Why You Still Need On-Prem Backup in The Cloud Era
Cloud technologies have fundamentally altered how we leverage computing resources. From software packages that require no maintenance by the customer to machine learning, the cloud gives us new ways to solve challenges.
Unfortunately, it also introduces new problems, sometimes as surprises. You might expect your cloud providers to automatically provide data protection, but they frequently offer only short-term solutions. Check your provider’s documentation carefully so that you understand what protections they do — and, most importantly, do not — offer.
Recently, cloud “disaster-recovery-as-a-solution” (DRaaS) offerings have appeared. They don’t have the same shock and excitement value as other cloud offerings, but they make up for that in convenience and perhaps cost. They also tend to lack the comprehensiveness of on-premises solutions.
Unprotected Cloud Resources
The Microsoft 365 packages provide subscribers with an impressive array of software and services. Its popularity makes it one of the most successful and widely used cloud products. However, it surprises some people to learn that Microsoft only includes minimal backup, spam, and malware protection.
Microsoft provides geographical redundancy to safeguard against disaster, they allow you to restore mailbox items for a few days after deletion (time varies by product and settings), and they can perform complete restores of mailboxes and SharePoint sites within a limited retention period.
So, they offer some protection, but nothing near what organizations accustomed to on-premises e-mail, file sharing, and SharePoint expect. For anything more, you need add-on solutions.
Hornetsecurity offers Microsoft 365 Backup to enhance backup coverage of your Outlook email and attachments, OneDrive, Teams and cloud-based SharePoint data. Hornetsecurity 365 Total Protection goes beyond that to provide protection against malware and spam. You have other choices in these markets, including some additional offerings from Microsoft.
Microsoft 365 stands out because of its popularity and the importance of the data entrusted to it, but most cloud products have the same lack of comprehensive protection. Consult with your providers to see what they offer, both as part of the product itself and as add-on or separate features.
Cloud Backup
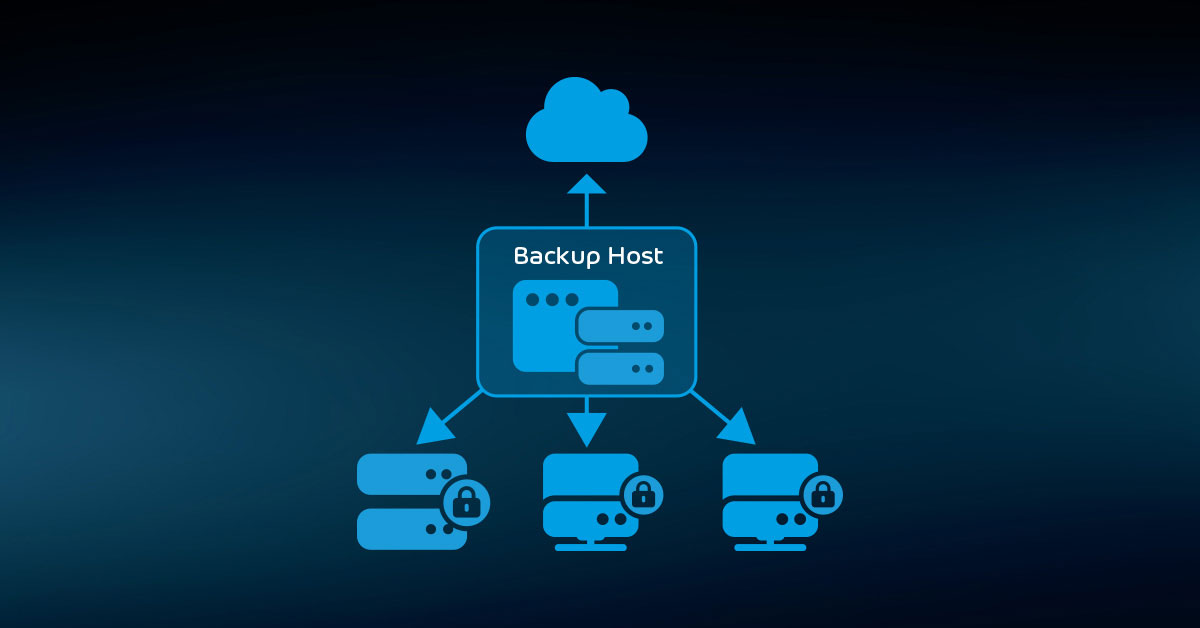
At the simplest, you can leverage your cloud account as a backup target. The cloud provider may offer some agent to run in your datacenter. More probably, you use a cloud-aware backup application, such as Hornetsecurity’s VM Backup, that automatically transfers on-premises backup data to the cloud.
A cloud backup strategy gives you the protection of offsite backup storage without the need to have your own secondary site. Your staff doesn’t need to travel anywhere to drop off or retrieve data. However, you still need to observe safe rotational practices.
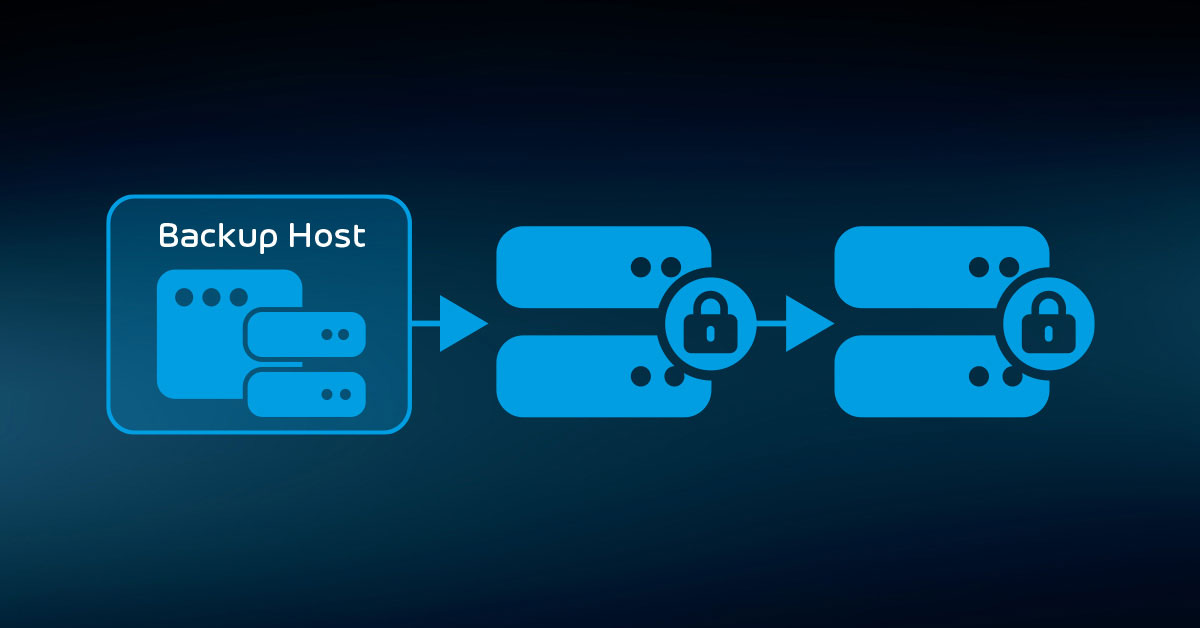
If your backup software can reach a particular location without human intervention, then so can any ransomware that hijacks the backup system. Cloud backup provides the best protection in conjunction with a standard offline rotation scheme.
For higher-tech solutions, you can consider establishing separate storage accounts and designing operations that limit access outside of expected backup windows. For instance, you might disable your backup system’s access to a dedicated “Monday” storage account all the other days of the week.
If you needed to restore the “Monday” data, you could manually override the access restriction. Such activities introduce risk and fragility into a critical function, however, and cannot guarantee to keep you safe from a ransomware assault. For the best results, use the cloud as a convenience target with standard offline storage as a failsafe.

Advanced Disaster Recovery Using Cloud Services
Using the cloud storage accounts described above, you can perform a restore operation by connecting your backup application to the account and running the same restore process that you would use with on-premises backup data. Other than data connectivity, this requires no special steps on your part.
However, the cloud provides alternative recovery options. With Azure Nested Virtualization, you could use your backup program to restore Hyper-V virtual machines directly into Azure. You would then need to do some work to enable connectivity, but your employees could use Azure as their datacenter.
If you don’t have the technology to directly restore a virtual machine right into Azure, but you like the idea of using Azure as an alternative datacenter, you have options. You could temporarily restore resources to a lower-powered system onsite, then transfer them into Azure’s SaaS and PaaS offerings. That works well for things like SQL Server and file serving.
It does take planning and time to execute but can provide substantial savings over building and operating your own secondary datacenter.
Some SaaS providers may offer enhanced services at a premium. They typically market such solutions as “DRaaS” (Disaster Recovery as a Service) or “BCaaS” (Business Continuity as a Service).
Features and pricing vary widely and change frequently, so you will need to research them and perform comparisons before deciding on anything. Such services will inevitably cost more than doing it yourself but should not cost as much as running an alternative site.
Keep in mind that “DRaaS” solutions frequently act more like replication technology than proper backup. For instance, Azure Site Recovery (ASR) allows you to mirror physical and virtual systems into Azure, where it may keep them or relay them to another of your facilities. However, it has no historical capabilities. Therefore, ASR can serve as a replication solution, but not as backup.
To properly protect your virtualization environment and all the data, use Hornetsecurity VM Backup to securely back up and replicate your virtual machine.
We ensure the security of your Microsoft 365 environment through our comprehensive 365 Total Protection Enterprise Backup and 365 Total Backup solutions.
For complete guidance, get our comprehensive Backup Bible, which serves as your indispensable resource containing invaluable information on backup and disaster recovery.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
Considering Cloud-Based Solutions
Someday, we might move to pure cloud-based options for backup and business continuity. We still have several problems to address before that can happen. For one, we do not have any foolproof ways to maintain an always-available data storage location in the cloud that can also provide adequate protection against ransomware.
Cloud backup and disaster recovery also presents the same challenge as every other cloud service: what do we do when we cannot access our cloud provider(s)? While it may seem archaic to keep your tapes and detachable hard drives around, only fully offline solutions provide any real guarantees.
For now, treat cloud-based backup and business continuity solutions as a convenience. Continue creating local copies that you can take completely offline and offsite.
FAQ
What is on-premise backup?
On-premise backup refers to creating and storing data backups on local hardware or servers within an organization’s physical premises. It is a traditional data protection method, ensuring that critical data is available and recoverable in case of data loss or system failures.
Which is the best backup solution?
Hornetsecurity offers a robust backup solution and is recognized as a leading provider on the market.
Does Microsoft have a backup solution?
The solutions offered by Microsoft are designed to help users protect their data and applications hosted on Microsoft platforms. However, choosing the most suitable backup solution should align with an organization’s requirements and preferences. On the other hand, Azure Backup provides a scalable, secure, and cost-efficient backup solution with the convenience of a one-click backup tailored to your storage requirements.