Email Encryption
How to send a secure email with S/MIME and TLS
Certificates, signed emails, symmetric and asymmetric encryption, S/MIME, TLS and PGP – for many who do not regularly deal with email encryption these terms are quite foreign. However, with the new basic data protection regulations (GDPR) these terms have been pushed to the top of the to-do lists for many SMBs. Although, many companies lack the necessary knowledge to implement the new requirements in regards to the encryption of their email communication. In this article, Hornetsecurity aims to explain some of the basic terms and technologies around email encryption.
S/MIME and TLS – Transport and Content Encryption
With S/MIME, the content of an e-mail is encrypted. The prerequisite is that the sender and recipient each have a secret and a public key. Only the recipient has the appropriate key to be able to read the e-mail encrypted by the sender. TLS differs fundamentally from S/MIME. Here, not the content of the e-mail is encrypted, but the connection between the two communicating parties. TLS is therefore referred to as an encrypted tunnel. In this way it can be ruled out that outsiders can intercept the e-mail. Figuratively, the whole thing can be imagined as a letter in an envelope, whereas with S/MIME the text of the letter is encrypted as such. An unencrypted e-mail, on the other hand, is more like a postcard that can be read by anyone who gets their hands on it.
Email Encryption with Cloud Computing – the contemporary way
All roads lead to Rome – but which ones lead to legally compliant e-mail encryption? In fact, there are several ways for companies to implement this. The most prominent are on-premise and cloud solutions.
Email Encryption with On-Premise Solutions
With on-premise solutions, the encryption of emails takes place directly on site, i.e. at the companies themselves. The e-mail encryption software can be purchased from an external provider, rented or operated entirely by the company itself. Although this procedure offers the company a high degree of transparency and freedom of decision, it entails an administrative effort that should not be underestimated. Also the costs for maintenance and operation are not insignificant. Today, on-premise solutions are regarded as a phase-out model and are increasingly being superseded by modern cloud computing.
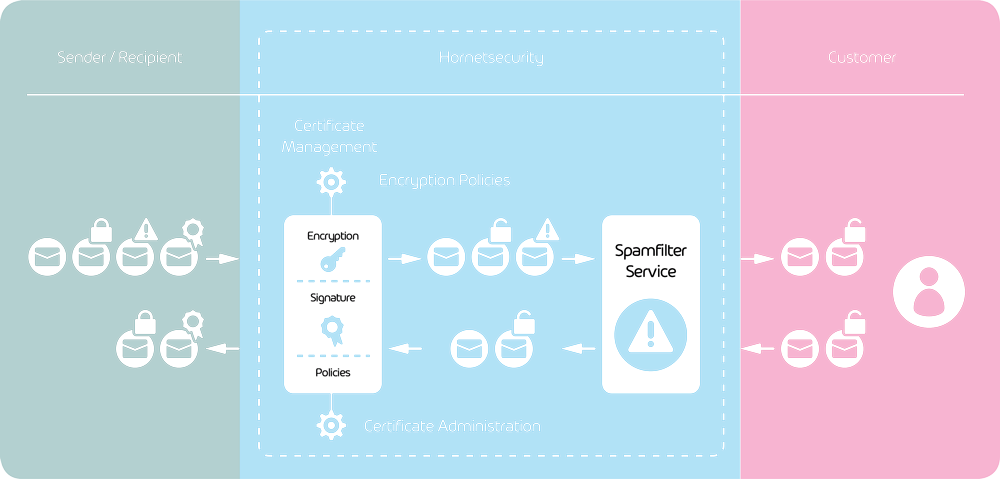
Email Encryption with Cloud Computing
With the cloud computing alternative, also known as the “SaaS” solution (Software as a Service), the security provider relieves the company of all administrative, administrative and operational tasks. The company’s entire e-mail traffic is then handled by the security provider’s servers, including Hornetsecurity’s e-mail encryption service.
The email encryption service from Hornetsecurity
Hornetsecurity’s email encryption service protects the email on its way via TLS, through an encrypted tunnel or encrypts the content of the message via S/MIME. If desired, S/MIME encrypted emails can also be transmitted through a TLS tunnel. S/MIME is increasingly being used between business communication partners who regularly exchange e-mails.
If the communication partner does not have an S/MIME certificate or in the rare case that TLS cannot be used there, Hornetsecurity offers the so-called “Websafe”. With the help of the Websafe, confidential e-mail communication can be carried out even if the recipient cannot actually receive encrypted e-mails. However, the use of the web safe should only take place in exceptional cases, since an additional password must be transmitted to the communication partner for this purpose. Of course, this password will not be sent by e-mail.
Conclusion: There is a suitable encryption method for every need
To communicate encrypted with private end users TLS is used almost exclusively. S/MIME is hardly used here at all. S/MIME is more often used between business communication partners, but TLS is also often used here. Hornetsecurity’s e-mail encryption service ensures that the right encryption method is chosen in the background, without the need for costly training of end users. This allows the employees of a company to devote themselves fully to their actual tasks.