ATP update – Introducing the new feature Malicious Document Decryption
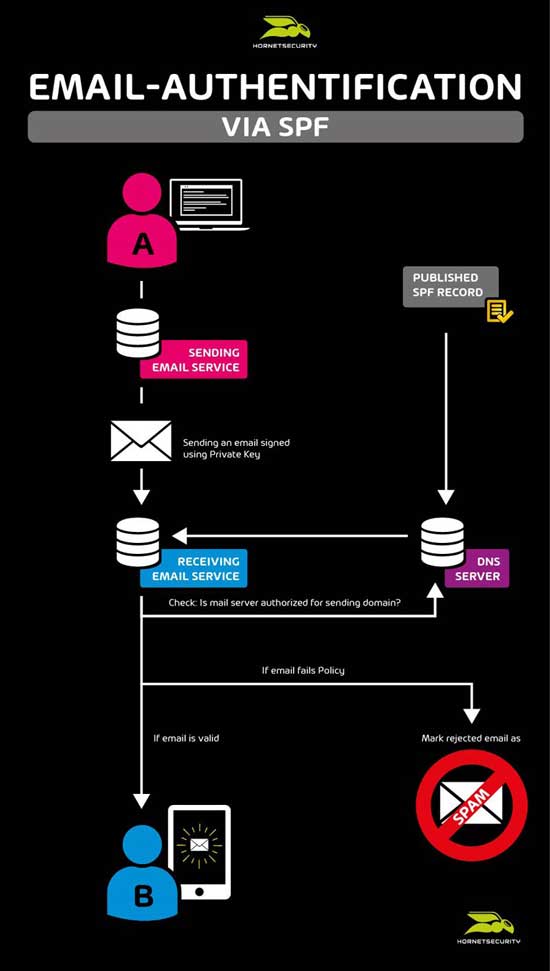
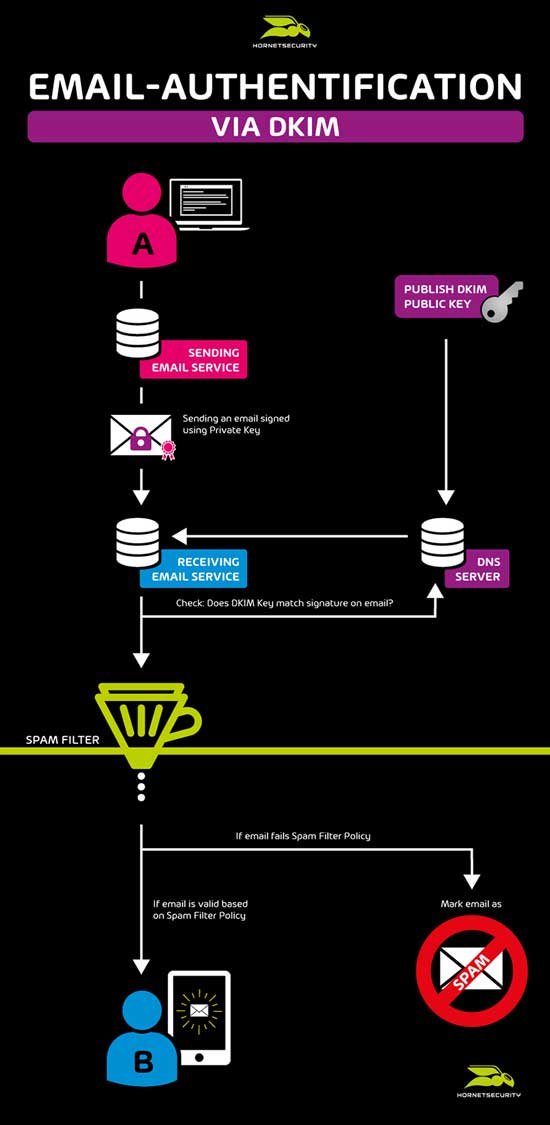
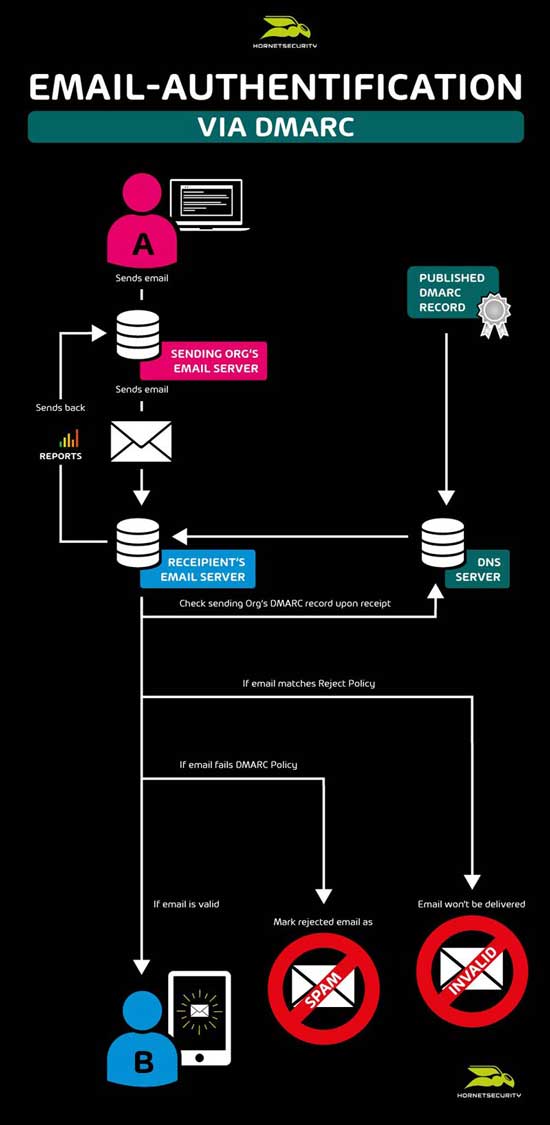
In order to spread ransomware, viruses or spyware into the systems of companies and organizations, cybercriminals are constantly developing new methods: Now they are focusing on a simple but very effective way, in which their distributed malware attached to an email can bypass antivirus scanning. The infected attached document is encrypted with a password, which prevents the filtering mechanisms of antivirus programs from detecting the hidden malware.
The current threat situation requires an update of the existing filtering mechanisms: “Malicious Document Decryption”fulfills these requirements perfectly.
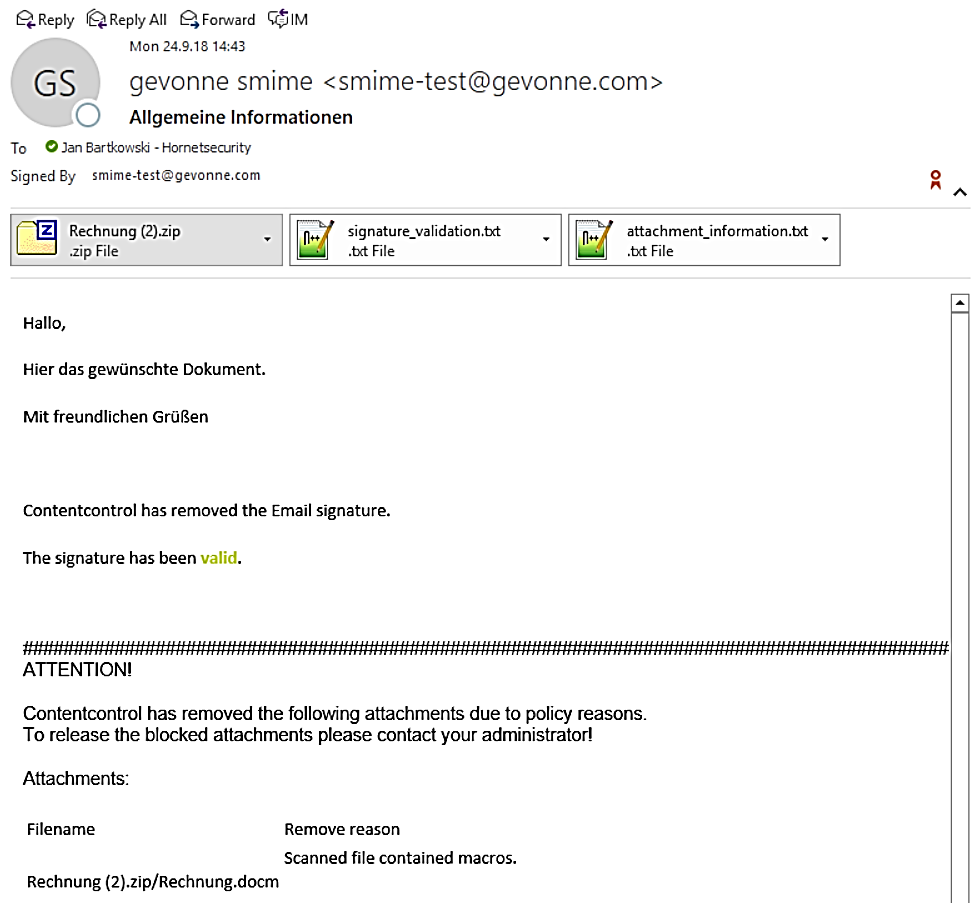
Just a few weeks ago, we reported about a “fake application mail” campaign that targeted HR departments in companies. This attack was performed by the ransomware GandCrab 5.2. The Hornetsecurity Security Lab still detects incoming malicious emails with encrypted and malware-infected attachments. The password for the decryption of the malicious file is visible to the recipient in the message of the email. However, decrypting the attachment downloads the hidden virus and infects the computer system.
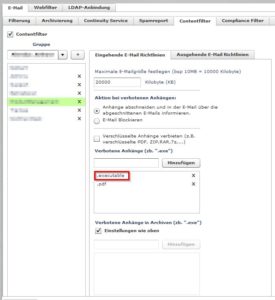
“Malicious Document Decryption” adds another elementary feature to Advanced Threat Protection to prevent the increasing threat of hidden malware. Emails with encrypted attachments are analyzed for their potential passwords within the email in order to decrypt the attachment in the sandbox. The file is then scanned using static and dynamic analysis methods and the behavior of the file is examined during execution. This makes it possible to detect malware in encrypted files and block the corresponding emails before they reach the recipient.
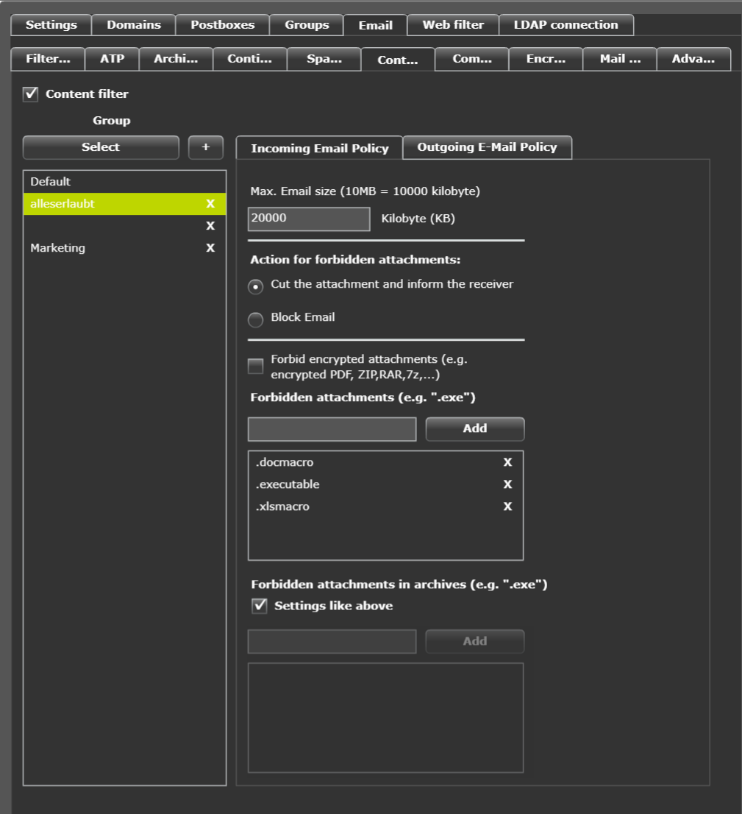
The “Malicious Document Decryption” feature decrypts all encrypted Microsoft Office file types and will be extended to decrypt PDF and archive files (RAR, ZIP, etc.).
Since the beginning of June, “Malicious Document Decryption” is included in the ATP service and already activated for all existing ATP customers..
More information:
- Service: Advanced Threat Protection