Is Ransomware Data Recovery Impossible?
“I will find you and I will decrypt you”
Unfortunately, we can’t call up Liam Neeson if our data is encrypted via ransomware. Although he is a man with a particular set of skills, we do have to take proactive steps to ensure we can recover from ransomware.
What if you don’t have backups, is all hope lost?
How can we recover files from ransomware and what steps can we put in place to improve ransomware data recovery?
How Does a Ransomware Attack Typically Work?
There are several different entry methods for a ransomware attack, most of which involve malicious software. Ransomware encryption typically works by using a combination of symmetric and asymmetric encryption methods to lock and encrypt files.
Infection: The ransomware infects the victim’s system, often through phishing emails, malicious downloads, or exploiting vulnerabilities.
Key Generation: Once on the system, the ransomware generates a unique pair of keys for encryption: a public key and a private key. The public key is used to encrypt the files on the victim’s computer, while the private key is saved by the attacker.
File Encryption: The ransomware scans the system and network shares for files and encrypts them using the public key. This encryption is often strong and cannot be broken without the corresponding private key. The private key, which is needed to decrypt the files, is transferred and stored by the attacker.
Ransom Demand: The victim is presented with a ransom note via malicious software or through email demanding payment, usually in cryptocurrency, in exchange for the private key. If the victim pays the ransom, the attacker may provide the private key to decrypt the files.
It’s important to note that paying the ransom does not guarantee that the files will be decrypted or that the attacker will not demand more money. Additionally, ransomware can also include tactics to increase pressure on victims, such as threatening to publish the encrypted data or incrementally deleting files until the ransom is paid.
In most cases, it is best to contact your country’s federal cybercrime division or police department to assist with any ongoing investigations. In some cases, they have dedicated teams to help with ransomware data recovery and available ransomware recovery processes.
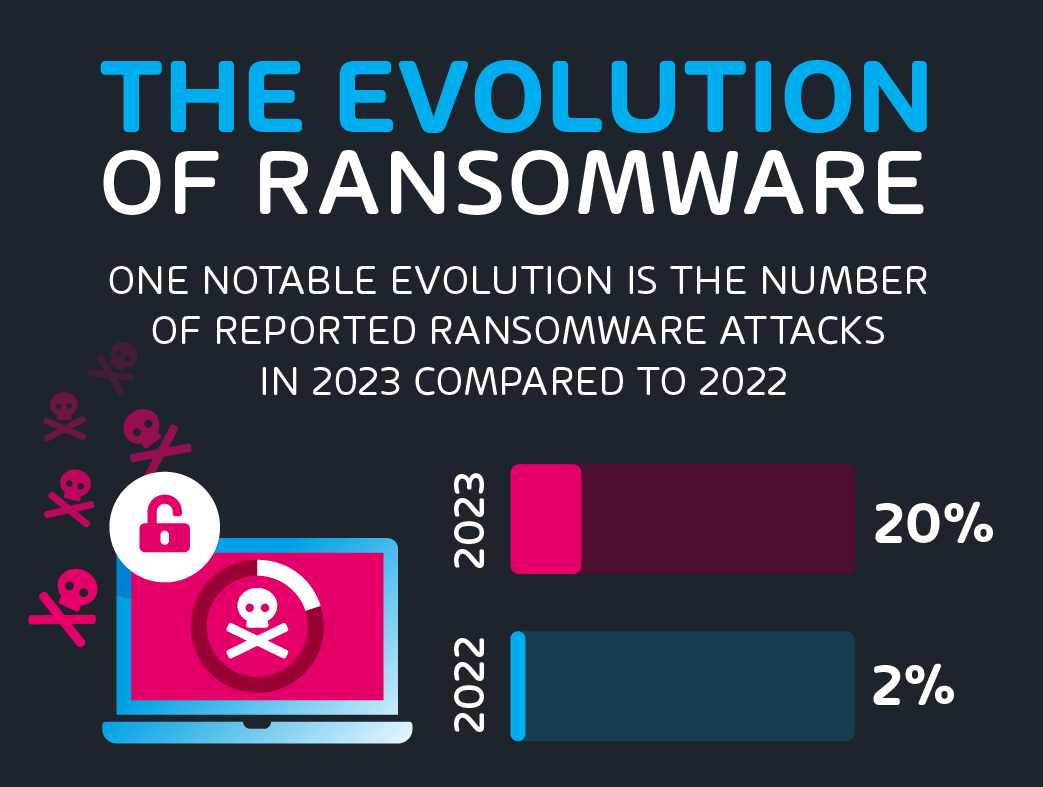
Response Strategies for a Ransomware Attack
When it comes to ransomware attacks, as with so many other business risks, planning ahead is vital. If you have a well thought out and practised Incident Response Plan, you’ll be more prepared and will respond to the attack in a more effective way if you implement the proper email security technology approach.
This can drastically improve ransomware data recovery time and reduce the risk of the ransomware spreading.
Record Important Details: Note down all known locations that have been encrypted along with the encryption extension. The ransom note or software can help identify the type of ransomware and in some cases, certain ransom keys have been broken or otherwise leaked online. This can greatly assist with ransomware data recovery.
Turn off the Infected Device: Ensure that the infected machine is disconnected from the network and shut down after you have recorded details. Removing the machine from the network is crucial to prevent the spread of infection or encryption.
Disconnect your Other Devices: Check your network to ensure that no other devices have been encrypted or infected. If any are identified, immediately disconnect them from the network.
Change Important Passwords: Ransomware can be known to locate and extract passwords stored on devices or in files. It’s very difficult to determine the scope of the attack so as a general recommendation all important passwords should be changed from a clean machine.
How Do You Report a Ransomware Attack?
It’s crucial to record all details about the attack, as they can be helpful for any professional assistance, insurance claims, legal claims, ransomware data recovery or informing authorities. Remember, paying the ransom does not guarantee the return of your data and may encourage further criminal activity. It’s best to consult with professionals and follow the reporting procedures outlined by your company and law enforcement agencies. This is because, in our ransomware surveys, we found that more than half of the business owners are concerned about the security of their critical data.

Techniques for Restoring Files After a Ransomware Attack
Several techniques can be leveraged for ransomware data recovery. Although we want to focus on proactive preventative measures, the steps below should be considered when looking to recover from an attack.
Implement an Incident Response Plan: As already mentioned, an effective response plan can be critical to ensuring that the blast radius of a ransomware attack is reduced, and the correct steps are followed to improve your chance of ransomware data recovery. The plan should include items such as: information collection, logging, communication internally/externally, legal requirements, investigation procedures, remediation steps and post-attack review.
Decryption Tools: Some ransomware encryption can be decrypted. This is why recording the ransomware information can be crucial. It’s best to reach out to a professional recovery team to help identify if your data can be decrypted without restoring from backup.
Restore from Backup: This can generally be the primary method of recovering files from ransomware. However, you must have good backup procedures in place before you need them. It is common for backups to become encrypted during a ransomware attack, therefore you need to ensure that your backup systems are isolated from production systems. If your backup storage is in the cloud, consider implementing immutable storage, which can’t be altered or deleted by anyone, including your own administrators. Regularly testing individual file, folder, Virtual Machine and system recovery is also important, as this will greatly assist in a crisis when the pressure is on to bring the business back to a working state quickly.
To properly protect your email technology environment from a potential ransomware attack, use Hornetsecurity’s hybrid approach email services such as:
To keep up with the latest articles and practices, visit our Hornetsecurity blog now.
Conclusion
The short answer to our question of “if ransomware data recovery is impossible” is no. There are a growing number of variants that can have their decryption keys applied but also good backup practices are the key to ensuring your data and business are protected.
FAQ
Is it possible to recover files from ransomware?
Yes, in most cases ransomware data recovery can be achieved if you have adequate backup systems in place, this isn’t usually a difficult task. If you do not have backups, then in some cases you can decrypt the data if the ransomware has been cracked by online communities.
What percentage of ransomware victims get their data back?
Excluding the victims who were able to restore their data from backup, according to a 2024 report from Sophos, approximately only 8% of victims who paid the ransom regained access to their data. This reinforces that paying for ransomware is usually not a good solution.
Is ransomware difficult to remove?
Typically, removing the ransomware software itself can be achieved by most Antivirus software but the decryption of data is where it becomes more difficult.
How long does it take to recover from ransomware?
This depends on a few factors. Do you have backups in place? Are they relevant and not encrypted? If you don’t have backups, are there decryption keys available for the variant?
In most cases, decryption takes as long as encrypting. Backup systems can take some time to restore depending on the amount of data encrypted but as a safe estimate allow at least 2-3 days of business downtime to recover. To sufficiently recover from ransomware proactive measures need to be in place.