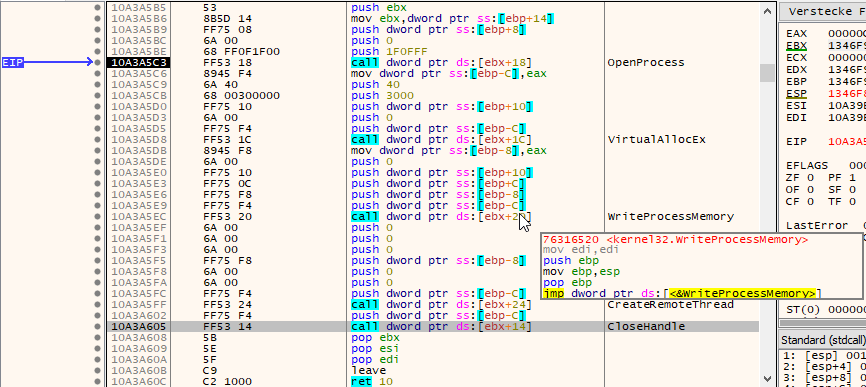
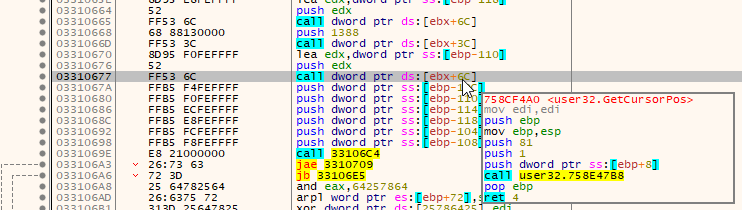
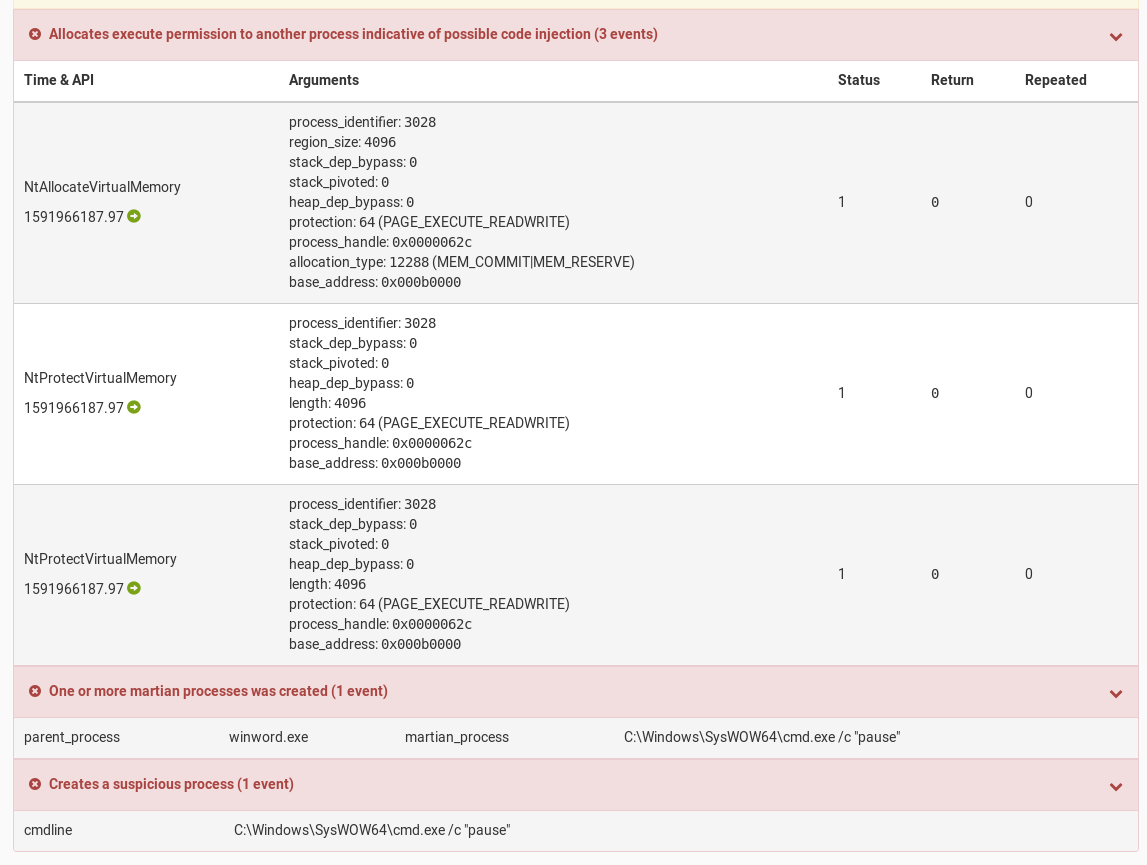
An email thread hijacking attack begins when a first victim is compromised. Next, their emails and often email login credentials are stolen. The attackers will then reply to the victim’s emails with their malicious messages.
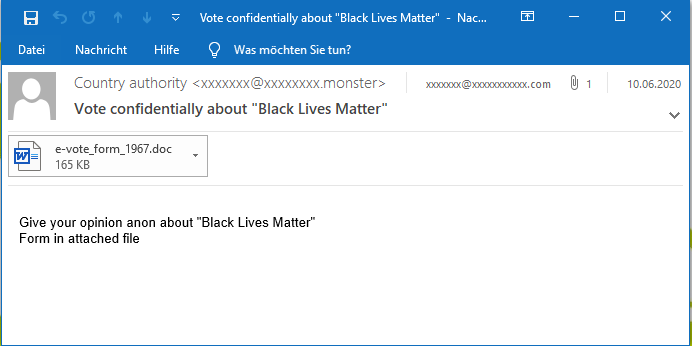
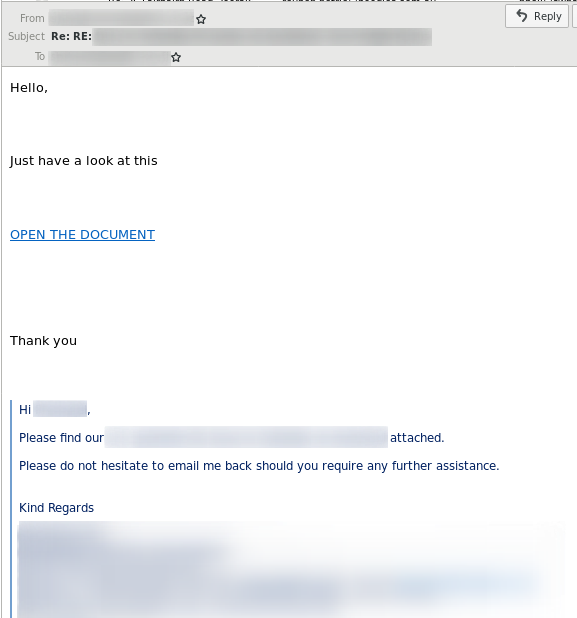
In the following example, the “From” field contains the victim’s email address. The “To” field contains the email address of the targeted user, with which the victim had an email conversation previously. The “Subject” contains the original subject of the email conversation but is prepended with a “Re: “. The quote below the message contains the entire email conversation the two parties had.
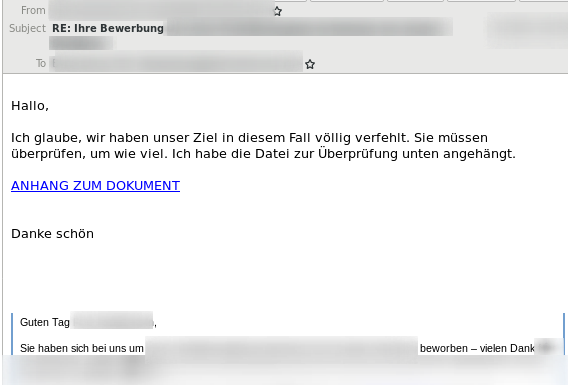
Good attackers also adapt the reply language to that of the hijacked email conversation, e.g., the following example uses a German language reply:
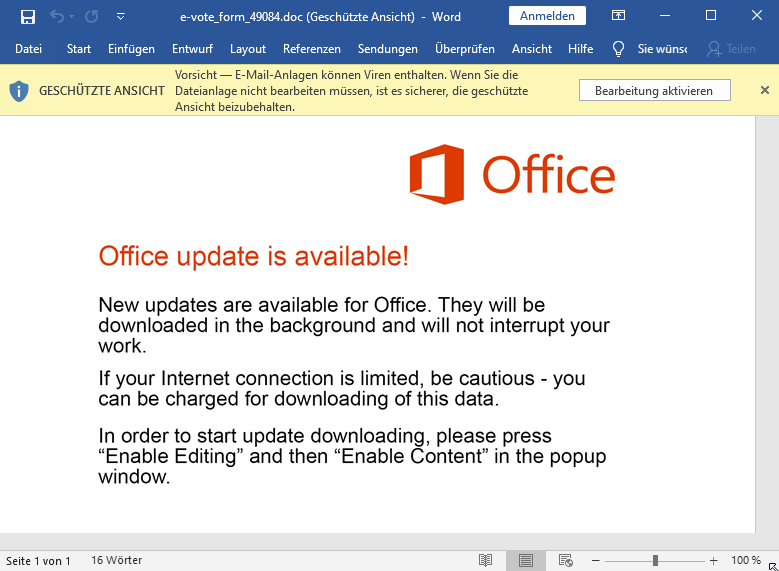
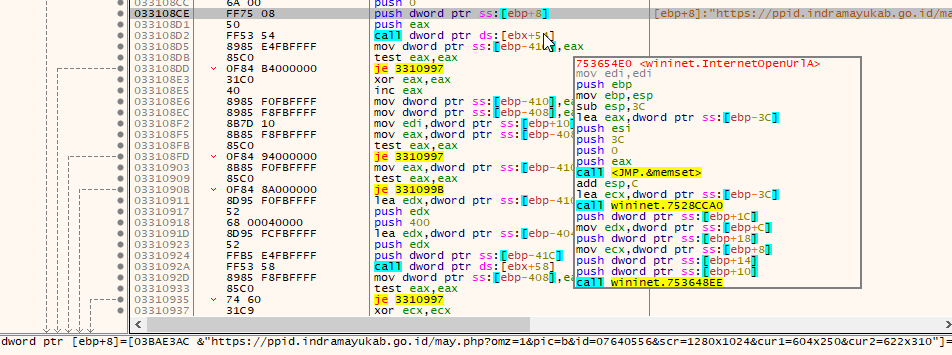
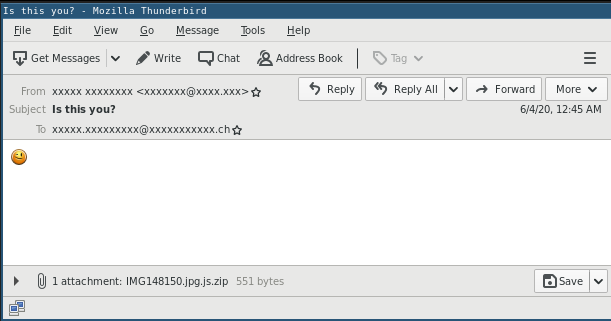
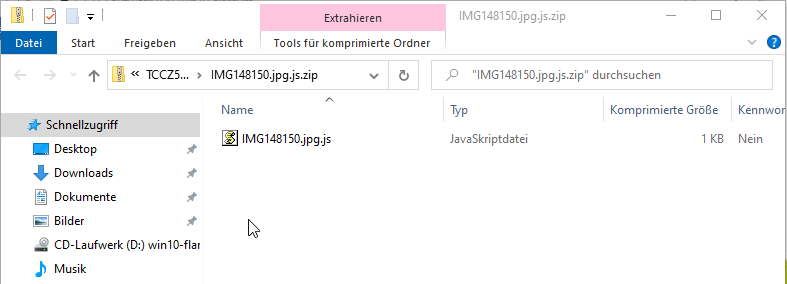
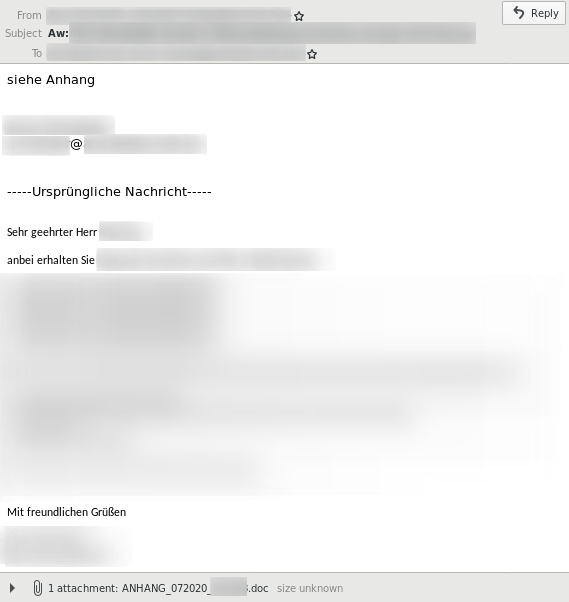
While in the previous examples the malicious reply email contained a malicious link, these emails can also use malicious attachments:
How effective is email conversation thread hijacking?
To demonstrate how effective email conversation thread hijacking is, we recreated a real email exchange that we observed during a routine false-positive email inspection:
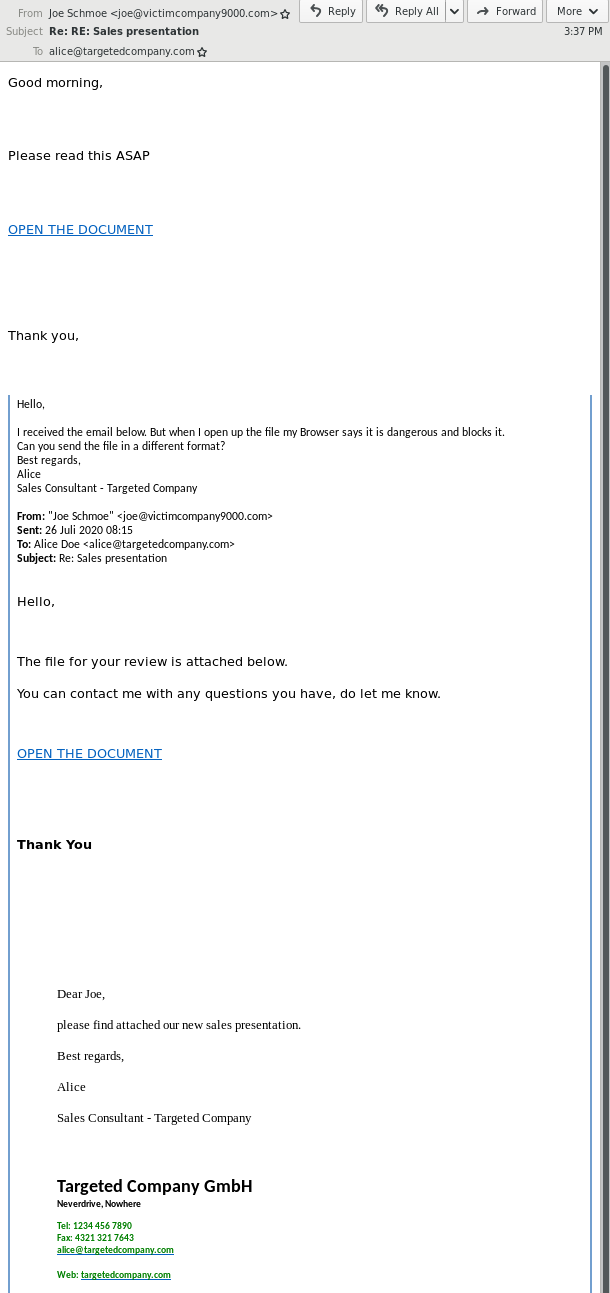
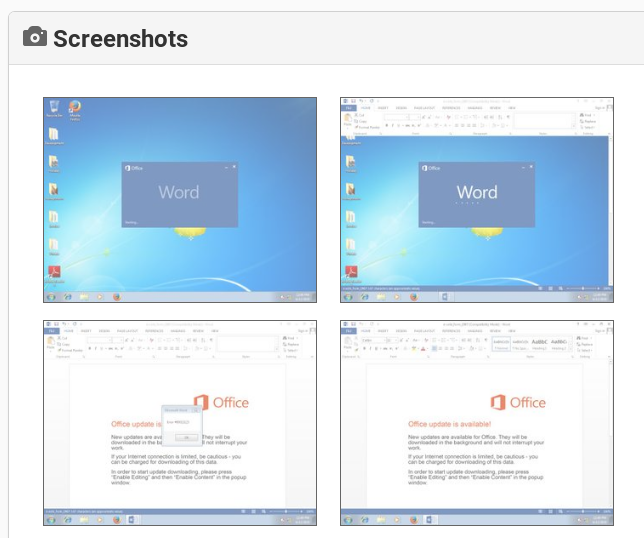
In this example, the attackers compromised Joe Schmoe’s email account and replied to an email that Joe has previously received from Alice. They replied with a malicious link (OPEN THE DOCUMENT) and some generic text. Alice released the email from quarantine and tried to open the malicious link, but her browser saved her from getting infected. She subsequently replied to Joe’s compromised email account that she can’t open “the file” and asked if “the file” could be sent in a different format. The attackers then send Alice another malicious link. While we are certain the attackers hijacking a previous hijacked email conversation thread again was coincidence, this example clearly shows how effective email conversation thread hijacking can be.
Fortunately, no attacker tailors their reply emails to fit into the hijacked conversation (yet). However, since threat actors have highly automated email conversation thread hijacking attack tools, the chances that the hijacked conversation involves documents that are shared back and forth is high. And even if it does not, who wouldn’t open a document sent by a known contact within an existing email conversation?
Who uses email conversation thread hijacking?
The number of threat actors using email reply chain attacks keeps increasing. While first observed in May 2017 in a limited targeted spearphishing campaign, many commodity threat actors adopted the technique in 2018.
In 2019, also Emotet adopted email conversation thread hijacking. To this end, they added an email-stealing module. The module steals emails and login credentials from victims and sends them to Emotet’s C2 servers, which distribute them to the systems of other victims infected with Emotet’s spam module, where they are used in attacks against new victims. Recently, Emotet has enhanced its email reply hijacking technique by also stealing attachments from victims and placing its malicious attachment among stolen benign attachments in order for the email to appear even more legitimate.
QakBot is also frequently distributed via replies to existing email conversation threads. In 2020, the Valek malware started to be distributed via email thread hijacking, too.
Hornetsecurity has observed an increase in compromised accounts being used to send malicious emails. While some do not (yet) use email conversation thread hijacking and simply misuse victims’ email accounts to send emails, with access to victims’ email accounts it is trivial to perform email reply chain attacks. A threat actor simply has to reply to emails received by his victims. We are therefore certain that the trend towards email thread hijacking attacks will continue. Therfore, users can no longer rely on a known trusted sender when deciding whether it is safe to open attachments or links.
Conclusion and Countermeasure
The advice to only open email attachments and links from known senders is outdated. With email conversation thread hijacking, even commodity threat actors can automate highly sophisticated and effective spearphishing emails. Often victims are not aware that they are compromised. In such cases it is important to inform victims that they are spreading malicious content via email so they can take measures against the compromise. Immediate actions should be to change the email login credentials. Secondary steps would be to determine how the attackers gained access to the email account in the first place to prevent such incidents in the future.
For humans it is very difficult, if not impossible, to spot email conversation threat hijacking because, by being sent from a legitimate but compromised account, the emails are – apart from the writing style – indistinguishable from real legitimate emails. However, email filters that inspect the attachments or links in emails can detect malicious content regardless.
Hornetsecurity’s Spam and Malware Protection, with the highest detection rates on the market, detects and quarantines threats regardless of whether they use email reply chain attacks or not. Also Hornetsecurity’s Advanced Threat Protection is not affected by email conversation thread hijacking and will inspect email contents regardless of whether it was sent from a compromised account or not. Hornetsecurity’s malware, phishing and ATP filters take precedence over sender allow lists. This way even if a allow-listed sender gets compromised and his email account is misused to send malicious emails, Hornetsecurity customers are protected.