Coronavirus is also dangerous by email
Hornetsecurity warns of phishing and malware attacks that pretend to be from global health organizations
Reports of new cases of Coronavirus infection are appearing rapidly. The pictures of sealed-off cities and people in quarantine suggest a horrifying scenario. But the virus is not only a risk in the analogue world: the growing fear is shamelessly exploited by cyber criminals with targeted phishing and malware campaigns. Sadly, there is now a Coronavirus infection risk via email.
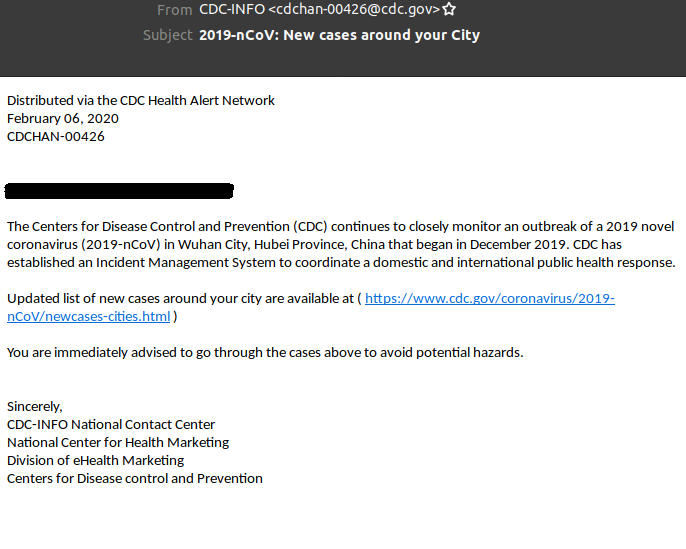
Since the beginning of February, the Hornetsecurity Security Lab has observed an increased volume of emails sent in the name of the World Health Organization and the Centers for Disease Control and Prevention. The messages explicitly take advantage of people’s fear of the virus.
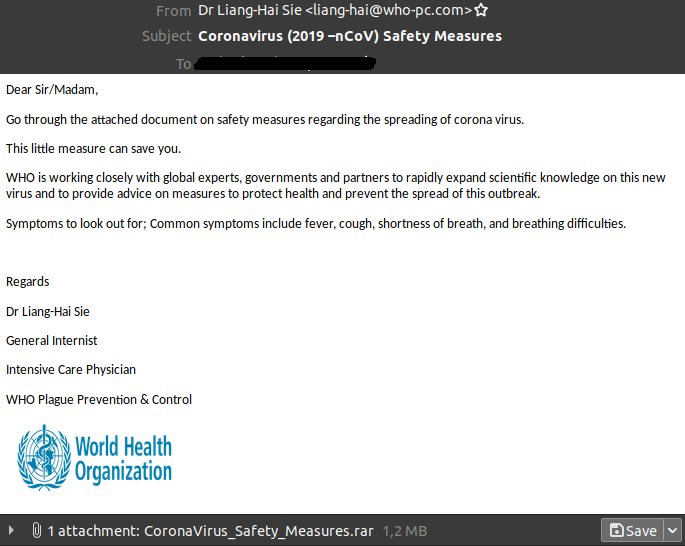
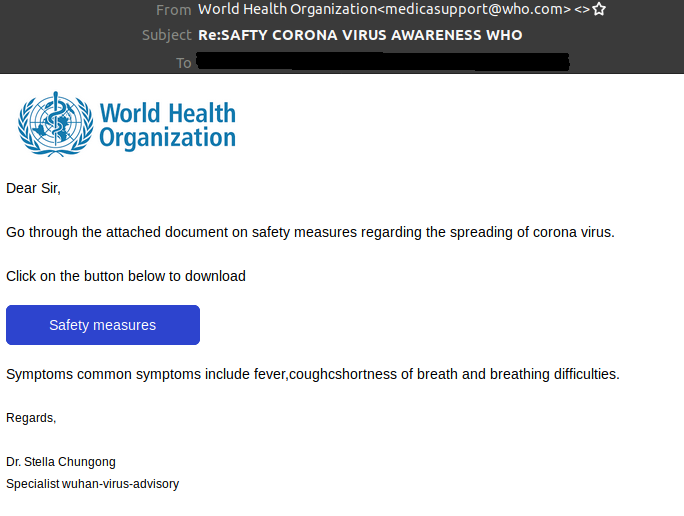
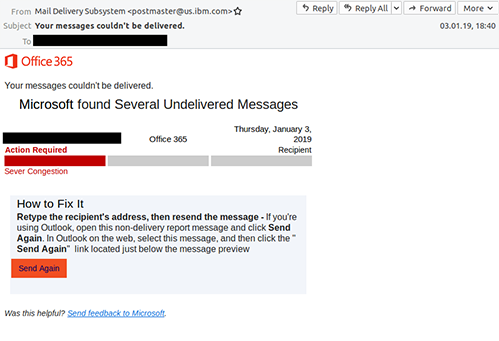
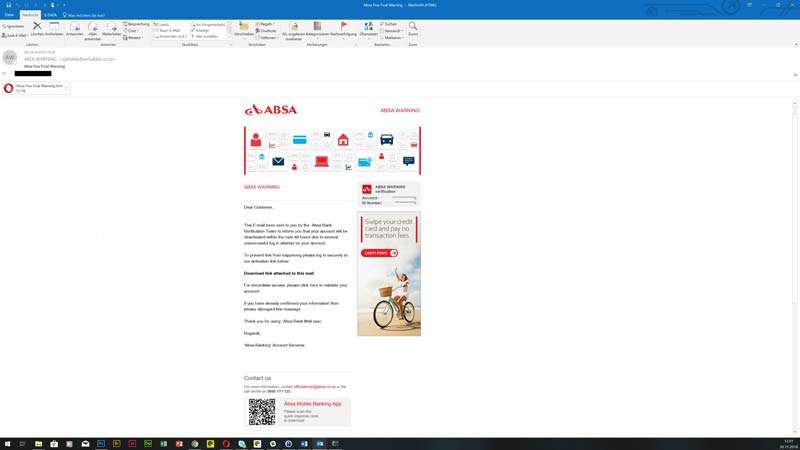
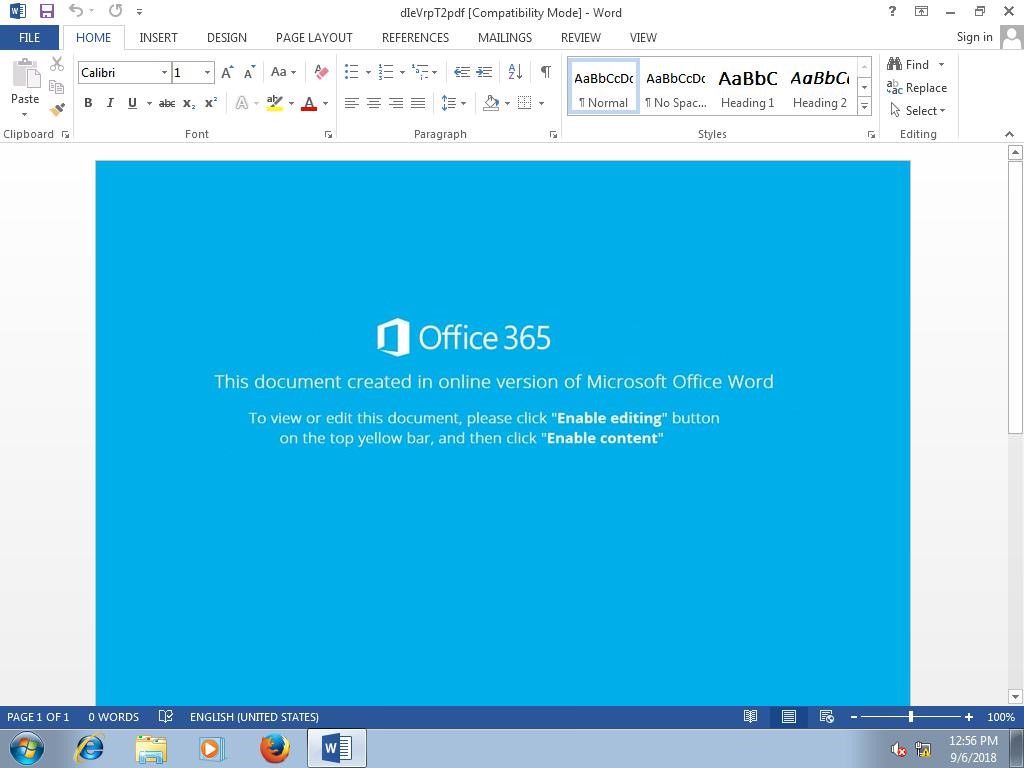
For example, a link provides an alleged list of new cases of infection in the immediate vicinity. The recipient would be able to access this list by entering an email address and a password. This is a classic phishing email that is intended to steal sensitive data. In other cases a download link or an attached document is offered. Both promise information on security measures to protect against infection.
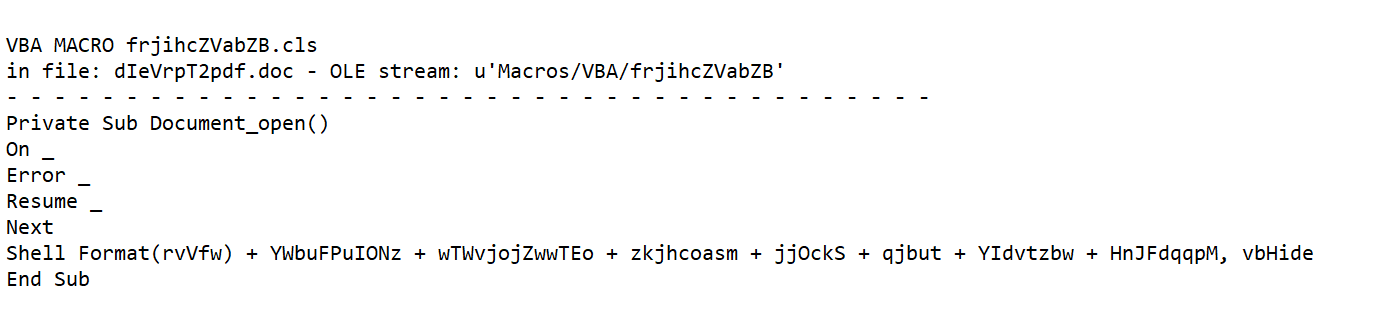
If the link is clicked or the document is opened, a malicious file will be downloaded. There is a substantial risk that the IT system could be infected with a virus or ransomware.
Increase in attacks that reference current events
The experts at Hornetsecurity point out that more and more often, current events with a high emotional charge are being used as hooks for large-scale phishing and malware campaigns. By exploiting people’s emotions, cyber criminals know their emails will receive more attention and be seen as more credible. The probability that the messages will be opened increases.
The Coronavirus mailing is only one of many current cases. There have been similar mail attacks referencing the climate protests initiated by Greta Thunberg, GDPR and the bush-fires in Australia—all of these are actual exploits that have been intercepted by Hornetsecurity.
Since email communication in companies is still the number one gateway for cyber attacks, employees must be made aware of this issue in addition to setting up effective protection mechanisms. Detecting phishing emails is not easy – but not impossible either. To vet suspicious messages, the following areas should be checked:
- The sender’s email address can provide information about the true origin of the message. If it is not plausible or contains spurious letters or cryptic symbols, this is a warning sign.
- Large-scale phishing campaigns often only use a generic form of address for the recipient.
- Incorrect spelling and grammar and an unprofessional layout are also an indication.
- The use of pressure is a common tactic. This is intended to undermine critical thinking.
- Cyber criminals often try to get the recipient to open a URL or attachment. Email attachments can present serious risks.