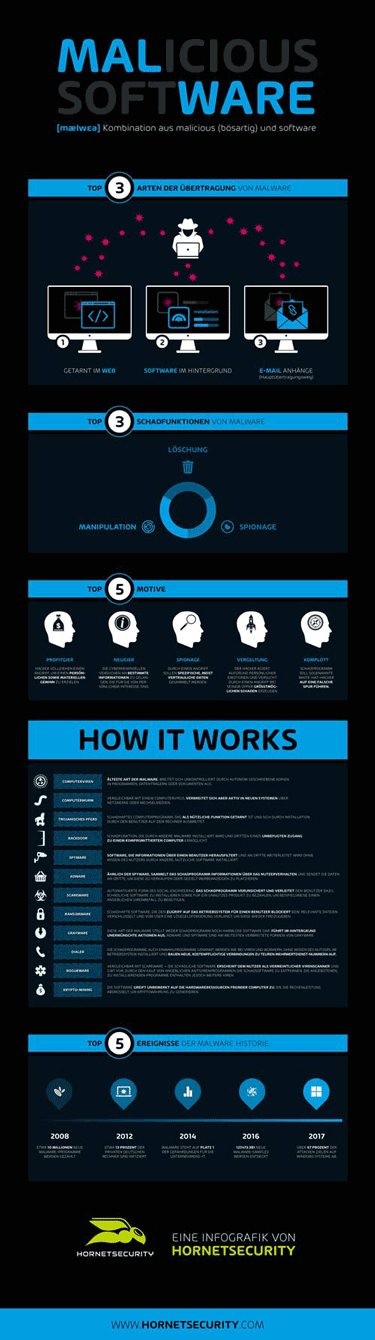
When the question is brought up as to what the term “malware“ is all about, most people do not understand what the term is about. Often words like “virus” or “Trojan” are used. This is not necessarily wrong, but also not actually right. After all, the topic is much more complex and is not just about viruses and Trojans.
More than just viruses and Trojans
“Malware” is a neologism composed of the two English words “malicious” and “software”. Mistakenly, malware is often used synonymously for the words virus or trojan, but the world of malware is much larger and more complex. In fact, malware is simply a collective term for various malicious programs, which in addition to viruses and Trojans also include “exploits”, “backdoors”, “spyware”, “worms” and “ransomware“ – to name just a few of the most important representatives.
Percentage of malware types
%
Trojans
%
Viruses
%
Scripts
Viruses, Trojans and worms – what are the differences?
Computer viruses are the classic type of malware and were already developed in the early 1970s. They are designed to infect other files and can spread from one computer system to another and contaminate it as well. Viruses cannot be activated without human intervention because the compromised file must be executed first.
A Trojan, on the other hand, is not a virus, but a malicious program that disguises itself as a good-natured application – which is why it is often referred to as a “Trojan horse”. Unlike viruses, Trojans do not replicate themselves. They allow hackers to take control of the infected system via a so-called “backdoor”.
Computer worm differ from viruses in their ability to spread without any intervention. By using a data interface, the malicious program can spread automatically. Since the worm can replicate itself within the system, there is a danger that not only one worm but hundreds or even thousands of copies will be sent. In the final instance, this can result in a system having to provide so many resources that no response or only extremely slow feedback occurs.
Spyware – The Spy in the System
spyware is considered the spy among malware types. It is out to record and steal entered user data. For example, it records logins in social media accounts or spies on account data during online banking. The captured data is then transferred to the hackers, who either resell it or misuse it for their own, mostly financial, interests.
Ransomware – When the computer demands ransom money
Ransomware is a form of malware that is able to prevent access to all data stored on a computer. The hackers encrypt the files stored on the hard disk and after a successful infection usually leave a message on the screen of the victim with the demand a ransom. If this doesn’t happen, it is threatened that the encrypted files – depending on the implementation of the Ransomware – will not be decrypted or even deleted.
There are plenty of ways to infect computers with ransomware. By far the most common gateway, however, is email communication. The cybercriminals often use social engineering to impersonate a well-known organization or a familiar person in order to suggest trust.
to impersonate a well-known organization or a familiar person in order to suggest trust.
In many cases, the Ransomware is contained in an Office document that is sent as an attachment. A pretext is used to persuade the recipient to open the file. In this case, all data on the hard disk is encrypted. Especially in recent years, there have been massive Ransomware attacks, known as „WannaCry“ or „Petya“. Even if Ransomware only appears rarely in the frequency of occurrence: The damage that can be caused by the aggressive cryptotrojans should never be underestimated! Measured in absolute figures, one percent of total malware worldwide is still a significant number.
Exploits and Backdoors – The ace up the sleeve
Exploits are a popular tool used by hackers to exploit vulnerabilities or security gaps in software and use them to enter computer systems. An exploit can be a simple theoretical description of a vulnerability or a directly runable program code.
The range of different types of exploits is so wide that there is the right exploit for almost every occasion. They differ not only in the type of attack, but also in their effects. Depending on its type, the malicious program can write or read data, for example, or even crash a system. Well-known exploit types are the zero-day attack and the denial of service exploit (DoS exploit).
Many types of malware, one solution?
The professionalism of malware attacks is increasing day by day. In particular, attacks through ransomware are very popular among cybercriminals. Those who think that there is THE solution to the problem of malware are unfortunately mistaken. Rather, a company should have a sophisticated security concept with many different measures. In the following we will describe in detail which measures can be considered.
Many components must work well together to achieve an optimum of protection against malware. However, the most important point is to increase the awareness of employees against cyber attacks. A company’s employees must be conscious of the threats caused by malware. Information about the various malware distribution channels should therefore be integrated into the daily work routine in regular training courses, for example.
To be on the safe side, companies are advised to use a spam filtering service to prevent malicious emails from reaching employees’ email inboxes in the first place. In the unlikely event that a malware program should ever be able to infect an employee’s computer, then an antivirus program is still a useful method of defeating the invader.
Also updates should not only be common for antivirus programs. It is advisable to establish a process that regularly reviews the actuality of the programs used, in order to update them if necessary. Those who stick to these tips are at least less likely to become a victim for cybercriminals.
Additional information:
-
- Blog post: Spam emails + infographic
- Blog Post: Successful Product CEO fraud + infographic
- Further information on the subject of cybercrime can now be found in the Hornetsecurity Knowledge Database.